From Chaos to Control: Building Your Company's Access Management Foundation
Transform your company's digital security from chaos to control with a access management system. This comprehensive guide walks you through selecting the right tools, implementing core security measures, and creating efficient processes—all without overwhelming your team or budget.

In previous article, "The Hidden Costs of Poor Access Management", we explored how inadequate access controls can lead to devastating financial and reputational damage for small businesses. The average cost of a security breach—ranging from $120,000 to $1.24 million—makes it clear that proper access management isn't just an IT luxury; it's a business necessity. But how do you actually build a secure access management system without breaking the bank or overwhelming your team?
Imagine walking into a house where every door has a different key, some locks don't work, and you're not quite sure who has copies of which keys. Unfortunately, this scenario perfectly describes how many small businesses manage their digital access—a chaotic collection of passwords, permissions, and procedures that leave them vulnerable while making work needlessly complicated. As someone who has helped numerous small businesses establish their security foundations, I can tell you that building a proper access management system doesn't have to be overwhelming or expensive.
Understanding Your Access Management Needs
Before diving into specific tools and implementations, let's understand what your small business actually needs. Think of access management as the security system for your digital workplace. Just as you wouldn't install a bank-grade vault for a small retail shop, you don't need enterprise-level solutions for a small team. What you need is a system that's both secure and sensible for your size.
The Three Pillars of Basic Access Management
Your access management foundation rests on three essential components that work together to keep your business secure:
- Identity Provider (IdP) - Your Master Key System
Your IdP serves as the central authority for digital access, controlling who can reach your workspace resources. For small businesses, two solutions stand out for their balance of features and affordability:
Google Workspace (formerly G Suite):
- Best suited for: Teams that prioritize simplicity and collaboration
- Starting cost: $6 per user monthly
- Key advantages:
- Intuitive interface that reduces training needs
- Comprehensive mobile support for remote work
- Integrated collaboration tools that work seamlessly together
- Built-in security features that protect your business automatically
- Best suited for: Teams heavily invested in Windows and Office tools
- Starting cost: $6 per user monthly
- Key advantages:
- Familiar Office tools that require minimal training
- Strong integration with Windows environments
- Advanced security features included in business plans
- Comprehensive email and calendar solutions
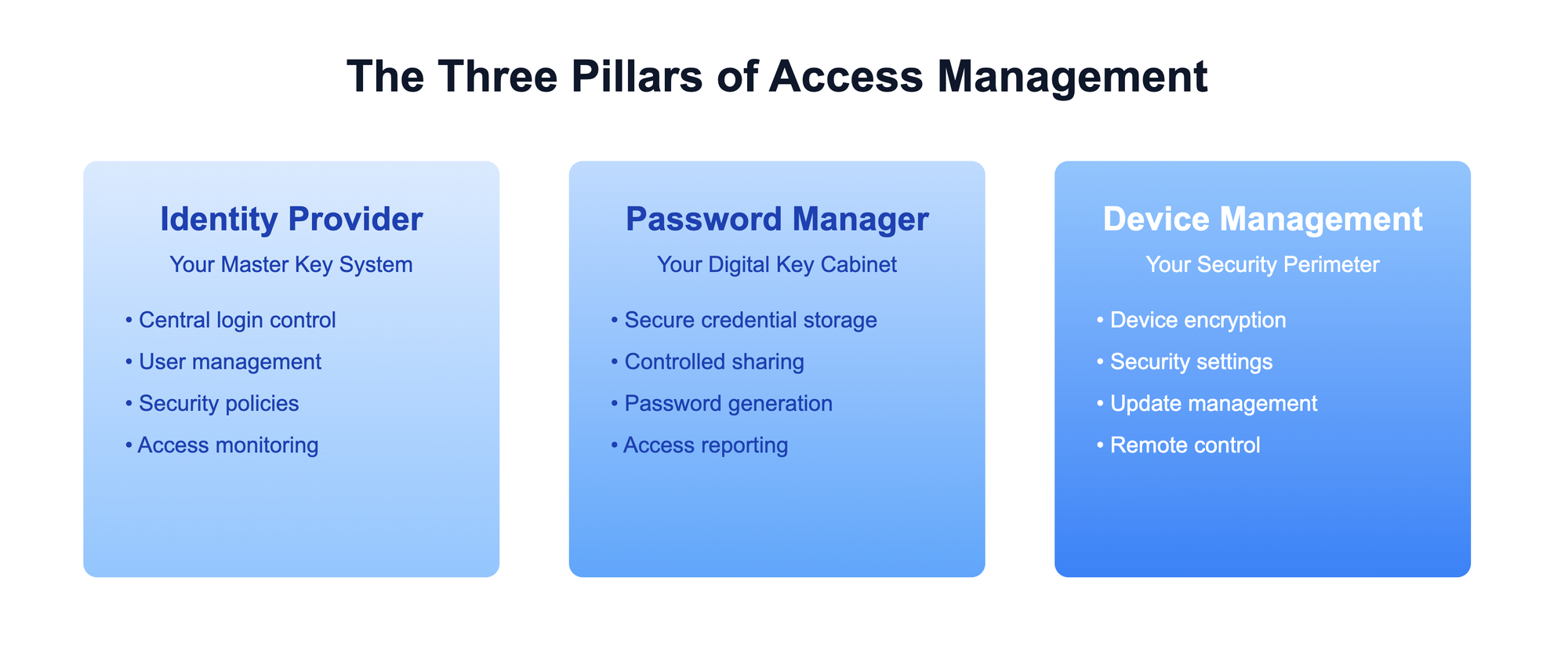
- Password Manager - Your Digital Key Cabinet
A password manager serves as your secure vault for all access credentials. For small teams, consider these options:
1Password for Business:
- Cost: $7.99 per user monthly
- Ideal for: Teams needing intuitive interfaces and robust sharing features
- Standout features:
- Simple and secure password sharing
- Detailed security reports
- Travel mode for secure international business
- Emergency access protocols
Bitwarden Teams:
- Cost: $3 per user monthly
- Ideal for: Cost-conscious teams comfortable with simpler interfaces
- Standout features:
- Open-source transparency
- Self-hosting capabilities
- Unlimited password collections
- Basic sharing features
- Device Management - Your Security Perimeter
Start with these fundamental device security measures:
- Enable built-in encryption tools (FileVault for Mac, BitLocker for Windows)
- Implement basic mobile device management through your IdP
- Deploy standard antivirus protection across all devices
Building Your Access Management System: A Step-by-Step Guide
Phase 1: Setting Up Your Identity Foundation
Start with your identity provider setup. Here's a detailed implementation plan using Google Workspace as an example:
Tasks:
- Visit workspace.google.com and select the Business Starter plan
- Verify your domain ownership or purchase a new domain
- Create your primary administrator account
- Set up your organization structure
Security Configuration:
- Access the Google Admin console
- Enable and configure these critical security settings:
- Require 2-Step Verification for all users
- Set minimum password length to 12 characters
- Enable suspicious activity alerts
- Configure basic mobile device management
Implementation Tip: Many businesses skip the security settings, planning to "do it later." This mistake often leads to security incidents. Complete your security configuration before adding any users to the system.
Phase 2: Implementing Password Security
With your identity foundation in place, establish your password management system:
Step 1: Initial Setup
- Create your business account with your chosen password manager
- Set up administrator access
- Configure security policies
Step 2: Organize Your Password Vaults
Create this structured vault hierarchy:
Company Vaults:
- Core Business (Administrative, Financial)
- Team Tools (Development, Marketing, Support)
- Emergency Access
Implementation Tip: Set up emergency access procedures immediately. This simple step can prevent business disruption if key personnel become unavailable.
Phase 3: Employee Access Management
Create a systematic process for managing employee access throughout their lifecycle with your company.
Pre-onboarding Checklist (1-2 Days Before):
- Create an Access Requirements Document (ARD) specifying:
- Employee details and role
- Required core system access
- Role-specific tool access
- Device requirements
- Security tool needs
Day One Setup Process:
- Core Access Setup
- Activate company email
- Configure password manager access
- Set up two-factor authentication
- Tool Access
- Grant specific tool access based on ARD
- Test all connections
- Verify permission levels
- Security Training
- Review security policies
- Provide password manager training
- Cover essential security practices
Avoiding Common Setup Mistakes
Learn from others' mistakes to build a more secure system:
The "We'll Fix It Later" Trap:
- Problem: Postponing security configurations
- Solution: Use our security checklist and complete it before adding users
- Prevention: Set up automated security checks
The Overprovisioning Error:
- Problem: Granting excessive admin access
- Solution: Follow the principle of least privilege
- Prevention: Document and justify each admin access grant
The Documentation Gap:
- Problem: Poor access record-keeping
- Solution: Maintain detailed access logs
- Prevention: Implement automated access tracking
Quick Security Wins (Implement These Today)
Even before completing your full access management system, implement these rapid improvements:
- Enable Two-Factor Authentication (15 minutes):
- Activate 2FA on all critical business accounts
- Set up backup authentication methods
- Document recovery procedures
- Create Basic Password Requirements (10 minutes):
- Set minimum password length to 12 characters
- Require special characters and numbers
- Prohibit password sharing
- Document Current Access (20 minutes):
- List all business tools and services
- Record who has access to each
- Note how access is currently granted
- Establish Emergency Procedures (10 minutes):
- Document key contact information
- Create backup access protocols
- Outline emergency response procedures
Moving Forward
Remember that effective access management is an ongoing process, not a one-time setup. Start with these foundational elements and build upon them as your business grows. Focus on getting the basics right—identity management, password security, and core procedures—before implementing more advanced features.
First Month Priority Timeline:
- Week 1: Identity provider setup and security configuration
- Week 2: Password manager implementation and vault organization
- Week 3: Documentation and template creation
- Week 4: Team training and process refinement
The key to success is starting with these basics and improving incrementally. Don't let perfect be the enemy of good—implementing these fundamental controls will already put you ahead of most small businesses in terms of security and efficiency.
This article is part of a comprehensive guide on access management for small businesses. Stay tuned for our upcoming ebook that will provide detailed implementation guides, templates, and best practices for securing your business effectively.

