The Small Business Guide to Everyday Access Management and Secure Off-boarding
Learn how to secure your company's digital assets in just 10 minutes a day. This practical guide shows small business owners and startup founders how to manage access, respond to security issues, and handle employee departures efficiently—all without disrupting daily operations.

In our previous articles, we explored the potentially devastating costs of poor access management and laid out the foundation for building a robust access management system. Now, let's focus on the day-to-day practices that keep your business secure. Think of this as your playbook for maintaining digital security without letting it consume your workday.
Daily Access Management: Creating Security Habits That Stick
Managing access to your company's digital resources is much like running a well-organized restaurant. Just as a restaurant manager needs to know who's handling food prep, managing the register, and serving customers, you need clear systems for managing digital access. The key is establishing routines that become as natural as locking your doors at night.
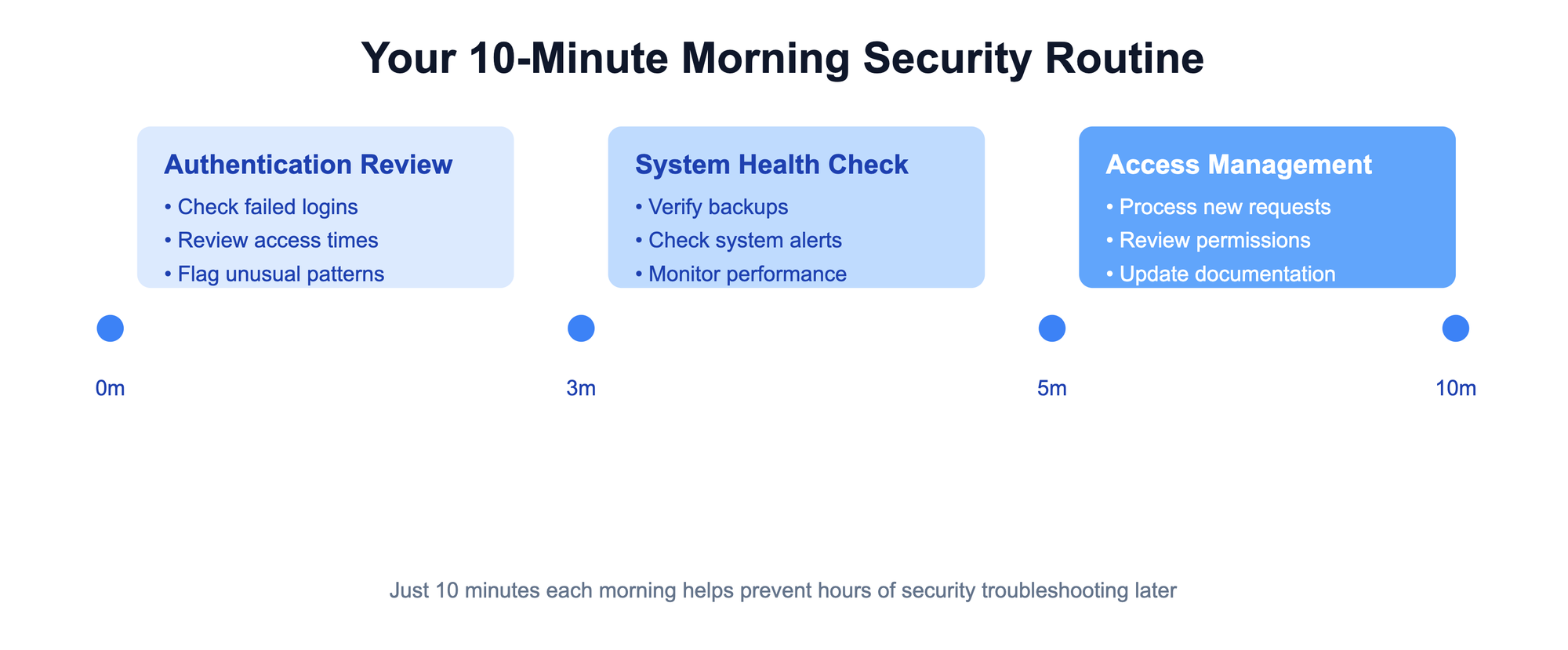
The 10-Minute Morning Security Routine
Start each workday with a quick but thorough security check. Think of it as your business's digital vital signs check – a structured way to spot potential issues before they become problems.
First 3 Minutes: Authentication Review
Begin by examining your authentication logs. You're not just looking at numbers; you're searching for patterns that might indicate security concerns. For example:
- Multiple failed login attempts followed by a successful login could suggest a breach
- Login attempts from unusual locations might indicate unauthorized access attempts
- Access patterns outside normal business hours could reveal compromised credentials
When reviewing these logs, think like a detective. A single failed login might be a typo, but five failed attempts from different countries should raise red flags.
Next 2 Minutes: System Health Check
Just as a doctor checks vital signs during a physical, your systems need regular health monitoring. Look for:
- Unusual CPU or memory usage that might indicate security issues
- Unexpected network traffic patterns that could suggest data exfiltration
- Backup system status to ensure your safety net is functional
- Security tool updates or warnings that need attention
Don't just confirm systems are running – verify they're running correctly. A system running at 100% CPU at 3 AM might be doing important work, or it might be mining cryptocurrency for an attacker.
Final 5 Minutes: Access Request Management
Process access requests with a security-first mindset. For each request, consider:
- Does this person truly need this level of access to perform their role?
- Could a more limited permission set accomplish the same goal?
- Are there any risks associated with granting this access?
- How will we monitor and review this access going forward?
Remember, every access grant is a potential security risk. The goal is to provide enough access for people to do their jobs effectively while minimizing potential vulnerabilities.
Responding to Access Issues: The 3-Minute Protocol
When access issues arise, you need a response that's both quick and secure. Here's how to handle common access problems efficiently:
Minute 1: Verification
Start with thorough verification, but make it efficient:
- Confirm the requester's identity through established channels
- Verify their authorization level for the requested access
- Check if the request aligns with their role and responsibilities
Think of this like checking ID at a secure facility – it might take a moment, but it's essential for security.
Minute 2: Implementation
Execute the necessary changes with precision:
- Make the required access adjustments
- Document the changes in your system
- Set any necessary time limits or review dates
Minute 3: Confirmation and Documentation
Wrap up the process professionally:
- Confirm the changes work as intended
- Notify relevant team members
- Update your access management records
Secure Offboarding: Protecting Your Business When Employees Leave
Employee departures represent one of the most significant security risks for small businesses. Consider this scenario: A marketing agency discovered a former employee still had access to their client presentation files three months after leaving. This wasn't malicious – it was simply overlooked in a rushed offboarding process.
Understanding the Scope of Modern Access
Today's employees typically have access to dozens of systems:
Let's understand how deep this access typically goes. A modern employee might have their digital fingerprints across:
- Email and communication platforms where they've exchanged sensitive information
- Project management tools containing strategic plans and timelines
- Cloud storage services holding company documents
- Social media accounts representing your brand
- (CRM) Customer relationship management systems with valuable client data
- Financial software with sensitive transaction records
- Development and deployment tools containing intellectual property
Each of these access points needs careful attention during offboarding. Think of it like collecting keys from a departing property manager – you need to know about every lock they had access to.
The Two-Week Offboarding Process
When you have advance notice of an employee's departure, follow this comprehensive process:
Week 1: Documentation and Knowledge Transfer
Days 1-2: Complete Access Mapping
- Document every system the employee has access to
- List all projects and responsibilities
- Identify critical knowledge that needs to be transferred
Days 3-5: Knowledge Preservation
- Schedule detailed handover meetings
- Document unique processes and procedures
- Update team documentation
- Ensure critical information isn't lost
Week 2: Access Management and Security
Days 6-8: Gradual Access Reduction
- Remove unnecessary access rights
- Monitor activity for any concerns
- Transfer ownership of shared accounts
- Begin archiving important communications
Days 9-10: Final Preparations
- Complete the offboarding checklist
- Conduct exit interviews
- Prepare for final account termination
- Document any remaining tasks or responsibilities
Emergency Offboarding: The 15-Minute Protocol
Sometimes you don't have the luxury of a two-week notice. Here's your rapid response plan:
First 5 Minutes: Critical System Protection
- Disable primary account access
- Revoke VPN and remote access capabilities
- Lock access to cloud services and sensitive data
- Reset critical shared passwords
Next 5 Minutes: Communication Systems
- Remove email access and set up forwards
- Disable chat and collaboration tool access
- Remove from project management systems
Final 5 Minutes: Documentation and Notification
- Document all actions taken
- Notify relevant team members
- Begin comprehensive access audit
Building Security into Your Daily Operations
The key to effective access management is making it part of your regular business rhythm. Here are five essential habits to develop:
1. Weekly Access Reviews
Every Friday, spend 15 minutes reviewing:
- Active user accounts and their current access levels
- Temporary access that should be revoked
- Unused licenses that could be reallocated
- Any unusual patterns in system access logs
2. Monthly Security Assessments
Once a month, conduct a deeper review:
- Evaluate access patterns across all systems
- Update documentation of security procedures
- Review and adjust access policies as needed
- Check for any unnecessary standing permissions
3. Quarterly Permission Audits
Every three months, perform a comprehensive audit:
- Review all user access rights
- Clean up outdated permissions
- Update security documentation
- Assess the effectiveness of current procedures
4. Continuous Training and Awareness
Make security awareness an ongoing process:
- Share monthly security tips with your team
- Review recent security incidents and lessons learned
- Update team members on new security procedures
- Encourage reporting of security concerns
Practical Implementation Steps
Start implementing these practices today:
- Create Your Access Inventory
- Map out all your systems and who has access
- Document current permission levels
- Identify system owners and administrators
- Note any temporary or special access arrangements
- Establish Basic Procedures
- Create standard forms for access requests
- Document your emergency response procedures
- Set up regular review schedules
- Develop your offboarding checklist
- Set Up Monitoring Systems
- Enable logging on all critical systems
- Configure basic security alerts
- Document your review process
- Create response procedures for common issues
Conclusion
Effective access management doesn't require complex systems or constant attention. By establishing clear procedures and maintaining consistent habits, you can protect your business while keeping operations smooth and efficient. Start with these fundamentals and gradually improve your processes as your company grows.
Remember: Security isn't about having the most sophisticated tools – it's about consistently following simple, effective practices that protect your business assets.
This article is part of a comprehensive guide on access management for small businesses. Stay tuned for our upcoming ebook that will provide detailed implementation guides, templates, and best practices for securing your business effectively.

