The Future of Search Marketing: Beyond Google's Horizon
As traditional search marketing evolves, cybersecurity companies must embrace a new paradigm that combines AI-driven discovery, interactive tools, and secure platforms. Learn how to leverage multi-platform presence, intent-based search and practical tools to create lasting ties with security firms.

As we stand at the intersection of artificial intelligence, cybersecurity, and digital marketing, a revolutionary transformation is reshaping how businesses connect with their audiences. Traditional search marketing, centered around Google's algorithm and keyword optimization, is giving way to a more sophisticated, multi-faceted approach that prioritizes practical value and interactive experiences. This evolution is particularly significant in the cybersecurity sector, where complex solutions and high-stakes decisions require more than just informational content.
The Evolution of Search Behavior: Deep Dive
The way people search for solutions has fundamentally changed. Today's B2B buyers, especially in technical fields like cybersecurity, engage in a complex discovery process that spans multiple platforms and formats. Understanding these changes is crucial for developing effective marketing strategies.
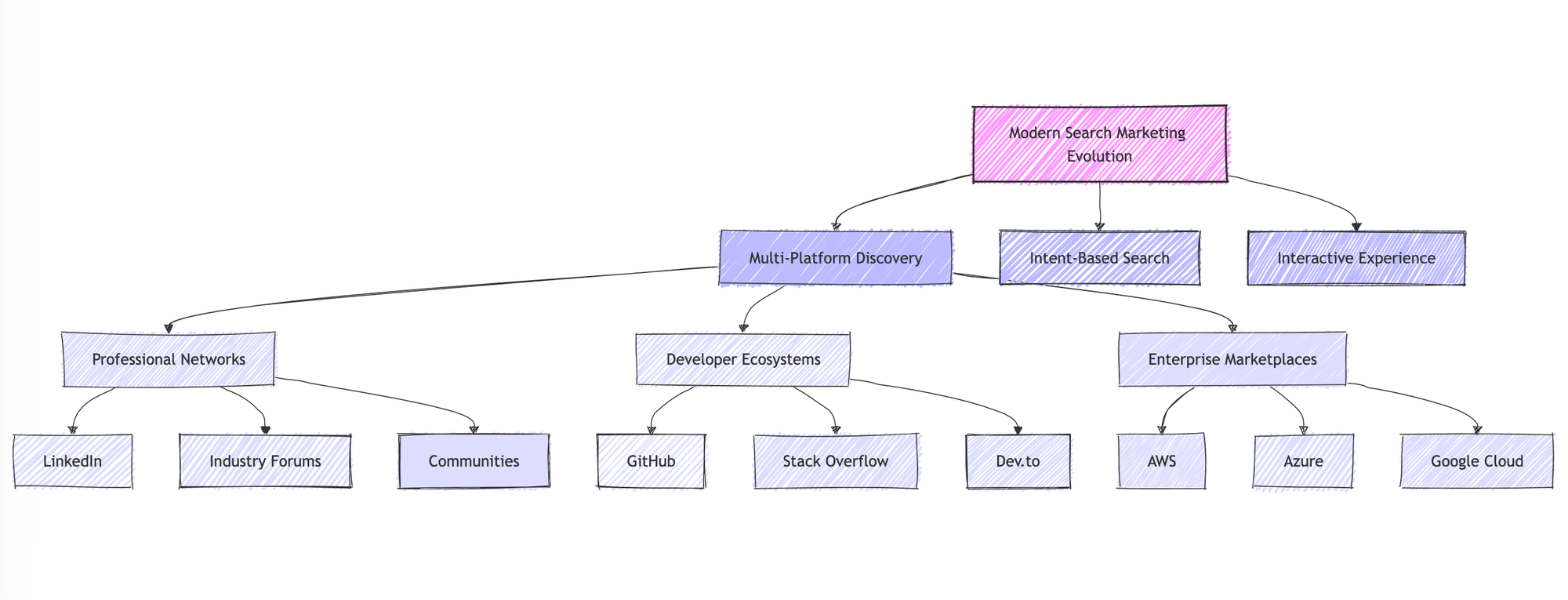
1. Multi-Platform Discovery
Modern B2B buyers no longer rely on a single search engine. Instead, they conduct parallel searches across various platforms, each serving a specific purpose in their decision-making journey:
Professional Networks
- LinkedIn: Technical decision-maker discussions and peer recommendations
- Industry Forums: Deep technical discussions and real-world implementation experiences
- Specialized Communities: Sector-specific challenges and solutions
Developer Ecosystems
- GitHub: Open-source security tools and implementation examples
- Stack Overflow: Technical implementation challenges and solutions
- Dev.to: Security development practices and tools
Enterprise Marketplaces
- AWS Marketplace: Cloud security solutions with immediate deployment options
- Azure Marketplace: Integrated security tools with cloud infrastructure
- Google Cloud Marketplace: Security tools with cloud-native integration
2. Intent-Based Search
The shift from keyword-based to intent-driven searches represents a fundamental change in how users interact with search platforms:
Traditional vs. Modern Queries
- Old: "endpoint security software"
- New: "how to protect remote workforce endpoints in financial services"
Solution Discovery Process
- Problem Definition: "preventing ransomware in healthcare"
- Implementation Planning: "ransomware protection implementation steps"
- Validation: "ransomware protection case studies healthcare"
3. Interactive Search Experience
Users now expect search results to provide immediate, actionable value:
Dynamic Content Engagement
- Interactive Documentation: Click-through tutorials and guides
- Live Demonstrations: Real-time product functionality showcase
- Configurable Solutions: Customizable feature sets and pricing
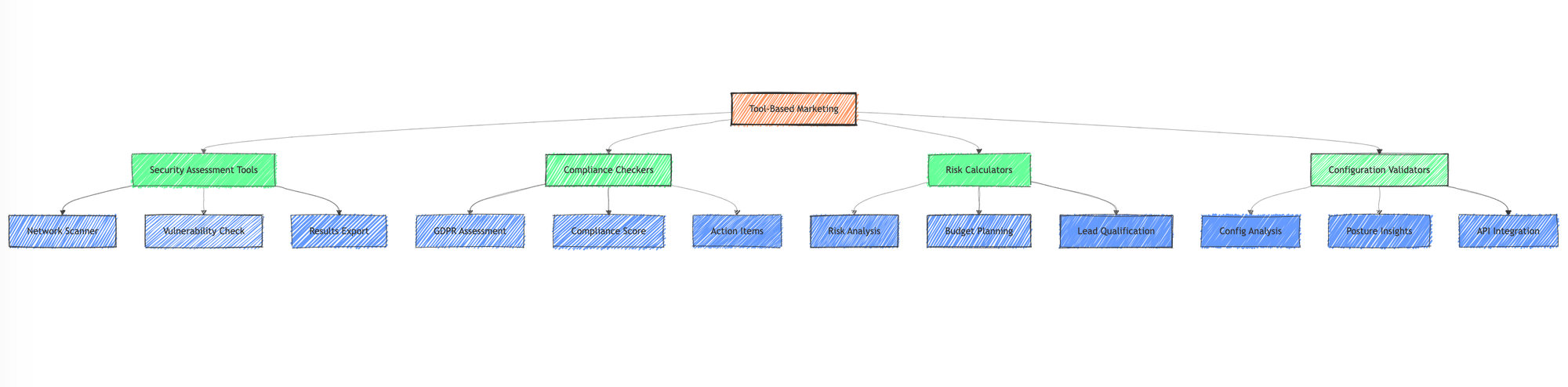
Tool-Based Marketing: Practical Implementation
The future of search marketing lies in providing immediate, practical value through interactive tools. This approach is particularly effective in cybersecurity marketing, where technical capability demonstration is crucial.
1. Security Assessment Tools
Example: Network Security Scanner
Purpose: Provide immediate security insights while demonstrating expertise
Implementation Details:
- Quick scan of external network vulnerabilities
- Basic port scanning and service identification
- Common vulnerability checking
- Customizable scan parameters
- Results export and sharing capabilities
Marketing Integration:
- Lead capture through results delivery
- Upsell opportunities based on identified vulnerabilities
- Integration with full security assessment services
2. Compliance Checkers
Example: GDPR Readiness Assessment
Core Features:
- Interactive questionnaire with branching logic
- Real-time compliance score calculation
- Industry-specific requirement mapping
- Downloadable compliance reports
- Action item prioritization
Business Integration:
- Compliance gap analysis
- Recommended solution mapping
- Consultation scheduling
- Compliance roadmap generation
3. Risk Calculators
Example: Cyber Insurance Cost Estimator
- Functionality: Industry-specific risk assessment
- User Value: Budget planning assistance
- Marketing Value: Lead qualification and segmentation
- Implementation: Mobile-friendly calculator with save/share features
4. Configuration Validators
Example: Cloud Security Posture Checker
- Functionality: Automated security configuration analysis
- User Value: Immediate security posture insights
- Marketing Value: Technical capability demonstration
- Implementation: API-based tool with integration options
Strategic Implementation Guide
A systematic approach to implementing next-generation search marketing strategies.
1. Building Your Tool Suite
Phase 1: Basic Tools
Foundation Components:
- Security assessment wizard
- Compliance checklist generator
- Vulnerability scanner lite
- Password policy analyzer
Integration Requirements:
- Web-based interface
- Basic authentication
- Results storage
- PDF report generation
Phase 2: Advanced Tools
Enhanced Features:
- Custom policy generator
- Risk simulation engine
- Threat modeling system
- Integration validator
Technical Requirements:
- API integration capability
- Multi-user support
- Custom reporting
- Data analytics
Phase 3: Enterprise Tools
Advanced Capabilities:
- Full security stack analysis
- Custom compliance frameworks
- Advanced threat intelligence
- ROI calculation engine
Enterprise Features:
- Single Sign-On (SSO)
- Role-based access control
- Audit logging
- Custom deployment options
2. Distribution Strategy
Multi-Channel Presence
Platform Integration:
- Website embedding
- Mobile optimization
- API marketplace presence
- Partner network distribution
Deployment Options:
- Cloud-hosted SaaS
- On-premise installation
- Hybrid deployment
- Container-based distribution
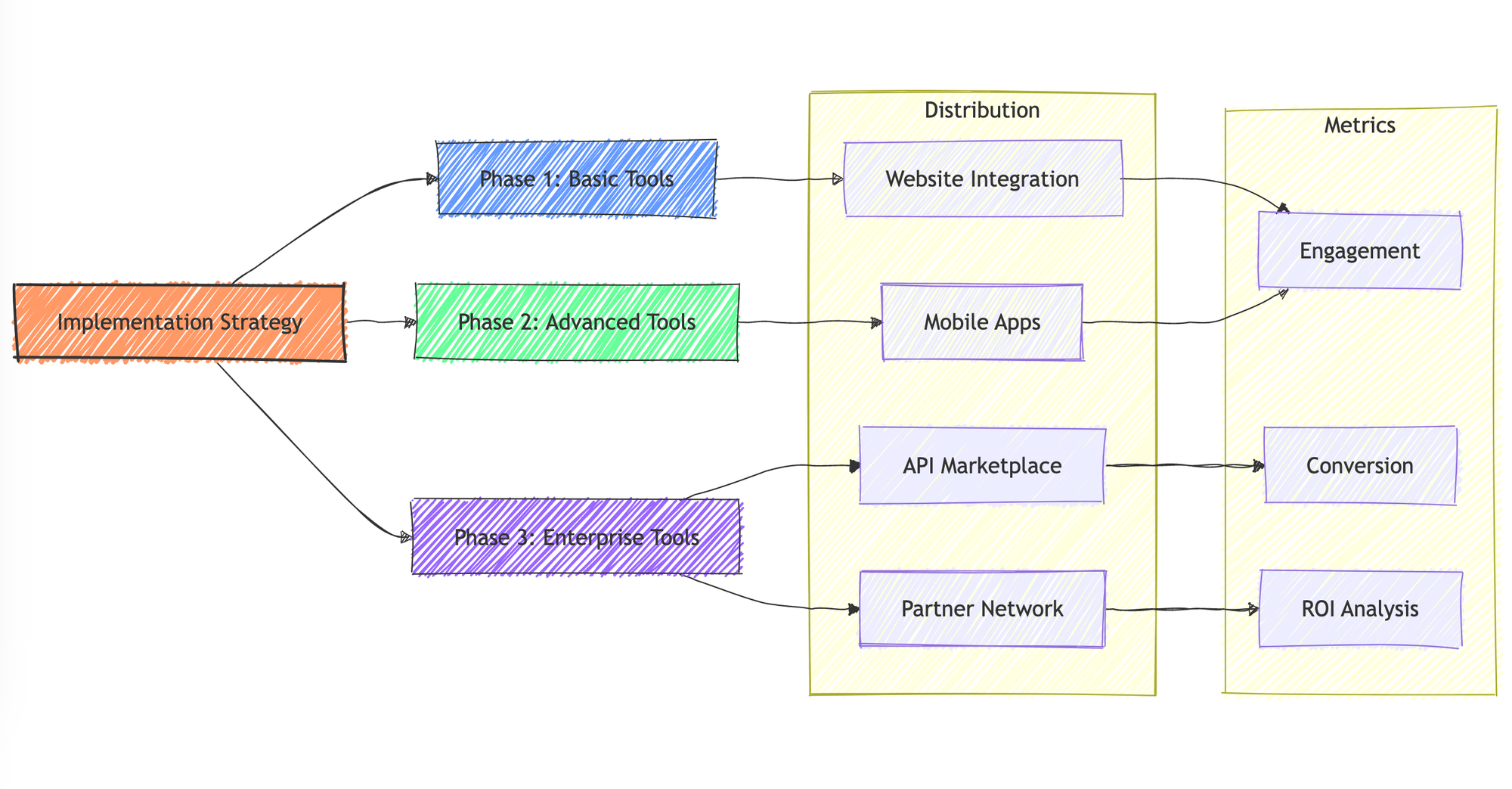
Measuring Success
1. Engagement Metrics
User Interaction Analysis
Key Metrics:
- Average session duration
- Tool completion rates
- Feature adoption velocity
- Return user frequency
Advanced Analytics:
- User journey mapping
- Drop-off point analysis
- Feature usage patterns
- User satisfaction scores
2. Conversion Metrics
Business Impact Measurement
Primary Metrics:
- Tool-to-trial conversion rate
- Assessment-to-consultation ratio
- Free-to-paid transition rate
- Enterprise adoption velocity
ROI Analysis:
- Customer acquisition cost
- Lifetime value calculation
- Revenue attribution
- Market penetration rate
Future-Proofing Your Strategy
1. Continuous Innovation
Technology Evolution
Focus Areas:
- AI/ML capability expansion
- API ecosystem development
- Interface modernization
- Security enhancement
Innovation Process:
- Regular feature updates
- User feedback integration
- Technology trend alignment
- Competitive analysis
2. Scalability Planning
Technical Architecture
Core Components:
- Microservices architecture
- Container orchestration
- API-first design
- Cloud-native infrastructure
Operational Considerations:
- Global availability
- Load balancing
- Data residency
- Disaster recovery
Conclusion
The transformation of search marketing in cybersecurity represents a fundamental shift from traditional content-centric approaches to interactive, value-driven strategies. Success in this new paradigm requires:
- Understanding and adapting to evolving search behaviors
- Developing practical, value-first tools
- Leveraging AI and community intelligence
- Maintaining a scalable, future-ready infrastructure
Organizations that embrace this evolution, focusing on immediate value delivery while building long-term relationships, will establish themselves as trusted authorities in the cybersecurity domain. The future belongs to those who can effectively combine search visibility with practical utility, creating a seamless journey from discovery to engagement to lasting partnership.

