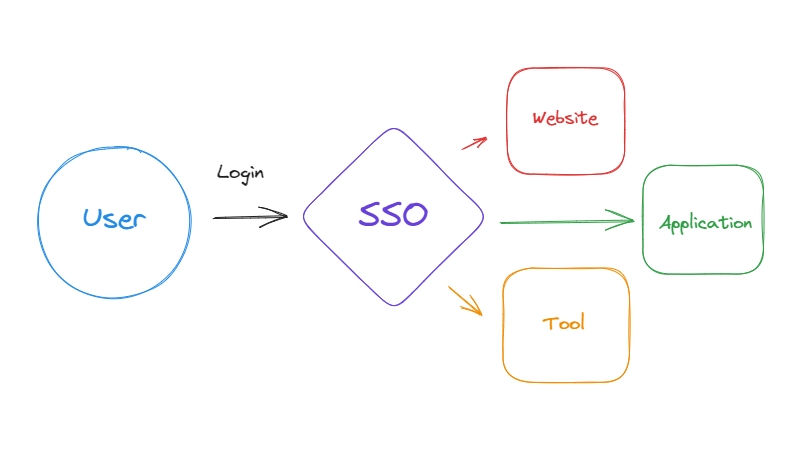
Dive into a clear technical guide explaining JWT, OAuth, OIDC, and SAML. Learn their strengths and weaknesses and use cases to choose the right approach for your next project. Stay updated with 2024 best practices and unlock seamless user experiences!