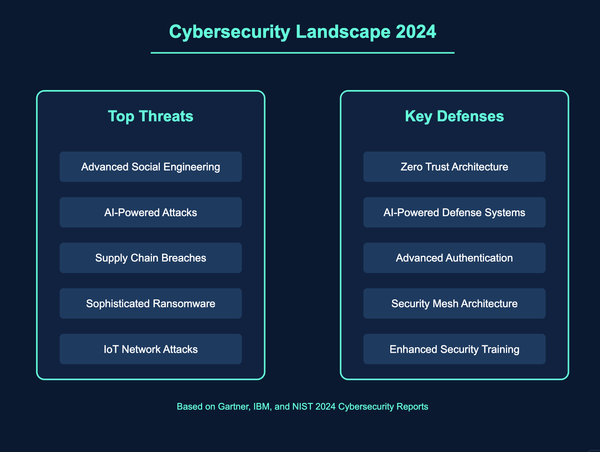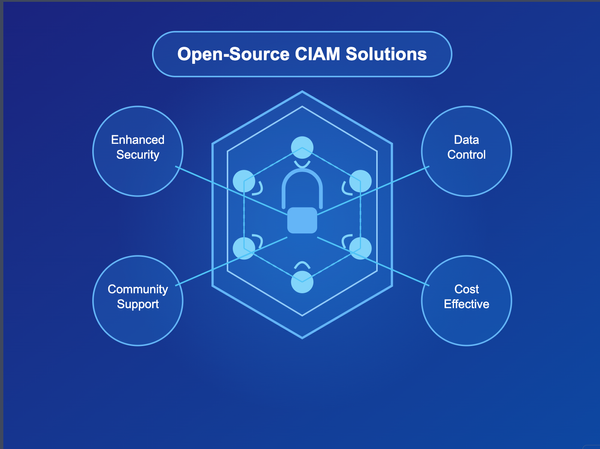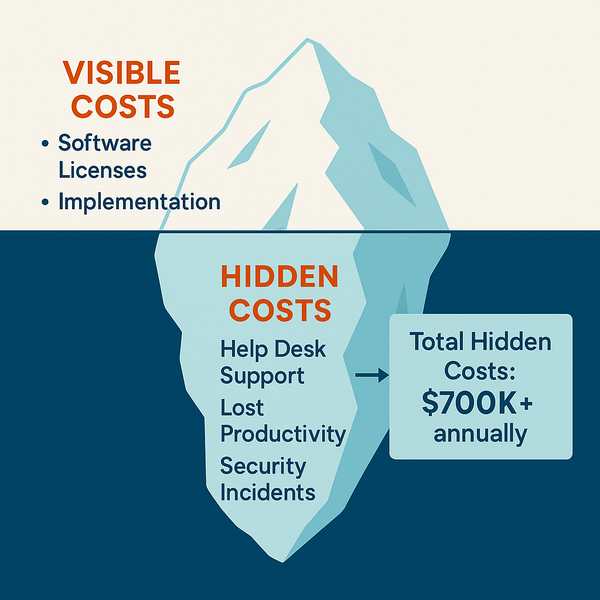

digital identity
Digital identity refers to the online or networked identity adopted or claimed in cyberspace by an individual, organization, or electronic device. It consists of various elements, including usernames, passwords, personal information, and digital certificates, which collectively authenticate and authorize access to systems and data.