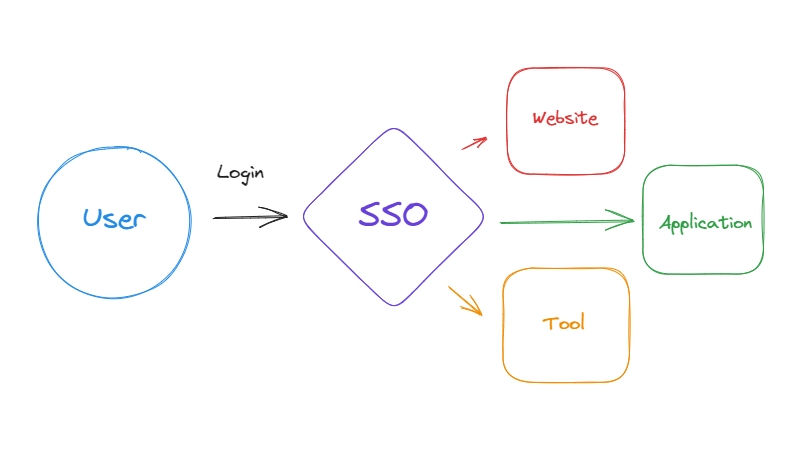
In the fast-paced world of the internet, where every click, every search, and every interaction leaves a digital footprint, the security of human identities has become paramount. Let's delve into the complexities of digital identity in a world increasingly governed by bits and bytes.