Modern Cyber Attacks: Understanding the Threats and Building Robust Defenses
Cyber attacks are more sophisticated than ever, from ransomware and phishing to DDoS attacks. This post explores these threats and provides actionable insights into building robust defenses. Learn how to implement security best practices and protect your valuable data from modern cyber attacks.
On a quiet Friday afternoon in May 2017, a hospital administrator in the UK clicked on what seemed like a routine email. Within hours, the WannaCry ransomware had spread across the National Health Service, eventually affecting over 200,000 computers across 150 countries. This watershed moment in cybersecurity history highlighted a sobering reality: in our interconnected world, the line between digital security and human lives has become increasingly blurred.
The Evolution of Cyber Threats: A Historical Perspective
The Early Days: Technical Exploits
In the 1980s and early 1990s, cyber attacks were primarily the domain of technically skilled individuals focusing on exposing system vulnerabilities. The Morris Worm of 1988, one of the first computer worms distributed via the internet, marked the beginning of a new era in digital security threats. However, these early attacks, while disruptive, were often more about proving technical prowess than causing widespread harm.
The Rise of Organized Cybercrime
As the internet became commercialized in the late 1990s and early 2000s, cybercrime evolved into a sophisticated, profit-driven enterprise. The landscape shifted from individual hackers to organized criminal networks, state-sponsored actors, and hacktivists. This transformation brought new attack vectors: targeted spear-phishing campaigns, advanced persistent threats (APTs), and sophisticated social engineering tactics.
The Modern Threat Landscape
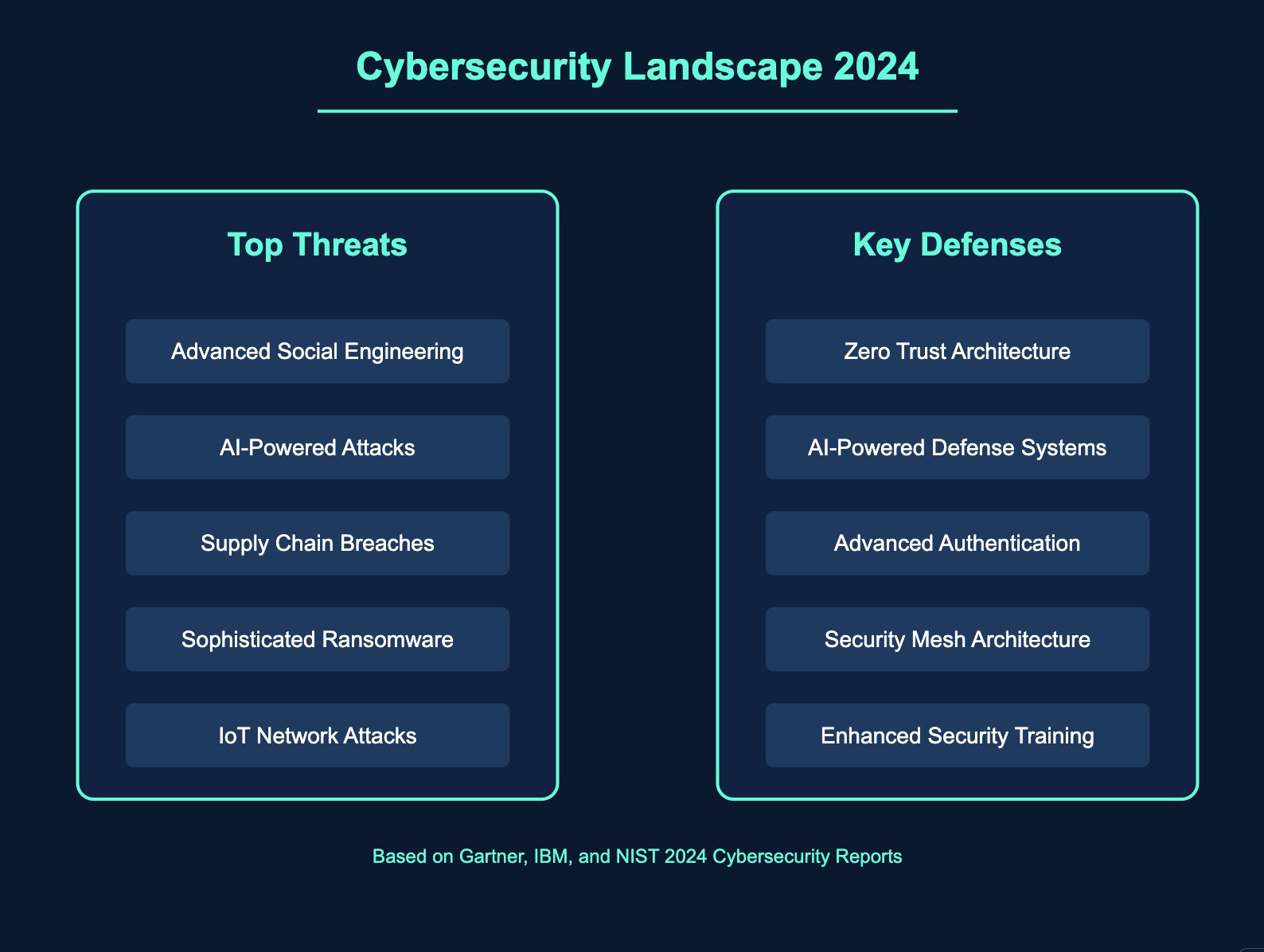
Today's cyber attacks represent a perfect storm of social manipulation, technical sophistication, and organizational complexity. Consider these statistics:
- In 2024, the average cost of a data breach reached $4.88 million
- 95% of cybersecurity breaches are caused by human error
- Ransomware attacks occur every 11 seconds
- Social engineering is involved in over 98% of cyber attacks
The Human Element
Perhaps the most significant shift in cyber attacks has been the increasing focus on human psychology. Modern attackers understand that it's often easier to manipulate people than to break through technical defenses. Take the case of the 2020 Twitter hack, where teenagers successfully compromised high-profile accounts not through sophisticated malware, but by convincing Twitter employees to grant them access through social engineering.
Understanding Today's Battlefield
The modern cybersecurity landscape is characterized by several key factors:
- Asymmetric Warfare
- Attackers need to find only one vulnerability
- Defenders must protect against all possible attack vectors
- The cost of attacking is often lower than the cost of defense
- Automation and Scale
- Artificial Intelligence-powered attacks
- Automated scanning and exploitation
- Mass customization of attack vectors
- Supply Chain Complexity
- Interconnected systems and vendors
- Third-party risk management
- Cloud service dependencies
- Regulatory Environment
- GDPR, CCPA, and other privacy regulations
- Industry-specific compliance requirements
- Cross-border data protection laws
As we delve into the specific types of attacks and defense strategies, it's crucial to understand that cybersecurity is no longer just an IT issue—it's a fundamental business risk that requires a holistic approach combining technical controls, human awareness, and organizational resilience.
1. Social Engineering Attacks
Understanding the Threat
Social engineering attacks exploit human psychology rather than technical vulnerabilities. These attacks manipulate people into breaking security protocols or revealing sensitive information.
Common Types:
- Phishing: Fraudulent attempts to obtain sensitive information by posing as trustworthy entities
- Spear Phishing: Targeted phishing attacks against specific individuals or organizations
- Vishing: Voice phishing using phone calls
- Baiting: Leaving malware-infected physical devices in strategic locations
- Pretexting: Creating a fabricated scenario to obtain information
Notable Incidents
- 2020 Twitter Bitcoin Scam: Attackers used social engineering to gain access to Twitter's internal tools, compromising high-profile accounts including those of Bill Gates, Elon Musk, and Barack Obama
- 2016 Snapchat Breach: An employee fell for a phishing email impersonating the CEO, revealing payroll information of 700 employees
Prevention Strategies
- Employee Training Programs
- Regular security awareness training
- Simulated phishing exercises
- Clear security protocols for handling sensitive information
- Technical Controls
- Email filtering systems
- DMARC, SPF, and DKIM implementation
- Multi-factor authentication (MFA)
2. Credential Stuffing
Understanding the Threat
Credential stuffing is an automated attack where cybercriminals use stolen username/password pairs to gain unauthorized access to user accounts through large-scale automated login requests.
Attack Mechanics
- Attackers obtain leaked credentials from data breaches
- Create automated scripts to test these credentials across multiple services
- Exploit the common practice of password reuse
- Use successful logins to perpetrate fraud or steal sensitive information
Notable Incidents
- 2020 Nintendo Account Breach: 300,000 accounts compromised through credential stuffing
- 2019 Dunkin' Donuts: Customer accounts breached through credential stuffing attacks
- 2016 Netflix Credential Stuffing: Attackers used stolen credentials to access and sell Netflix accounts
Prevention Strategies
- Technical Measures
- Implement robust rate limiting
- Use CAPTCHAs for suspicious login attempts
- Deploy Web Application Firewalls (WAF)
- Implement IP-based blocking for suspicious activities
- Authentication Enhancement
- Mandate strong password policies
- Implement MFA
- Use passwordless authentication methods
- Monitor for compromised credentials
- User Education
- Encourage unique passwords for each service
- Promote password manager usage
- Regular security awareness training
3. Emerging Attack Vectors
AI-Powered Attacks
- Deepfake Social Engineering: Using AI-generated voice and video to impersonate executives
- Automated Attack Pattern Generation: AI systems creating sophisticated attack patterns
- Behavioral Analysis Evasion: Using AI to mimic legitimate user behavior
Prevention Evolution
- Zero Trust Architecture
- Verify every request regardless of source
- Continuous authentication and authorization
- Microsegmentation of networks
- AI-Powered Defense
- Behavioral biometrics
- Anomaly detection
- Predictive threat analysis
- Blockchain-Based Identity
- Decentralized identity verification
- Immutable audit trails
- Self-sovereign identity solutions
4. Future of Cybersecurity Defense
Next-Generation Authentication and Identity
- Advanced Biometric Systems
- Multi-modal biometric fusion
- Combining facial, voice, and behavioral patterns
- Contextual authentication factors
- Liveness detection and anti-spoofing
- Continuous Authentication Frameworks
- Real-time behavior analysis
- Risk-based authentication scoring
- Adaptive security policies
- Neural Biometrics
- Brain-wave pattern recognition
- Cognitive fingerprinting
- Emotional state analysis
- Multi-modal biometric fusion
- Quantum-Era Cryptography
- Post-Quantum Algorithms
- Lattice-based cryptography
- Hash-based signatures
- Multivariate cryptographic systems
- Quantum Key Distribution (QKD)
- Satellite-based QKD networks
- Metropolitan QKD infrastructure
- Quantum random number generators
- Hybrid Cryptographic Systems
- Classical-quantum combinations
- Algorithm agility
- Backward compatibility solutions
- Post-Quantum Algorithms
Advanced Defense Systems
- AI-Powered Security Operations
- Autonomous Security Platforms
- Self-learning security systems
- Predictive threat detection
- Automated response orchestration
- Cognitive Security Analytics
- Natural language threat analysis
- Visual pattern recognition
- Contextual risk assessment
- Neural Network Defense
- Deep learning attack detection
- Adversarial AI protection
- AI-driven forensics
- Autonomous Security Platforms
- Self-Healing Architecture
- Automated Resilience
- Real-time vulnerability remediation
- Dynamic security policy adjustment
- Autonomous system hardening
- Intelligent Recovery Systems
- Automated backup verification
- Smart failover mechanisms
- Self-restoring configurations
- Adaptive Security Mesh
- Dynamic security perimeter
- Automated microsegmentation
- Context-aware protection
- Automated Resilience
- Privacy-Preserving Computing
- Zero-Knowledge Systems
- Advanced ZK-proof protocols
- Privacy-preserving authentication
- Secure multi-party computation
- Homomorphic Encryption
- Fully homomorphic encryption applications
- Encrypted data processing
- Secure cloud computing
- Confidential Computing
- Hardware-based encryption
- Secure enclaves
- Trusted execution environments
- Zero-Knowledge Systems
Emerging Defense Paradigms
- Biological Security Integration
- DNA-Based Authentication
- Genetic verification systems
- Molecular computing security
- Bioelectric authentication
- Human-Computer Interface Security
- Neural interface protection
- Thought-based authentication
- Biological encryption keys
- DNA-Based Authentication
- Quantum Defense Systems
- Quantum Sensing
- Quantum radar detection
- Quantum imaging security
- Quantum sensor networks
- Quantum Machine Learning
- Quantum pattern recognition
- Quantum anomaly detection
- Quantum optimization for security
- Quantum Sensing
- Distributed Security Frameworks
- Blockchain-Based Security
- Decentralized identity management
- Smart contract security controls
- Distributed security governance
- Edge Security Mesh
- Autonomous edge protection
- Distributed threat detection
- Edge-based encryption
- Blockchain-Based Security
- Cognitive Security Solutions
- Natural Interface Security
- Voice command authentication
- Gesture-based security
- Ambient computing protection
- Emotional Intelligence Security
- Stress-based threat detection
- Emotional state authentication
- Psychological security profiling
- Natural Interface Security
Comprehensive Implementation Guide
Immediate Actions: Building the Foundation
- Enhanced Security Baseline
- Implement Risk-Based MFA
- Adaptive authentication based on user behavior
- Context-aware access policies
- Biometric authentication for critical systems
- Comprehensive Security Audits
- Automated vulnerability scanning
- Third-party security assessments
- Compliance gap analysis
- Advanced Incident Response
- Automated playbooks for common scenarios
- Integration with SOAR platforms
- Regular tabletop exercises
- Modern Employee Training
- Gamified security awareness programs
- Role-specific security training
- Measured learning outcomes
- Implement Risk-Based MFA
- Advanced Technical Controls
- Zero Trust Network Architecture
- Microsegmentation with dynamic policies
- Identity-aware proxies
- Just-in-time access provisioning
- Next-Gen Access Control
- Attribute-based access control (ABAC)
- Risk-adaptive access control
- Continuous authorization
- Enhanced Monitoring
- ML-powered SIEM systems
- User and entity behavior analytics (UEBA)
- Network detection and response (NDR)
- Comprehensive Testing
- Purple team exercises
- Adversary emulation
- Bug bounty programs
- Zero Trust Network Architecture
Long-term Strategy: Building Resilience
- Evolution of Security Culture
- Security Champions Network
- Dedicated security advocates in each department
- Peer-to-peer learning programs
- Recognition and reward systems
- Continuous Learning Framework
- Personal development paths
- Certification support
- Knowledge sharing platforms
- Measurable Security Metrics
- Security scorecards
- KPI tracking
- Regular benchmarking
- Collaborative Security Model
- Cross-functional security teams
- Vendor security management
- Industry partnerships
- Security Champions Network
- Strategic Technology Investment
- Next-Generation Security Tools
- Cloud-native security platforms
- Container security solutions
- API security frameworks
- Advanced Authentication Systems
- Passwordless authentication
- Continuous behavioral authentication
- Identity orchestration platforms
- Automation and Orchestration
- Security workflow automation
- Automated compliance monitoring
- Self-healing systems
- Threat Intelligence Platform
- Real-time threat feeds
- Automated indicator sharing
- Threat hunting capabilities
- Next-Generation Security Tools
- Innovation Integration
- Emerging Technology Adoption
- Quantum-resistant cryptography
- Blockchain-based identity systems
- Edge computing security
- Research and Development
- Internal security innovation lab
- Academic partnerships
- Technology proof of concepts
- Security by Design
- Secure development frameworks
- DevSecOps implementation
- Security architecture reviews
- Emerging Technology Adoption
Implementation Roadmap
- Phase 1: Foundation
- Security assessment and gap analysis
- Basic security controls implementation
- Initial training program rollout
- Essential monitoring setup
- Phase 2: Enhancement
- Advanced security controls deployment
- Automated response capabilities
- Enhanced training and awareness
- Security metrics establishment
- Phase 3: Optimization
- AI/ML security integration
- Advanced threat detection
- Mature security program
- Innovation implementation
- Phase 4: Evolution
- Continuous improvement
- Technology refresh cycles
- Program expansion
- Strategic partnerships
Conclusion
The landscape of cyber attacks continues to evolve, with attackers becoming increasingly sophisticated in their methods. Organizations must adopt a multi-layered approach to security, combining technical controls with human awareness and emerging technologies. The future of cybersecurity will likely see greater integration of AI, quantum-safe cryptography, and automated defense systems, but the fundamental principles of security awareness and defense-in-depth will remain crucial.
The key to protecting against modern cyber attacks lies in staying informed about emerging threats, maintaining robust security practices, and fostering a security-conscious culture. As we move forward, the focus should be on building resilient systems that can adapt to new threats while maintaining usability and efficiency.
Industry White Papers
- Cloud Security Alliance: Top Threats to Cloud Computing: The Pandemic Eleven
- SANS Institute: 2024 State of Security Awareness Report
- Gartner: Top Strategic Technology Trends for 2024
Government Advisories
- CISA : Known Exploited Vulnerabilities Catalog
- CISA: "Shields Up" Technical Guidance
- FBI: Internet Crime Report 2022
- National Cyber Security Centre (UK): Annual Review 2023

