Social Engineering Attacks: Prevention and Best Practices [Infographic]
Over the years, social engineering attacks have been a regular phenomenon against companies. It has actually become more and more sophisticated. It is high time for businesses to perform careful research and use the right instruments to remain ahead of fraudsters.
![Social Engineering Attacks: Prevention and Best Practices [Infographic]](/content/images/size/w2000/2022/01/social-engineering-attack.png)
Social engineering attacks have become a common occurrence against enterprises over the years. In fact, it has grown increasingly sophisticated.
Needless to say there is no ‘stop sign’ for cybercrimes any time soon. Instead, hackers have been coming up with more creative methods to deceive employees and people into sharing sensitive credentials.
It is high time that companies conduct proper research and utilize the right tools to keep ahead of fraudsters.
This infographic will cover what social engineering is and the best practices to avoid becoming a victim of the most common social engineering attacks.
What is Social Engineering
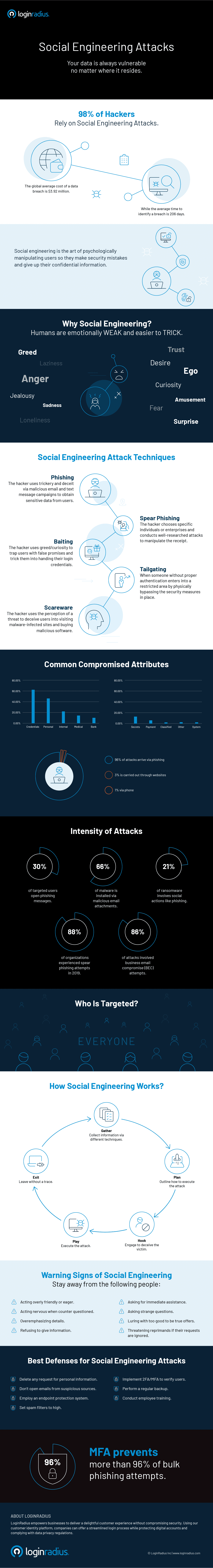
Social engineering is a cyberattack where criminals psychologically manipulate unsuspecting users into making security mistakes and giving up their confidential information.
Social engineering involves the criminal using human emotions like fear, curiosity, greed, anger, etc. to trick victims into clicking malicious links or physical tailgating attacks.
Social engineering attackers have one of two goals:
- They want to corrupt data to cause inconvenience to an organization.
- They want to steal information, money. or obtain unsolicited access.
Common Social Engineering Attack Techniques
Here is a quick overview of the most common social engineering scams used against modern enterprises and individuals.
Phishing
Phishing is the most common and widely successful form of social engineering attack. The fraudster uses trickery and deceit via email, chat, web ad, or website to persuade a person or organization to expose their PII and other valuables.
For example, the fraudster might pretend to represent a bank, a government organization, or a major corporation trusted by the naive victim. The source can be an email asking the email recipients to click on a link to log in to their accounts. They are then redirected to a fake website appearing to be legitimate, and that's where the attack takes place.
Spear Phishing
Spear Phishing is another form of social engineering where the fraudster does some background research on the victim's personal and professional life to establish the right pretext.
For example, the fraudster might reveal to the victim that they are planning a surprise birthday for a friend and are seeking help to pull it off.
Baiting
Baiting is when the fraudster uses greed or curiosity to trap the victim with false promises and trick them into handing in their login credentials.
For example, the fraudster may leave a malware-infected, authentic-looking flash drive (or bait) in the least suspicious area like the bathroom or elevator of a company. The bait will also have enticing labels like a payroll list or appraisal list that will be tempting enough to insert on a computer.
Tailgating
Tailgating happens when someone without proper authentication enters into a restricted area by physically bypassing the security measures in place.
For example, the attacker can strike up conversations with an employee in the lobby or the parking lot and use the familiarity to enter the office premises and get past the front desk.
Scareware
Scareware is a malware tactic where the fraudster perceives a threat to deceive users into visiting malware-infected sites and buying malicious software.
Examples include PC Health Check Programs and Antivirus Updaters that scare victims into buying diagnostic and repair services they do not need.
Warning Signs of Social Engineering Attacks
One of the best ways to protect against social engineering is to understand the warning signs and steer clear of attacks. A few of the warning signs include:
- Asking for immediate assistance.
- Asking to verify your information.
- Acting overly friendly or eager.
- Acting nervous when counter questioned.
- Overemphasizing details.
- Luring with too good to be true offers.
- Threatening reprimands if their requests are ignored.
Best Practices to Prevent Social Engineering Attacks
Be careful of what you share. And no, you don't need to be paranoid about these attacks. Preventing them is possible. The following are a few ways that help.
- Set spam filters to high. Every email program has spam filters. To find out, look closely through your setting options and set them too high. It will help you keep away from spam messages to a large extent.
- Never use the same password for different accounts. If the attacker gets hold of one account, they will be able to hack other accounts too.
- Use two-factor or multi-factor authentication. Just the password is no longer enough to secure your account. Additional layers are just are crucial. It can be a security question, a captcha, fingerprinting, or SMS confirmation codes.
- When in doubt, change passwords right away. If you think you gave away your password to a spammer, change all your passwords immediately.
- Educate employees. Knowledge is key. Keep your employees aware of the latest social engineering threats and help them exercise the necessary caution, whenever needed.
To learn more about Social Engineering Attacks – preventions and best practices, check out the infographic created by LoginRadius.
Originally Published at LoginRadius



