Understanding Privileged Access Management (PAM): A Comprehensive Guide
Privileged Access Management (PAM) is crucial in today's threat landscape. This guide explores what PAM is, why it's essential for your organization, and how it safeguards against unauthorized access. Learn about best practices and key features to strengthen your security posture.
Cybersecurity threats are growing exponentially, and protecting privileged access has become a cornerstone of any robust defense strategy. Privileged Access Management (PAM) is not just a tool but a philosophy that helps organizations safeguard their most sensitive data and systems. This guide breaks down everything cybersecurity professionals need to know about PAM—its basics, history, and where it's headed.
Table of Contents
- Introduction to PAM
- Historical Context and Evolution
- Understanding PAM Architecture
- Essential PAM Capabilities
- Cloud-Specific PAM Considerations
- Zero Trust and PAM
- Best Practices and Guidelines
- Compliance and Regulatory Considerations
- Common Challenges and Solutions
- Measuring PAM Success
- Future Trends and Evolution
- Conclusion and Next Steps
1. Introduction to Privileged Access Management (PAM)
Think of privileged access like having a master key to your organization's most valuable rooms. Just as you wouldn't want everyone to have access to every room in a building, organizations need to carefully control who has access to sensitive systems and data. This is where Privileged Access Management comes in.
PAM is a set of tools and practices designed to secure accounts with elevated access to critical systems and data. It as a vault, not just for passwords but also for all forms of privileged access, ensuring only the right people have access to the right resources at the right time.
Historically, administrators managed privileged access with shared root or admin credentials. Over time, as systems became more interconnected, the risks of mishandling these accounts skyrocketed. This led to the evolution of PAM into a sophisticated solution that doesn’t just secure but also monitors and controls privileged access.
What is PAM?
Privileged Access Management (PAM) is a comprehensive security strategy and set of technologies designed to control, monitor, and secure elevated access to an organization's critical resources. It's like having a sophisticated security system that not only controls who gets the master keys but also tracks how they use them and ensures they return them when they're done.
Why PAM Matters Today
Organizations face increasing cybersecurity threats from both external attackers and potential insider risks. Consider these facts:
- According to recent studies, 80% of cloud breaches involve compromised credentials
- Over 74% of data breaches start with privileged access abuse
- The average cost of a data breach has reached millions of dollars
PAM has become more critical than ever because:
- Organizations are moving to the cloud, expanding their attack surface
- Remote work has become the norm, requiring secure access from anywhere
- Regulatory compliance requirements are becoming stricter
- Cyber attacks are growing more sophisticated
- The cost of data breaches continues to rise
2. Historical Context and Evolution of PAM
The Early Days: Password Vaults
PAM started simply - as password vaults in the late 1990s and early 2000s. Think of these early systems as digital safes where organizations stored their most important passwords. While better than writing passwords down or sharing them verbally, these systems were basic and often isolated.
The Transition Years: Beyond Simple Storage
As organizations grew more complex and cyber threats evolved, PAM evolved too. Key developments included:
Mid-2000s:
- Introduction of session monitoring and recording
- Basic privilege elevation capabilities
- Initial automation of password changes
2010-2015:
- Integration with identity management systems
- Enhanced audit and compliance features
- Introduction of privileged session management
- Development of application-to-application password management
2015-2020:
- Cloud-ready PAM solutions emerge
- Just-In-Time (JIT) privilege elevation
- Integration with DevOps tools and processes
- Advanced threat analytics
Modern PAM: A Comprehensive Security Approach
Today's PAM solutions are sophisticated platforms that offer:
Core Capabilities:
- Privileged account discovery and management
- Password and secrets management
- Session recording and monitoring
- Access request and approval workflows
- Real-time threat detection
- Cloud infrastructure protection
Advanced Features:
- AI-powered threat detection
- Zero Trust architecture support
- Cloud-native privileged access management
- DevOps secrets management
- Just-In-Time access provisioning
- Robust reporting and analytics
The Market Today
The PAM market has grown significantly:
- Current market size: $2.37 billion (2024)
- Expected growth rate: 10% annually
- Major players: CyberArk, Delinea, BeyondTrust, and others
- Growing focus on cloud security and automation
Looking Ahead
PAM continues to evolve with:
- Increased adoption of AI and machine learning
- Enhanced cloud security capabilities
- Greater integration with other security tools
- Focus on user experience and automation
- Expansion into new areas like IoT and operational technology
Understanding this evolution helps organizations appreciate why PAM has become such a critical component of cybersecurity strategy and why it continues to evolve to meet new challenges in our increasingly connected world.
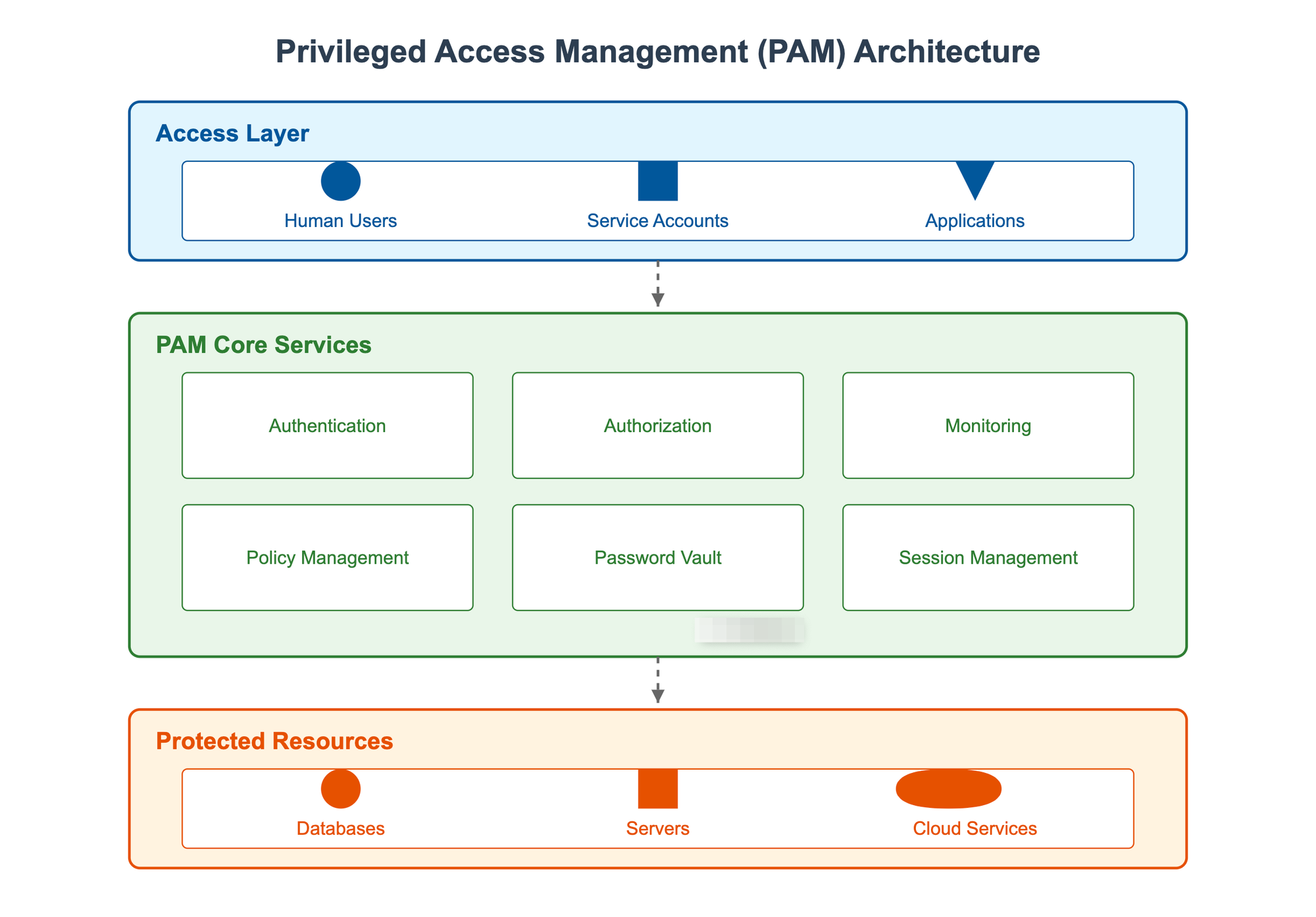
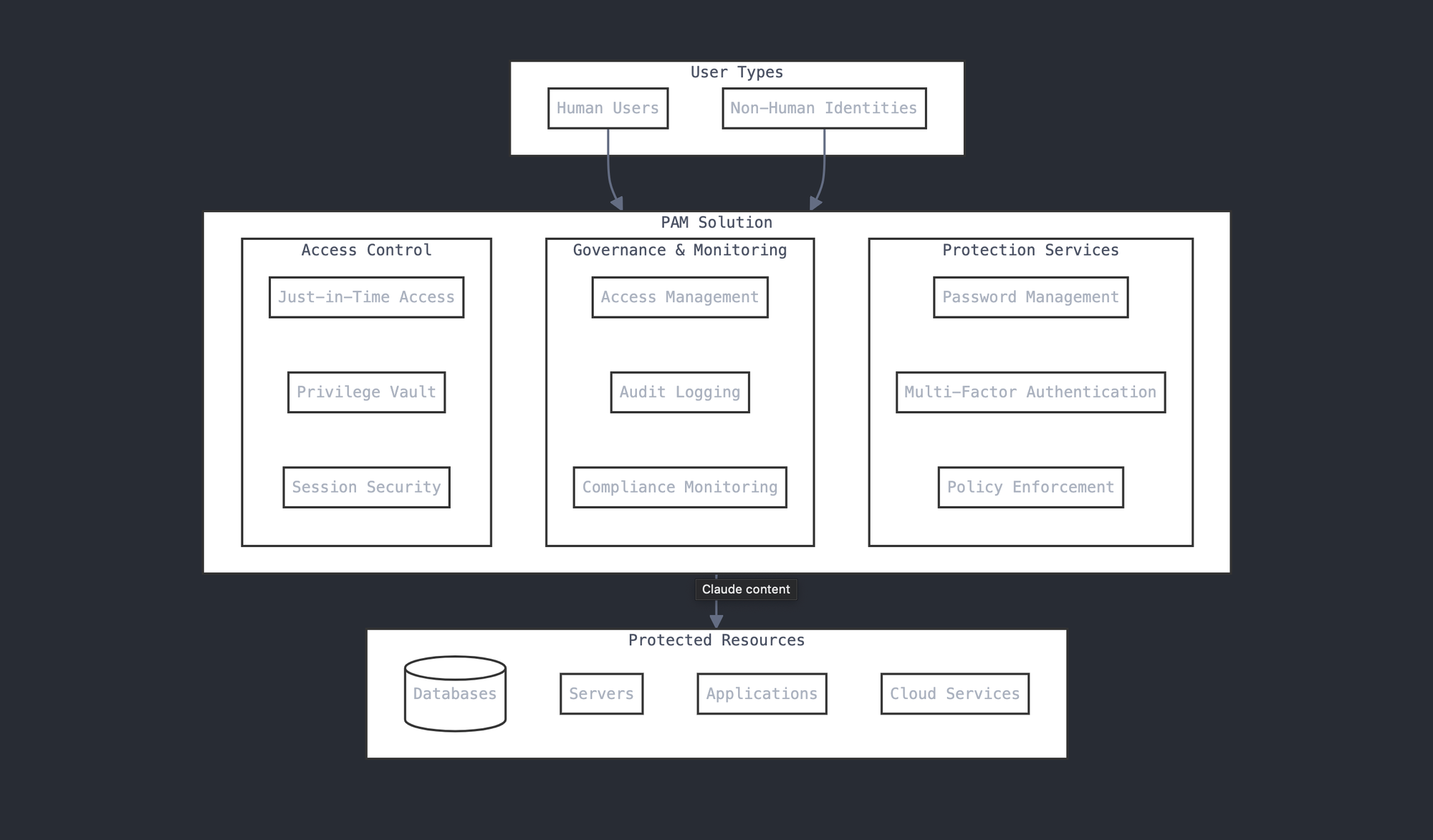
3. Understanding PAM Architecture: Building Blocks of Secure Access
The Foundation: What Makes Up a PAM System?
Think of a PAM system like a high-security bank. Just as a bank has various security layers - from the vault to security cameras to guard stations - PAM has multiple components working together to keep your privileged access secure. Let's break down each major component:
1. The Vault (Password and Secrets Management)
Picture this as the bank's main vault where all valuable items are stored. In PAM terms:
- Stores all privileged credentials securely using strong encryption
- Automatically changes passwords on a regular schedule
- Manages encryption keys and digital certificates
- Provides emergency access procedures (like the bank's emergency protocols)
Real-world example: When a system administrator needs to access a critical server, they don't actually see or know the password. The vault provides temporary access without exposing the actual credentials.
2. Access Control Center (Policy Engine)
Think of this as the bank's security office that decides who gets access to what. It:
- Sets and enforces access rules
- Determines who can access which systems
- Controls when and how long access is granted
- Manages approval workflows
- Implements the principle of least privilege
Real-world example: A database administrator might need elevated access only during maintenance windows. The policy engine ensures they can't access the database outside these approved times.
3. Session Management (The Security Camera System)
Like a bank's surveillance system, this component:
- Records all privileged sessions
- Monitors active sessions in real-time
- Can terminate suspicious sessions
- Provides video-like playback for auditing
- Creates searchable logs of all actions
Real-world example: If someone accesses a critical financial system, every keystroke and action is recorded, just like a security camera recording everyone in the bank vault.
4. Authentication Hub (The Security Checkpoint)
Similar to the bank's entry security, this component:
- Verifies user identities
- Manages multi-factor authentication
- Integrates with existing identity systems
- Controls access methods
- Handles emergency access procedures
5. Discovery Engine (Security Patrol)
Like security guards doing regular patrols, this component:
- Continuously scans for new privileged accounts
- Identifies unmanaged privileged access
- Detects security policy violations
- Finds forgotten or orphaned accounts
- Monitors for new systems and applications
How Privileged Access Management Works
PAM works on a simple principle—control, monitor, and minimize access. Here’s how it typically functions:
- Discovery: PAM tools identify all privileged accounts across systems, including hidden and inactive ones.
- Credential Management: It stores credentials in a secure vault, rotating them regularly to prevent misuse.
- Session Monitoring: PAM tracks user activities during privileged sessions, recording commands and actions for auditing.
- Just-In-Time Access: Instead of always-on privileges, users get access only when they need it and only for specific tasks.
These mechanisms ensure that organizations enforce the “least privilege” principle, granting users only the permissions they need to perform their duties.
PAM Deployment Models: Choosing Your Security Setup
1. On-Premises Deployment
- Complete control over all components
- Direct management of security
- Higher initial costs but potentially lower long-term costs
- Requires dedicated IT staff and infrastructure
Best for: Organizations with strict data sovereignty requirements or heavily regulated industries
2. Cloud-Based PAM (SaaS)
- Lower initial setup costs
- Automatic updates and maintenance
- Scalable based on needs
- Managed by the vendor
- Always accessible from anywhere
Best for: Organizations looking for quick deployment and minimal infrastructure management
3. Hybrid Deployment
- Combines on-premises and cloud components
- Flexible architecture
- Can keep sensitive data local while leveraging cloud benefits
- Balances control and convenience
Best for: Organizations with diverse needs or those transitioning to the cloud
Integration Points: Connecting Your Security Systems
Essential Integrations
PAM needs to work with:
- Identity Management Systems (like Active Directory)
- Cloud Platforms (AWS, Azure, Google Cloud)
- Security Information and Event Management (SIEM) systems
- IT Service Management (ITSM) tools
- DevOps tools and pipelines
Modern PAM Architecture Features
1. Zero Trust Implementation
- Never trust, always verify approach
- Continuous verification of every access attempt
- Context-based authentication
- Just-In-Time access provisioning
2. AI/ML Capabilities
- Anomaly detection in access patterns
- Risk-based access decisions
- Predictive security analytics
- Automated threat response
3. Automation Features
- Automated password rotation
- Scheduled access provisioning
- Automated compliance reporting
- Self-service access requests
Best Practices for PAM Architecture
- Layer Your Security
- Multiple authentication factors
- Separate admin and user networks
- Segmented access levels
- Build in Redundancy
- High availability setup
- Disaster recovery plans
- Emergency access procedures
- Plan for Scale
- Start small but plan big
- Use modular components
- Choose flexible integration options
- Focus on User Experience
- Simple, intuitive interfaces
- Streamlined access requests
- Clear security policies
- Efficient workflows
Common Challenges and Solutions
- Challenge 1: Complex Implementation
- Solution: Start with critical systems first, then expand gradually
- Challenge 2: User Resistance
- Solution: Focus on making security seamless and user-friendly
- Challenge 3: Legacy System Integration
- Solution: Use PAM solutions with broad protocol support and flexible APIs
- Challenge 4: Cloud Migration
- Solution: Choose a PAM solution that supports hybrid environments and cloud-native features
Future Architecture Trends
- Increased Automation
- More self-service capabilities
- Automated compliance reporting
- AI-driven decision making
- Enhanced Cloud Integration
- Better cloud-native support
- Improved container security
- Serverless architecture support
- Advanced Analytics
- Real-time risk assessment
- Predictive security measures
- Behavioral analytics
Remember: The best PAM architecture is one that balances security with usability. It should be robust enough to protect your most sensitive assets while being simple enough for daily use without disrupting business operations.
4. Essential PAM Capabilities: A Deep Dive
Standard, Advanced, and Emerging PAM Capabilities
- Standard Capabilities: These include credential vaulting, session monitoring, and auditing. They form the backbone of any PAM system and help meet compliance standards.
- Advanced Capabilities: Today’s PAM solutions leverage AI to detect anomalies, automate entitlement reviews, and provide Just-In-Time (JIT) access.
- Emerging Capabilities: The future of PAM lies in passwordless authentication, invisible PAM (seamless, user-friendly management), and advanced integration with identity threat detection systems.
Let's break down the key capabilities of modern PAM solutions in simple terms, understanding why each matters and how they work together.
Password Vaulting and Management
How It Works
- Stores privileged passwords in an encrypted, secure database
- Automatically changes passwords on a regular schedule
- Requires approval before anyone can use sensitive passwords
- Keeps a detailed log of who accessed what and when
Example: Imagine a database administrator needs to access a critical server. Instead of knowing the actual password:
- They request access through the PAM system
- If approved, they get temporary access
- The system automatically changes the password after use
- Everything is logged for security review
Session Management and Monitoring
Key Features
- Records all privileged sessions (like watching a security camera recording)
- Allows real-time monitoring of sensitive activities
- Can instantly terminate suspicious sessions
- Creates searchable logs of all actions taken
Example: When a contractor accesses your systems:
- Every command they type is recorded
- Sensitive actions trigger alerts
- Security teams can watch in real-time if needed
- All activity is saved for audit purposes
Access Control and Elevation
This capability ensures users only get the exact level of access they need, when they need it.
How It Works
- Users start with basic access
- They request elevated privileges for specific tasks
- Approval workflows manage these requests
- Access is automatically revoked when the task is complete
Example: A help desk technician needs to install software on a user's computer:
- They request temporary admin rights
- Their manager approves for a 2-hour window
- They complete the installation
- Admin rights automatically expire
Privileged Account Discovery
This helps organizations find and manage all their privileged accounts - even ones they didn't know existed.
Key Functions
- Automatically scans systems for privileged accounts
- Identifies unused or dormant accounts
- Detects unauthorized privilege escalations
- Maps relationships between accounts and systems
5. Cloud-Specific PAM Considerations
Understanding the Cloud Security Challenge
Imagine moving from a house where you control all the locks to a large apartment complex where some security is managed by others. That's similar to the challenge organizations face when moving to the cloud. You still need to protect your assets, but the way you do it changes completely.
Key Areas of Focus
Different Types of Cloud Services
- Infrastructure as a Service (IaaS):
- Example: AWS EC2, Azure Virtual Machines
- Key focus: Securing admin access to servers and infrastructure
- Platform as a Service (PaaS):
- Example: Azure SQL Database, Google App Engine
- Key focus: Managing developer and application access
- Software as a Service (SaaS):
- Example: Salesforce, Microsoft 365
- Key focus: Controlling admin and user privileges
Cloud-Specific Security Controls
- Identity Management (IAM)
- Single Sign-On (SSO) integration
- Multi-factor authentication (MFA)
- Just-In-Time access
- Entitlement Management (CIEM)
- Understanding who has access to what
- Regular access reviews
- Automated privilege cleanup
- Access Monitoring
- Real-time activity tracking
- Anomaly detection
- Compliance reporting
6. Zero Trust and PAM
Understanding Zero Trust Simply
Think of traditional security like checking ID at the front door of a building. Once inside, people could go anywhere. Zero Trust is like checking ID at every door, every time - even if someone was just in that room five minutes ago.
Key Principles of Zero Trust in PAM
1. Never Trust, Always Verify
- Every access request must be validated
- No automatic trust based on location or network
- Continuous verification of identity
2. Least Privilege Access
- Give only the minimum access needed
- Time-limited access grants
- Regular access reviews and removals
3. Assume Breach
- Act as if your system is already compromised
- Monitor all privileged sessions
- Record all privileged activities
- Quick response to suspicious behavior
Implementing Zero Trust
- Identity Verification
- Strong authentication methods
- Regular credential rotation
- Biometric authentication where appropriate
- Access Control
- Just-In-Time access provisioning
- Risk-based access decisions
- Automatic access revocation
- Monitoring and Analytics
- Behavioral analysis
- Anomaly detection
- Real-time alerts
7. Best Practices and Guidelines
Implementing PAM in Modern Enterprises
Deploying PAM is not just about buying a tool; it’s about embedding it into your security culture. Here’s a roadmap:
- Discover Privileged Accounts: Use PAM tools to find all accounts with elevated privileges, even those forgotten over time.
- Define Policies: Clearly outline who gets access to what and under what conditions.
- Select the Right Solution: Choose a PAM solution that fits your needs—whether it’s SaaS for scalability or on-premises for control.
- Integrate with Existing Systems: Connect PAM with your IAM, cloud environments, and DevOps tools.
- Continuous Monitoring: Regularly audit privileged access logs and refine policies to adapt to new threats.
Practical Implementation Steps
- Start Small
- Begin with most critical systems
- Pilot with a small group
- Gather feedback and adjust
- Gradually expand scope
- Focus on User Experience
- Make access requests simple
- Provide clear instructions
- Offer self-service options
- Quick response to access needs
- Automate Where Possible
- Password rotation
- Access reviews
- Compliance reports
- Alert responses
The Business Value of PAM
Securing privileged access isn’t just good cybersecurity—it’s good business. Here’s why:
- Reduced Risk: By minimizing the attack surface, PAM makes it harder for adversaries to exploit your systems.
- Compliance Made Easier: Most regulatory frameworks, like GDPR and HIPAA, require stringent control over privileged accounts.
- Operational Efficiency: Automating tasks like credential rotation saves time and reduces errors.
- Improved Trust: When your systems are secure, customers and stakeholders feel more confident in your organization.
8. Compliance and Regulatory Considerations
Understanding Compliance Requirements
Common Regulations
- GDPR (General Data Protection Regulation)
- Personal data protection
- Access control requirements
- Audit trail needs
- Breach notification rules
- SOC
- Financial systems access control
- Audit requirements
- Change management
- Documentation needs
- PCI DSS
- Payment card data protection
- Access control requirements
- Monitoring and logging
- Regular testing
Practical Compliance Steps
1. Documentation
- Written policies and procedures
- Access control matrices
- Regular review and updates
- Incident response plans
2. Implementation
- Technical controls alignment
- Regular compliance checks
- Automated compliance reporting
- Training and awareness
3. Monitoring and Reporting
- Regular compliance audits
- Automated compliance checks
- Exception management
- Incident response testing
Making Compliance Work
- Integrate with Business Processes
- Build compliance into workflows
- Automate compliance checks
- Regular training and updates
- Clear escalation paths
- Regular Reviews
- Quarterly compliance checks
- Annual policy reviews
- Regular training updates
- Audit preparation
- Continuous Improvement
- Learn from incidents
- Update procedures as needed
- Incorporate new requirements
- Refine processes based on feedback
9. Common Challenges and Solutions
Despite its benefits, PAM adoption can be challenging:
Implementation Challenges
1. Technical Complexity
- Challenge: Complex integration with existing systems
- Solution:
- Start with critical systems first
- Use pre-built connectors where possible
- Engage vendor professional services
- Document all configurations
- User Resistance
- Challenge: Users resist change and new security measures
- Solution:
- Phased implementation approach
- Clear communication of benefits
- User-friendly interfaces
- Regular training and support
3. Cost Management
- Challenge: High implementation and maintenance costs
- Solution:
- Start with essential features
- Clear ROI calculation
- Phased budget allocation
- Regular cost-benefit analysis
Operational Challenges
1. Performance Impact
- Challenge: PAM solutions can slow down access
- Solution:
- Optimize configurations
- Use caching where appropriate
- Regular performance monitoring
- Load balancing for large deployments
2. Emergency Access
- Challenge: Handling urgent access needs
- Solution:
- Break-glass procedures
- Emergency access protocols
- Documented escalation paths
- Post-incident review process
10. Measuring PAM Success
Key Performance Indicators (KPIs)
- Security Metrics
- Number of privileged account breaches
- Time to detect unauthorized access
- Number of failed access attempts
- Password policy compliance rate
- Operational Metrics
- Average time for access approval
- System uptime
- Number of emergency access requests
- Help desk tickets related to access
- Business Impact Metrics
- Cost savings from automated processes
- Reduction in audit findings
- Compliance violation reduction
- Time saved in access management
ROI Calculation
- Cost Factors
- Implementation costs
- Training expenses
- Ongoing maintenance
- Staff time allocation
- Benefits Quantification
- Security incident reduction
- Audit cost savings
- Operational efficiency gains
- Compliance penalty avoidance
11. Future Trends and Evolution in PAM
The PAM landscape is evolving rapidly, and these trends are shaping its future:
AI and Machine Learning Integration
- Automated Threat Detection
- AI systems that can spot unusual patterns in privileged access
- Real-time alerts for suspicious activities
- Learning from past incidents to prevent future ones
- Smart Access Decisions
- AI-powered recommendations for access approvals
- Automated risk scoring for access requests
- Predictive analytics for potential security issues
Zero-Standing Privileges
- Moving away from permanent privileged access
- Just-In-Time (JIT) access becoming the norm
- Dynamic privilege assignment based on context
Unified Identity Security Platforms
- Combining PAM with IAM and CIEM for a holistic approach
- Hybrid and multi-cloud environments
Cloud-Native Solutions
- Built specifically for cloud environments
- Better integration with cloud services
- Improved scalability and flexibility
Emerging Technologies
- Blockchain for PAM
- Immutable audit trails
- Decentralized access control
- Enhanced transparency
- Quantum-Safe Security
- Preparing for quantum computing threats
- New encryption methods
- Future-proofing access controls
Conclusion and Next Steps
As organizations increasingly digitize their operations, Privileged Access Management is no longer optional—it’s essential. Whether you’re a large enterprise or a small business, securing privileged access protects your most critical assets from internal and external threats. Here's why PAM solutions are essential:
For Human Identities:
- Privileged accounts are prime targets for cyber attacks, as they provide extensive access to sensitive systems and data
- PAM ensures that users only have the minimum necessary privileges required for their roles, reducing the attack surface
- It enables detailed audit trails of privileged activities, crucial for compliance and incident investigation
- Automated password management prevents credential sharing and ensures regular rotation of sensitive credentials
For Non-Human Identities:
- The proliferation of service accounts, APIs, and automated processes creates a complex web of machine identities
- PAM solutions manage and secure machine-to-machine communications, preventing unauthorized access
- They provide just-in-time access for applications and services, reducing standing privileges
- Automated credential management for applications and services eliminates hardcoded passwords in scripts
Future Essentials:
- As organizations adopt more cloud services and IoT devices, the number of privileged accounts will grow exponentially
- Zero-trust security models require granular access control and continuous verification that PAM provides
- AI and automation will increase the need for secure machine identity management
- Regulatory compliance requirements are becoming stricter, making PAM's audit and control features indispensable
The rise of sophisticated cyber threats and the expanding digital footprint of organizations make PAM not just a security tool, but a business enabler that protects critical assets while enabling digital transformation. Without robust PAM solutions, organizations risk unauthorized access, data breaches, compliance violations, and potential business disruption.
Take the first step today: assess your organization’s privileged access landscape, choose the right PAM solution, and build a culture of security. Remember, in the world of cybersecurity, it’s better to be proactive than reactive.

