Understanding CIEM, CIAM, and Their Place in the IAM Ecosystem
Identity and Access Management (IAM) is vital for organizations to safeguard their digital assets.This blog post delves into the key differences between Cloud Infrastructure Entitlement Management (CIEM) and Customer Identity and Access Management (CIAM).
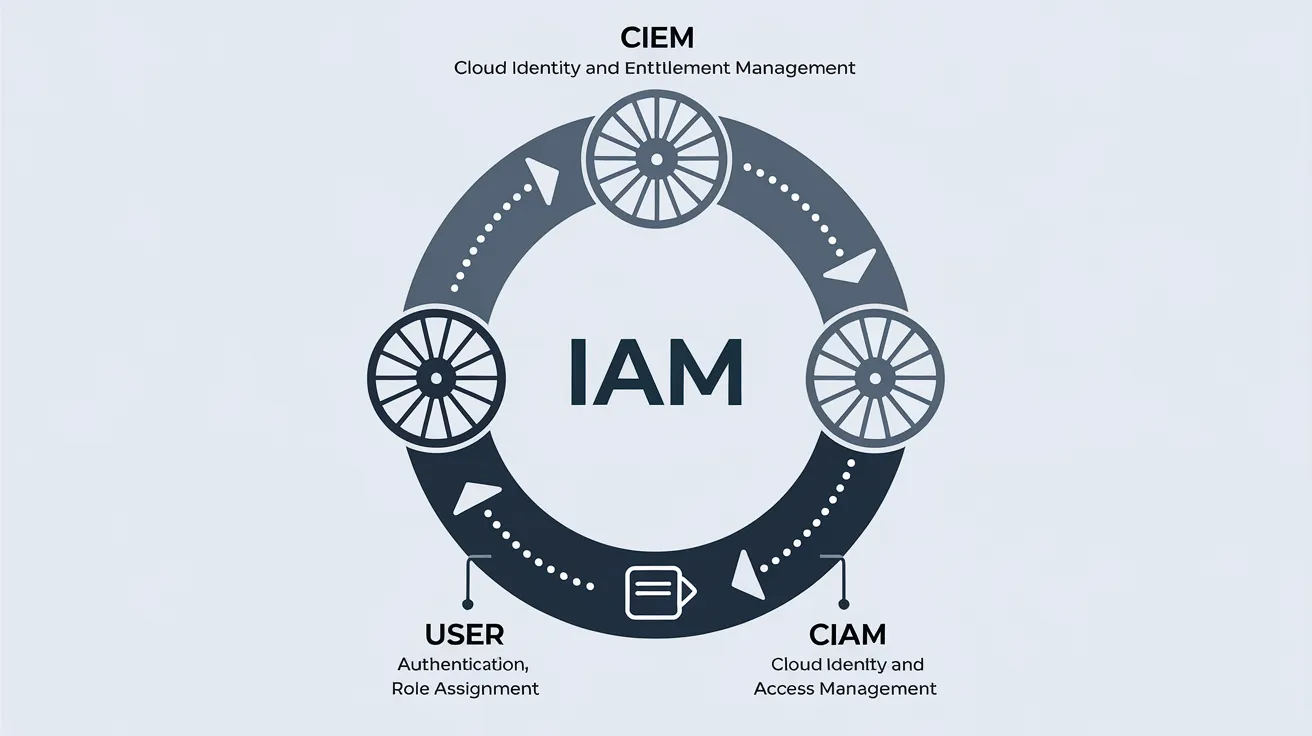
Managing identities and access rights is crucial for organizations of all sizes. This article delves into the key differences between Cloud Infrastructure Entitlement Management (CIEM) and Customer Identity and Access Management (CIAM), their relationship with the broader Identity and Access Management (IAM) industry, and how they connect with Privileged Access Management (PAM) and Identity Governance and Administration (IGA).
IAM: The Overarching Framework
Before we dive into the specifics, it's important to understand that Identity and Access Management (IAM) serves as the overarching framework for managing digital identities and user access to resources. IAM encompasses various specialized areas, including CIEM, CIAM, PAM, and IGA.
CIEM vs. CIAM: Key Differences
Cloud Infrastructure Entitlement Management (CIEM)
CIEM focuses on managing access and permissions within cloud infrastructures. Its primary purpose is to ensure that users and services have the right level of access to cloud resources, no more and no less.
Key features of CIEM:
- Cloud-specific: Designed for multi-cloud and hybrid cloud environments
- Focuses on machine and human identities within cloud services
- Emphasizes least privilege access and continuous monitoring
- Helps prevent cloud misconfigurations and excessive permissions
Customer Identity and Access Management (CIAM)
CIAM, on the other hand, is centered around managing customer identities and their access to an organization's digital services and applications.
Key features of CIAM:
- Customer-centric: Designed to manage external user identities (customers, partners)
- Focuses on user experience, including registration, authentication, and profile management
- Emphasizes scalability to handle millions of users
- Includes features for consent management and privacy compliance (e.g., GDPR)
The Relationship with IAM
Both CIEM and CIAM are specialized subsets of the broader IAM industry. While traditional IAM typically focuses on internal users (employees), CIEM and CIAM extend these concepts to cloud resources and external users, respectively.
The IAM industry has evolved to address the changing needs of organizations:
- Traditional IAM: Managing internal user access to on-premises resources
- CIAM: Extending IAM concepts to customer-facing applications and services
- CIEM: Adapting IAM principles to the complex world of cloud entitlements
Connecting the Dots: PAM and IGA
To fully understand the IAM ecosystem, we need to consider two other important components: Privileged Access Management (PAM) and Identity Governance & Administration (IGA).
Privileged Access Management (PAM)
PAM focuses on securing, controlling, and monitoring access to critical systems and sensitive data by privileged users.
How PAM connects with CIEM and CIAM:
- CIEM often incorporates PAM principles for managing high-level access to cloud resources
- CIAM may integrate with PAM for managing privileged customer accounts (e.g., super users in a SaaS platform)
Identity Governance and Administration (IGA)
IGA is concerned with identity lifecycle management, access requests, and compliance reporting across an organization's IT environment.
How IGA connects with CIEM and CIAM:
- CIEM can be seen as extending IGA principles to cloud environments, focusing on governance of cloud entitlements
- CIAM may incorporate aspects of IGA for managing customer identity lifecycles and ensuring compliance with data protection regulations
The Interplay of IAM Components
To visualize how these components work together:
- IAM serves as the foundation, providing core identity and access management capabilities.
- CIAM extends IAM to customer-facing scenarios, focusing on user experience and scalability.
- CIEM applies IAM principles to cloud resources, emphasizing security and least privilege.
- PAM adds an extra layer of security for privileged accounts across all environments.
- IGA ensures proper governance and compliance across the entire identity ecosystem.
Conclusion
While CIEM and CIAM may sound similar, they serve distinct purposes within the IAM landscape. CIEM is focused on managing access to cloud resources, while CIAM is dedicated to managing customer identities and their experience. Both are crucial components of a comprehensive identity and access management strategy, working alongside PAM and IGA to provide a secure, efficient, and compliant approach to managing identities and access in today's complex digital environments.
As organizations continue to digitalize and move to the cloud, understanding the nuances and interrelationships between these IAM components becomes increasingly important for IT leaders and security professionals.

