The Science of Password Protection: Understanding Hashing, Salting, and the Future of Authentication
Uncover the mechanics of password hashing and salting, and how these techniques are pivotal in defending against cyber threats.
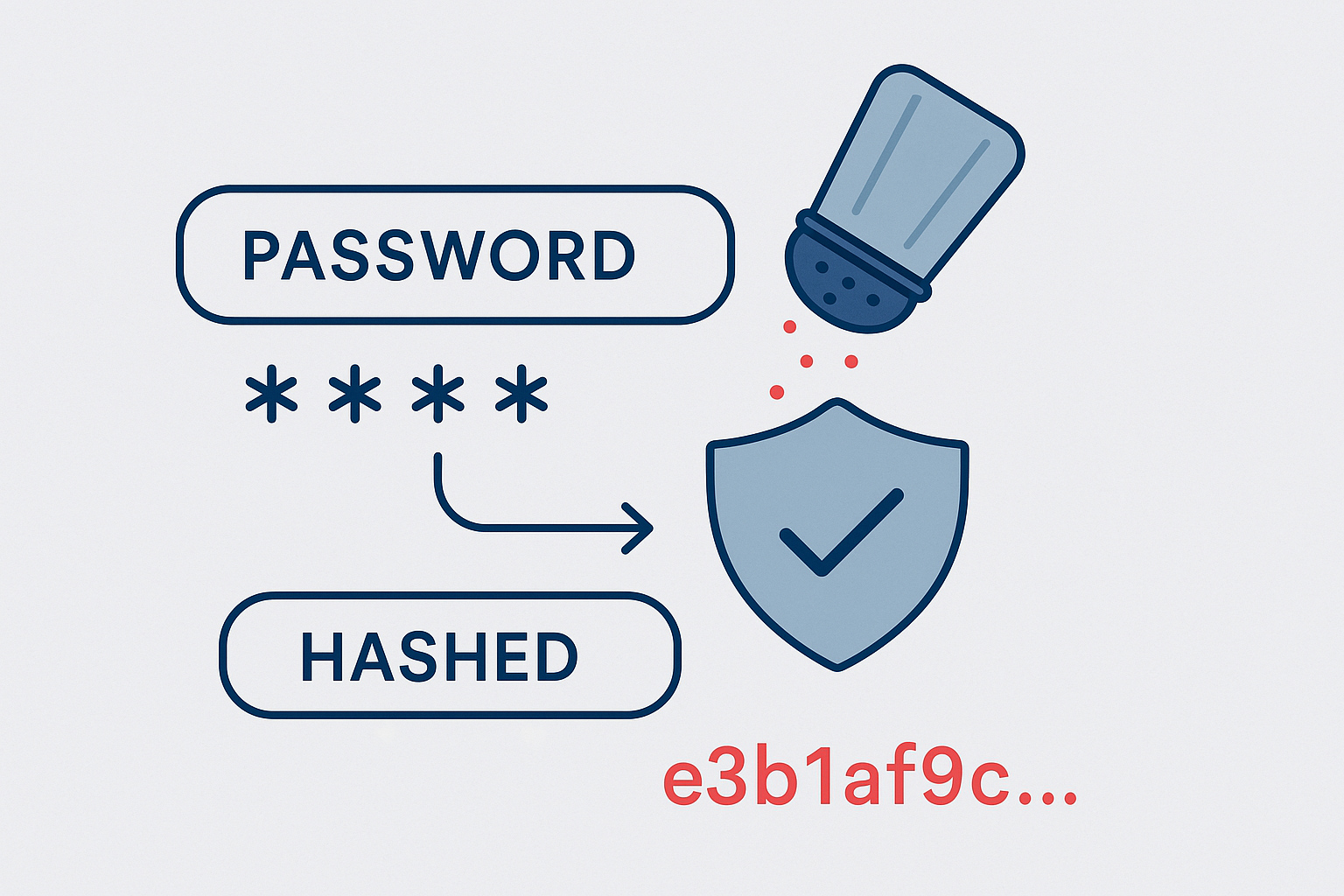
Passwords remain the primary keys to our online identities despite their well-documented vulnerabilities. Behind the scenes, responsible organizations don't actually store your passwords in plain text—instead, they use cryptographic techniques like hashing and salting to protect this sensitive information. But how exactly do these processes work, and why are they still not enough to fully secure our digital lives?
This article will demystify password hashing and salting, explore best implementation practices, and examine why even these sophisticated techniques don't completely solve our authentication security challenges. We'll also look at how passwordless authentication is changing the landscape and how AI might shape authentication in the coming years.
What is Password Hashing?
Password hashing is a fundamental security practice that transforms your plain text password into a fixed-length string of characters that appears random and unintelligible. This transformation happens through a mathematical algorithm called a hash function.
How Hashing Works
When you create a password on a website, a properly designed system will:
- Take your password (for example, "MySecretPassword123")
- Run it through a hash function
- Generate a fixed-length string of characters (the hash)
- Store only this hash in the database
For example, the password "MySecretPassword123" might produce this hash using the SHA-256 algorithm:
3d7c612fc27352f841db9b38c16d6eebab2a37e4bda66db7bd3d3e56145e8676
The critical properties of good hash functions include:
- One-way transformation: It should be computationally infeasible to reverse the process and determine the original password from the hash.
- Deterministic: The same input always produces the same output hash.
- Avalanche effect: Even a tiny change in the input (changing just one character) creates a dramatically different hash output.
- Fixed output length: Regardless of password length, the hash output has a consistent length.
Common Hashing Algorithms
Not all hashing algorithms are created equal. General-purpose cryptographic hash functions like MD5 and SHA-1 are now considered insecure for password storage because they're designed for speed rather than security. Modern password hashing should use specialized algorithms that are deliberately slow to compute, including:
- bcrypt: Designed specifically for password hashing, incorporates salting automatically and includes a work factor to adjust computational cost
- Argon2: The winner of the 2015 Password Hashing Competition, addresses various attack vectors with tunable memory, computation, and parallelism parameters
- PBKDF2 (Password-Based Key Derivation Function 2): Uses multiple iterations of a hash function to increase computational requirements
- scrypt: Memory-hard function designed to be resistant to hardware acceleration attacks
Use this Visual hashing tool to understand cryptographic hash functions and their properties.
What is Password Salting?
While hashing protects passwords, it has a significant vulnerability: identical passwords produce identical hashes. This creates several problems, particularly with rainbow table attacks (pre-computed tables of password hashes) and attacking multiple passwords simultaneously.
This is where salting comes in.
How Salting Works
Password salting adds a random string of characters (the "salt") to each password before hashing. The process works like this:
- Generate a unique random salt for each user
- Combine the salt with the user's password
- Hash the combined string
- Store both the resulting hash and the salt in the database
For example:
- Password: "MySecretPassword123"
- Random salt: "8dF7h2Kl"
- Combined string to hash: "MySecretPassword1238dF7h2Kl" or "8dF7h2KlMySecretPassword123"
- Resulting hash (stored along with the salt): "a7c8edb9..."
Why Salting Matters
Salting solves several critical problems:
- Prevents rainbow table attacks: Pre-computed hash tables become ineffective because each password is hashed with a unique salt
- Prevents hash comparisons: Even if two users have the same password, their hashes will be different because they have different salts
- Increases entropy: Adds additional randomness to passwords before hashing
- Requires per-user attacks: Forces attackers to crack each password individually rather than attacking all identical passwords at once
Best Practices for Implementing Hashing and Salting
Implementing secure password storage requires careful attention to several key aspects:
Choosing the Right Algorithm
- Use modern, purpose-built password hashing algorithms (bcrypt, Argon2, PBKDF2)
- Avoid general cryptographic hash functions like MD5, SHA-1, and even SHA-256 when used alone
- Stay informed about cryptographic developments and be prepared to upgrade
Proper Salt Generation
- Generate cryptographically strong random salts for each user
- Use a reliable source of randomness (like
/dev/urandomon Unix systems orCryptGenRandomon Windows) - Make salts sufficiently long (16 bytes/128 bits is generally recommended)
- Never reuse salts across different users
Configuring Work Factors
Modern hashing algorithms allow adjusting their computational cost through work factors:
- Set work factors to make hashing take approximately 100-500ms on your server hardware
- Increase work factors over time as hardware becomes faster
- Balance security with user experience and server load
- Consider using adaptive work factors based on the sensitivity of the account
Database Storage Considerations
- Store the hash and salt together, along with the algorithm identifier and work factor
- Consider using a format like:
$algorithm$iterations$salt$hash - Example (bcrypt):
$2a$10$N9qo8uLOickgx2ZMRZoMyeIjZAgcfl7p92ldGxad68LJZdL17lhWy - Never store plain text passwords, even temporarily
Secure Implementation
- Use established libraries rather than implementing hashing algorithms from scratch
- Keep password-handling code minimal and well-reviewed
- Implement timing-safe comparison functions when verifying passwords
- Consider using security frameworks that handle hashing correctly by default
Key Differences Between Hashing and Salting
Understanding the distinct roles of hashing and salting is important:
Purpose
- Hashing: Converts passwords into fixed-length strings that cannot be reversed
- Salting: Ensures that identical passwords don't produce identical hashes
Function
- Hashing: A one-way cryptographic transformation
- Salting: A data preparation technique that adds randomness
Security Contribution
- Hashing: Prevents storage of plain text passwords
- Salting: Prevents precomputation attacks and forces per-user cracking efforts
Independence vs. Complementary
- Hashing: Can be implemented without salting (though not recommended)
- Salting: Always requires hashing to be effective; salt alone provides no security
Limitations of Hashed and Salted Passwords
Despite these security measures, several vulnerabilities remain:
Credential Stuffing Persists
Credential stuffing attacks don't attempt to crack passwords—they simply try username/password combinations obtained from data breaches on other websites. Since many users reuse passwords across sites, attackers can gain access even if passwords are properly hashed and salted on your system.
When an attacker tries a username/password combination:
- Your system hashes the submitted password using the stored salt
- It compares this hash to the stored hash
- If they match, access is granted
No amount of hashing or salting can prevent this attack because it exploits user behavior (password reuse) rather than technical vulnerabilities.
Hardware Advancements vs. Security
Advances in computational power, particularly specialized hardware like GPUs and ASICs, continually reduce the cost of password cracking:
- A modern GPU can attempt billions of password hashes per second for MD5 (an outdated algorithm)
- Even with stronger algorithms, the economics of cracking continue to favor attackers
- The inevitable march of hardware improvements requires constant adjustment of work factors
Implementation Vulnerabilities
Common mistakes undermine even theoretically secure systems:
- Insufficient randomness in salt generation
- Work factors set too low
- Using deprecated algorithms
- Timing attacks that leak information
- Side-channel attacks against implementation
- Failure to upgrade algorithms as vulnerabilities emerge
Password Predictability
Human-generated passwords tend to follow predictable patterns, making them vulnerable to smart dictionary attacks regardless of hashing strength:
- Dictionary words with simple substitutions ("P@ssw0rd")
- Common patterns ("123456", "qwerty")
- Predictable modifications to meet requirements (adding "!" to the end)
Why Passwordless Authentication Is the Future
Given these persistent challenges, the industry is increasingly turning to passwordless authentication methods:
Advantages of Passwordless Approaches
- Eliminates credential stuffing: Without passwords, there's nothing to stuff
- Removes password management burden: No more forgotten passwords or reset processes
- Improves user experience: Faster, more convenient login experiences
- Reduces attack surface: Eliminates entire categories of password-related vulnerabilities
- Leverages stronger authentication factors: Physical devices and biometrics can be more secure than memorized secrets
Common Passwordless Methods
- Magic links: One-time email links for authentication
- Authenticator apps: Time-based one-time passwords (TOTP)
- FIDO2/WebAuthn: Standard for cryptographic authentication using security keys or platform authenticators
- Biometrics: Fingerprints, facial recognition, voice patterns
- Push notifications: Prompts sent to trusted devices
Real-World Implementations
Many major platforms are already moving toward passwordless:
- Microsoft: Pushing "passwordless account" options across their ecosystem
- Google: Advanced Protection Program and security key integration
- Apple: PassKeys in iCloud Keychain
- Enterprise environments: Increasingly adopting FIDO2 security keys
The Future of Authentication with AI
As authentication continues to evolve, artificial intelligence will play an increasingly important role:
AI-Enhanced Threat Detection
- Behavioral biometrics: Learning how users type, move their mouse, or hold their mobile devices
- Anomaly detection: Identifying login attempts that deviate from established patterns
- Continuous authentication: Monitoring user behavior throughout sessions rather than just at login
- Adaptive challenge selection: Dynamically choosing appropriate authentication challenges based on risk assessment
AI for Attackers
The threat landscape is also evolving with AI:
- Password generation: Using machine learning to generate more human-like password guesses
- Behavior mimicry: Potential for sophisticated attacks that simulate legitimate user behavior
- Deepfakes: Synthetic media potentially bypassing biometric systems
- Adversarial attacks: Finding weaknesses in AI-based authentication systems
The Evolution of Multi-Factor Intelligence
Future authentication systems will likely combine multiple signals with AI-driven analysis:
- Context awareness: Considering location, device, network, and time of access
- Risk-based authentication: Adjusting security requirements based on transaction risk
- Passive signals: Using background information that doesn't require explicit user action
- Social and behavioral patterns: Recognizing typical usage patterns across services
Challenges on the Horizon
The integration of AI into authentication brings its own challenges:
- Privacy concerns: Balancing data collection for security with user privacy
- Transparency: Making AI-based decisions understandable to users and administrators
- Inclusivity: Ensuring systems work equitably across diverse user populations
- AI security: Protecting AI systems themselves from manipulation and attack
- Regulatory compliance: Meeting emerging requirements for AI-based security systems
Conclusion
Password hashing and salting represent important foundations of digital security, transforming vulnerable plain text passwords into protected formats that mitigate many risks. However, as we've seen, even the most sophisticated implementation of these techniques cannot fully protect against human behaviors like password reuse or the relentless advance of computing power.
The future of authentication lies beyond passwords, embracing passwordless methods that eliminate entire categories of attacks. As AI continues to develop, we'll see increasingly sophisticated systems that balance security with usability, adapting to both user behavior and emerging threats.
For organizations still relying on password-based authentication, implementing proper hashing and salting remains essential. But forward-looking security strategies should include a roadmap toward reducing password dependence and embracing stronger, more usable authentication methods.
The evolution of authentication isn't just about technical solutions—it's about creating security that works with human behavior rather than against it. As we continue this journey, the combination of cryptographic best practices, passwordless technologies, and intelligent systems will shape the future of how we prove our digital identities.

