The Future of AI Agent Authentication: Ensuring Security and Privacy in Autonomous Systems
Dive into the world of AI agent authentication, where cutting-edge security meets autonomous systems. Discover how delegation tokens, real-time verification, and multi-layer security protocols work together to ensure safe and private AI operations while maintaining operational efficiency.

Artificial intelligence is becoming increasingly autonomous, the need for robust authentication and security mechanisms for AI agents has never been more critical. This comprehensive analysis explores how AI agents can securely authenticate in real-time while maintaining data privacy and security, drawing from cutting-edge research and practical implementations.
Understanding AI Agent Authentication
AI agent authentication is fundamentally different from traditional user authentication. While human users can rely on passwords, biometrics, or two-factor authentication, AI agents require a more complex system that validates both their identity and their authorization to act on behalf of users or organizations.
Key Components of AI Agent Authentication:
- Identity Verification: Establishing the authentic identity of both the AI agent and the delegating user
- Delegation Management: Controlling what actions an AI agent can perform
- Access Control: Managing and restricting access to resources and services
- Audit Trail: Maintaining comprehensive logs of all agent actions and authentications
The Authentication Framework
The modern AI agent authentication framework consists of three primary components:
a) User's ID Token
The User's ID Token serves as the foundational element of the authentication system. This token represents the verified identity of the human user who is delegating authority to the AI agent. Identity providers like Google, Microsoft, or enterprise authentication systems issue these tokens after thorough verification of the user's credentials.
The token contains essential information about the user, including their verified identity attributes, authorization levels, and organizational affiliations. These tokens integrate seamlessly with existing identity management systems, allowing organizations to maintain consistent access control policies across both human and AI agent interactions.
- Represents the human user's identity
- Issued by trusted authentication providers
- Contains verified user information
- Links to existing identity management systems
b) Agent ID Token
The Agent ID Token functions as a digital passport for the AI agent itself. Unlike simple identifiers, this token contains comprehensive information about the agent's capabilities, limitations, and operational boundaries.
The token includes detailed system documentation that describes the agent's intended functions, its training parameters, and any known limitations in its capabilities. This documentation is crucial for services to understand what the agent can and cannot do reliably.
The token also specifies the agent's relationships with other systems and services, enabling complex multi-agent interactions while maintaining security boundaries.
- Unique identifier for the AI agent
- Contains agent capabilities and limitations
- Includes system documentation
- Specifies relationship attributes with other systems
c) Delegation Token
The Delegation Token acts as the bridge between the user and the AI agent, explicitly defining the scope of authority granted to the agent. This token contains cryptographic references to both the user's ID token and the agent's ID token, creating an unbreakable chain of delegation.
Within the delegation token, detailed permission sets specify exactly what actions the agent can perform, under what conditions, and for how long. The token includes validity conditions such as time limits, geographic restrictions, or resource usage caps. These conditions can be dynamically updated to respond to changing security requirements or risk levels.
- Explicitly authorizes agent actions
- References both user and agent tokens
- Defines scope and permissions
- Includes validity conditions and expiration
Real-Time Authentication Process
The authentication process follows a structured flow to ensure security at every step:
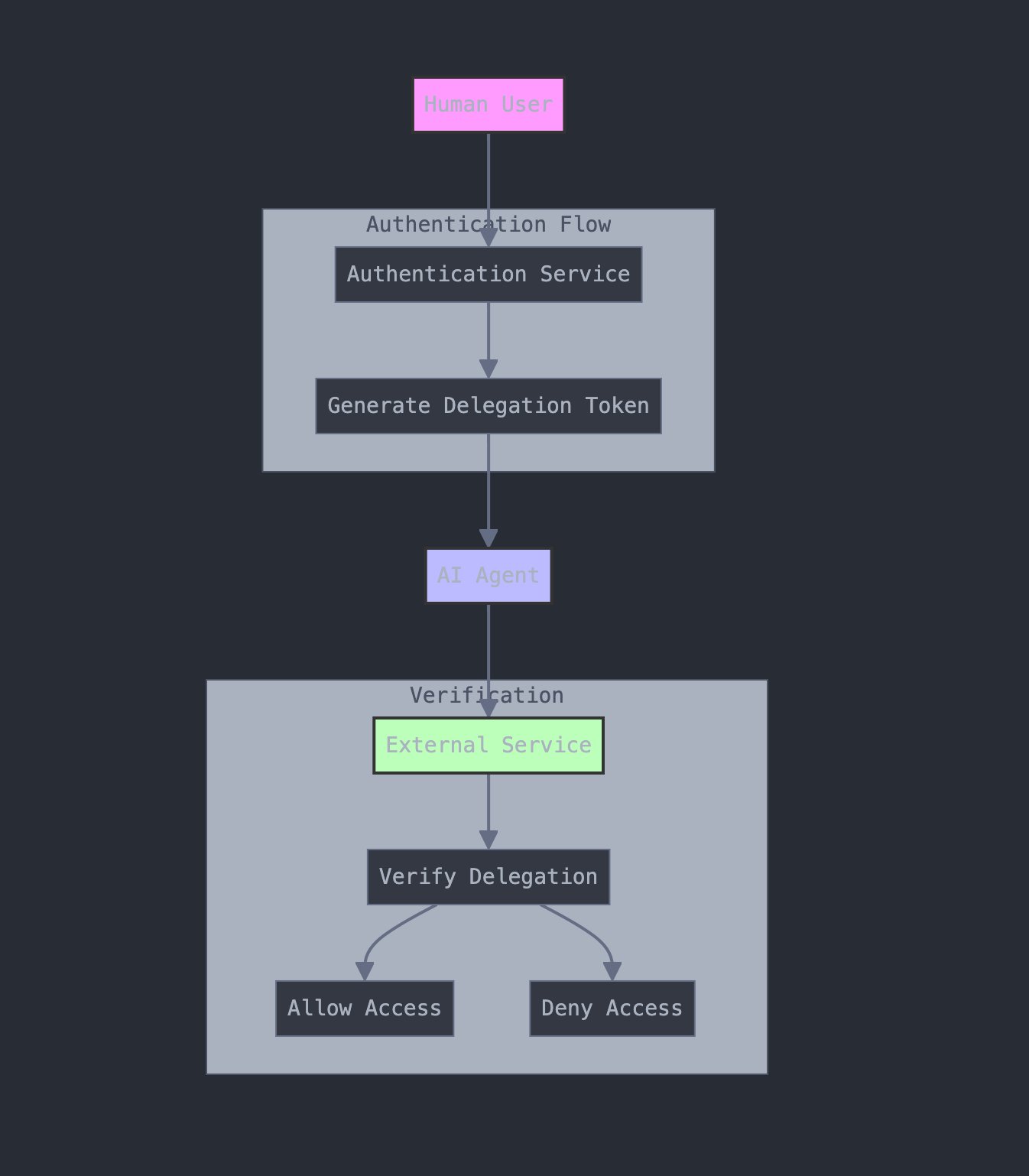
Initial Setup:
- User authenticates with an OpenID Provider
- User registers the AI agent with the provider
- Provider issues necessary tokens and credentials
Operation Flow:
- AI agent receives a task from the user
- Agent presents delegation credentials to target service
- Service verifies credentials with the OpenID Provider
- Access is granted based on defined permissions
- Actions are logged for accountability
- Security Mechanisms
Multiple security layers protect the authentication system:
Layer 1: Identity Protection
This layer involves multiple sophisticated mechanisms working together to ensure the authenticity and integrity of all participants. Digital signatures, based on strong cryptographic algorithms, protect every token from tampering or forgery. These signatures use industry-standard protocols like RSA or ECDSA, with key lengths that meet or exceed current security recommendations.
The cryptographic linking between credentials creates a verifiable chain of trust from the user through to the agent's actions. This chain allows any party to validate the complete authorization path. The token structure itself includes tamper-evident features that make any unauthorized modifications immediately detectable. Regular credential rotation policies ensure that even if credentials are compromised, the window of vulnerability remains limited.
- Digital signatures for all tokens
- Cryptographic linking between credentials
- Tamper-evident token structure
- Regular credential rotation
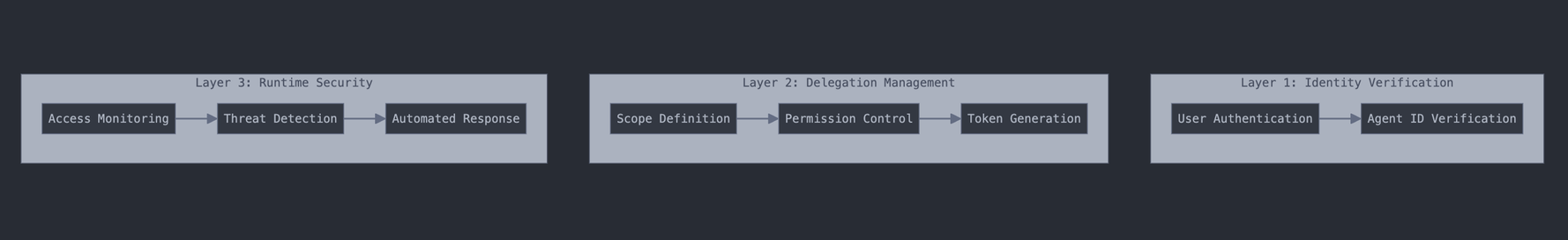
Layer 2: Access Control
This layer implements a sophisticated, context-aware authorization system. The fine-grained permission management allows organizations to specify exactly what resources an agent can access, down to individual API endpoints or data fields. The context-aware authorization system takes into account factors like time of day, location, current system load, and recent activity patterns when making access decisions.
Resource-specific restrictions can limit not just access, but also the rate of requests, the types of operations allowed, and the volume of data that can be processed. Time-bound access tokens ensure that permissions automatically expire after a predetermined period, requiring regular revalidation of the agent's authority.
- Fine-grained permission management
- Context-aware authorization
- Resource-specific restrictions
- Time-bound access tokens
Layer 3: Monitoring and Response
This layer provides continuous oversight of agent activities. Real-time monitoring systems track every authentication attempt and subsequent action, building a detailed profile of normal behavior patterns.
Advanced anomaly detection algorithms analyze this activity stream, identifying potential security threats or policy violations. When suspicious activity is detected, automated response systems can take immediate action, from requiring additional verification to temporarily suspending access privileges. The continuous authentication process ensures that agents must regularly revalidate their credentials, preventing any single compromise from having long-term impact.
- Real-time activity monitoring
- Anomaly detection
- Automated threat response
- Continuous authentication
Privacy Considerations
Privacy protection is built into the authentication framework through several mechanisms:
Data Minimization
Data minimization forms the cornerstone of privacy protection in AI agent authentication. Rather than collecting and storing all possible information, the system carefully selects only the essential data points required for each specific interaction.
For example, when an AI agent needs to access a customer service database, its credentials might include authorization for customer data access without revealing internal system architectures or unrelated business data. This selective information sharing significantly reduces the potential impact of any security breach while maintaining functional effectiveness.
- Only essential information is included in tokens
- Selective disclosure of agent capabilities
- Purpose-specific credentials
- Temporary access grants
Information Flow Control
The information flow control system acts as a sophisticated traffic controller for sensitive data. When an AI agent initiates communication with a service, the system establishes encrypted channels using industry-standard protocols like TLS 1.3. These channels ensure that all credential exchanges and subsequent communications remain private and secure.
The system implements strict controls on data sharing between services, requiring explicit authorization for any cross-service information exchange. Each service operates within its own isolated execution environment, preventing unauthorized data leakage between different parts of the system.
- Controlled data sharing between services
- Privacy-preserving credential verification
- Isolated execution environments
- Encrypted communication channels
Key Use Cases
Let's explore four primary use cases for autonomous AI agent authentication:
A. Enterprise Resource Access
Enterprise Resource Access represents one of the most common applications for AI agent authentication. In a typical enterprise scenario, AI agents need to interact with various internal systems, from document management to customer relationship databases.
The authentication process begins when the organization's identity provider verifies the agent's credentials and delegation token. The system then applies role-based access control policies, which define specific permissions based on the agent's assigned role and the task at hand.
- Scenario: AI agents accessing internal systems and databases
- Authentication: Role-based access control with delegated permissions
- Security: Strict monitoring of data access and modifications
- Privacy: Compartmentalized access to sensitive information
Example: An AI agent handling customer support tickets might receive authorization to access customer histories and common resolution templates, but not financial records or employee data. The system maintains detailed logs of every access attempt and action taken, enabling comprehensive audit trails for compliance and security purposes. Privacy protection mechanisms ensure that sensitive customer information remains segregated and accessible only on a need-to-know basis.
B. Financial Transactions
Financial transactions require particularly robust authentication mechanisms due to their sensitive nature. When an AI agent initiates a financial transaction, it must first present multiple forms of verification, including its delegation token, transaction-specific authorization, and any applicable spending limits.
The system performs real-time risk assessment, analyzing factors such as transaction patterns, amount thresholds, and recipient verification before approving any movement of funds.
- Scenario: AI agents managing payments and transactions
- Authentication: Multi-factor verification with transaction limits
- Security: Real-time fraud detection and prevention
- Privacy: Encrypted transaction details and secure audit trails
Example: An AI agent managing expense approvals: it might have authority to approve routine expenses up to a certain amount, but require additional human authorization for larger transactions or unusual patterns. The system encrypts all transaction details and maintains secure audit trails that can be used for financial reconciliation while preserving privacy and confidentiality.
C. Healthcare Systems
Healthcare implementations demonstrate how AI agent authentication can comply with strict regulatory requirements like HIPAA. The authentication system incorporates multiple layers of verification before granting access to patient records or medical systems.
Each access request is evaluated against both the agent's credentials and specific patient consent records, ensuring compliance with privacy regulations.
- Scenario: AI agents accessing patient records and medical systems
- Authentication: Strict identity verification and HIPAA compliance
- Security: Comprehensive access logging and audit trails
- Privacy: Patient data protection and controlled information sharing
Example: An AI agent assisting with medication management would need to prove its authorization to access specific patient records, verify its credentials for medication-related tasks, and document every interaction in compliance with healthcare regulations. The system maintains strict separation between different patients' data and enforces role-based access controls that limit exposure to sensitive information.
D. Multi-Agent Collaboration
Multi-agent collaboration scenarios present unique challenges in authentication and security. When multiple AI agents work together on complex tasks, each agent must not only verify its own credentials but also validate the authenticity and permissions of other agents it interacts with.
The system establishes secure communication channels between agents and maintains careful control over information sharing.
- Scenario: Multiple AI agents working together on complex tasks
- Authentication: Cross-verification of agent credentials
- Security: Monitored interaction between agents
- Privacy: Controlled information sharing between agents
Implementation Challenges and Solutions
Scale and performance challenges in AI agent authentication require sophisticated architectural solutions. Modern systems use distributed authentication architectures with strategic caching mechanisms to handle millions of simultaneous authentication requests. Load balancers distribute requests across multiple identity providers, ensuring consistent performance even during peak usage periods. Regular performance monitoring helps identify bottlenecks and optimization opportunities, allowing the system to scale efficiently with increasing demand.
Security threats continue to evolve, requiring adaptive defense mechanisms. The multi-layer security architecture includes protective measures at each level of the system, from network security to application-level controls. Continuous security monitoring uses advanced analytics to detect potential threats, while automated response systems can immediately revoke compromised credentials or adjust security parameters based on detected risk levels.
Common challenges in implementing AI agent authentication include:
Scale and Performance:
- Challenge: Managing millions of simultaneous authentications
- Solution: Distributed authentication systems with caching
- Implementation: Load-balanced identity providers
- Monitoring: Performance metrics and optimization
Security Threats:
- Challenge: Protection against sophisticated attacks
- Solution: Multi-layer security architecture
- Implementation: Continuous security monitoring
- Response: Automated threat mitigation
Privacy Protection:
- Challenge: Maintaining data privacy across systems
- Solution: Privacy-preserving authentication protocols
- Implementation: Encrypted credential exchange
- Verification: Regular privacy audits
Future Developments
The integration of quantum-resistant cryptography prepares authentication systems for future security challenges. As quantum computing capabilities advance, traditional encryption methods may become vulnerable to new types of attacks. Authentication systems are beginning to implement post-quantum cryptographic algorithms that can withstand attacks from both classical and quantum computers.
Blockchain-based credential verification offers promising advantages for distributed trust and verification. By recording credential issuance and verification events on a blockchain, systems can create immutable audit trails and enable decentralized verification of agent credentials. This technology could revolutionize how we manage trust in autonomous systems while maintaining privacy and security.
The future of AI agent authentication will likely include:
- Quantum-resistant cryptography
- Blockchain-based credential verification
- Zero-knowledge proofs for privacy
- Adaptive authentication systems
Conclusion
AI agent authentication is a critical component of secure autonomous systems. By implementing robust authentication frameworks with strong security measures and privacy protections, organizations can safely deploy AI agents while maintaining control and accountability. The key is to balance security requirements with operational efficiency while ensuring complete privacy protection.
As AI agents become more prevalent in our digital infrastructure, the importance of secure authentication will only increase. Enterprises must stay current with evolving security standards and privacy requirements while maintaining the flexibility to adapt to new threats and challenges.
Organizations that successfully implement and maintain effective AI agent authentication systems will be better positioned to leverage autonomous technologies while managing associated risks. The key to success lies in maintaining a proactive approach to security and privacy while remaining flexible enough to adapt to changing requirements and emerging threats.

