The Art and Science of Prompt Engineering: Mastering AI Interactions for Exceptional Results
While most struggle with generic AI responses, elite prompt engineers command it. Why? They extract 10x value from same AI models everyone else uses. This guide reveals four-level framework to elevate your prompting skills from basic queries to sophisticated systems that solve real problems.
"I just saved 20 hours of work with a single, well-crafted prompt."
This isn't a marketing claim—it's the new reality for professionals who've mastered prompt engineering. While most struggle with generic AI outputs, a select few are unlocking exponentially better results by speaking the language AI understands.
The difference between mediocre and exceptional AI performance isn't in the model—it's in how you communicate with it. Organizations now pay $300,000+ for skilled prompt engineers because the ROI is undeniable: better outputs in less time with fewer iterations.
In a world where 79% of enterprise leaders call AI a "game-changer," the competitive advantage lies not in having AI access, but in extracting its maximum value. Every suboptimal prompt costs you time, accuracy, and opportunities your competitors might be seizing.
This isn't just another tech skill—it's the new business literacy. Let me show you how to master it.
Understanding Prompt Engineering
Prompt engineering is more than just typing questions into a chatbox. It's a methodical approach to constructing inputs that guide AI systems toward producing precisely what you need. Think of it as learning to communicate with an incredibly powerful but sometimes literal-minded collaborator who needs clear, structured guidance to deliver its best work.
The quality of your prompts directly determines the value of the AI's response. This relationship is so critical that organizations are now hiring dedicated prompt engineers with salaries exceeding $300,000 annually—highlighting just how valuable this skill has become in the AI ecosystem.
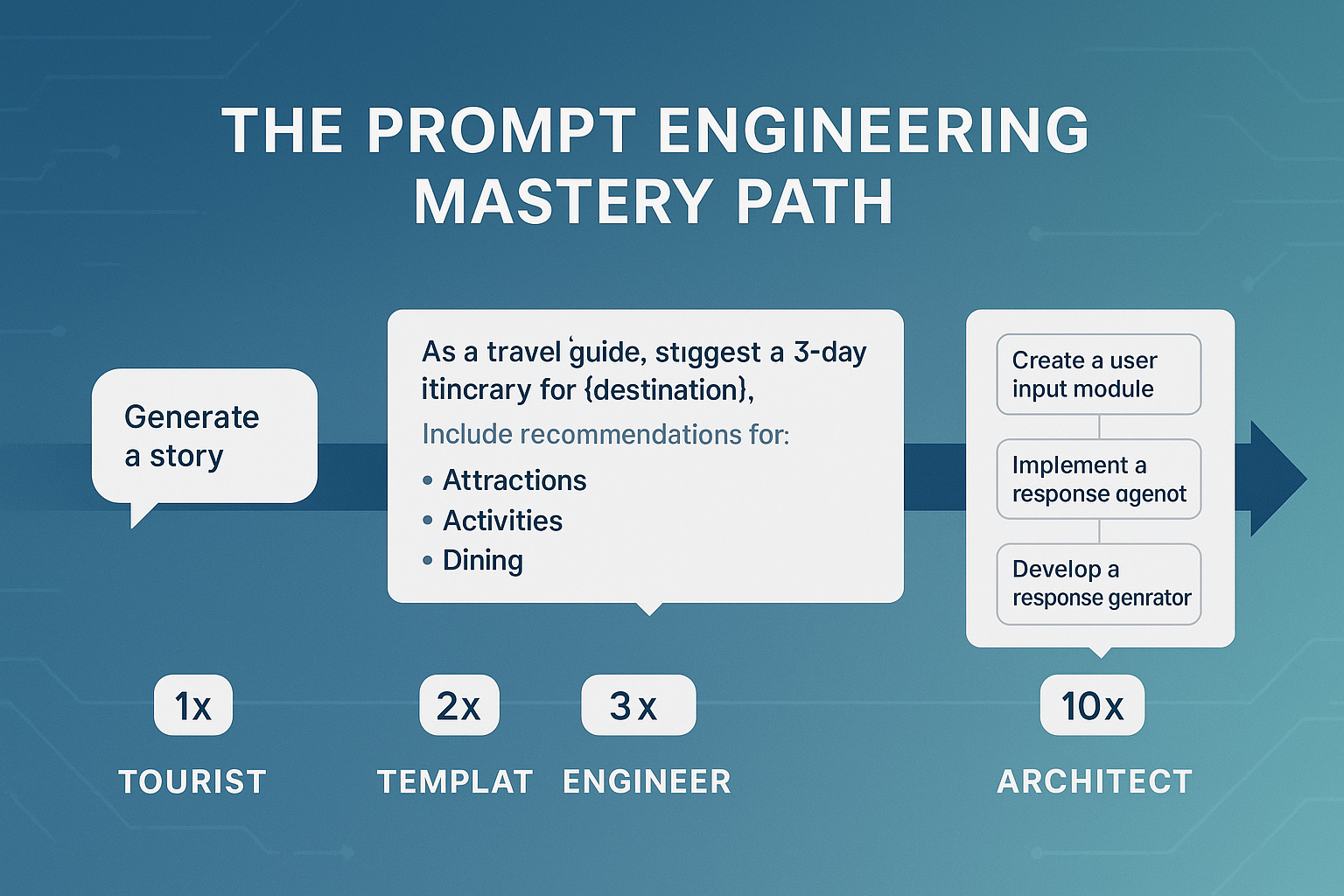
The Four Levels of Prompt Engineering Expertise
Like any technical discipline, prompt engineering has distinct levels of mastery. Understanding where you currently stand can help you chart a path toward greater proficiency.
Level 1: The Tourist
At this foundational level, users typically input simple, unstructured queries:
Write a blog post about cybersecurity.
These basic prompts leave almost everything to the AI's interpretation. While you might occasionally get useful results, outcomes are inconsistent and rarely aligned with specific needs. The Tourist approach is characterized by:
- Single-sentence prompts
- Vague instructions
- Reactive refinement ("No, make it shorter" or "Add more examples")
- Limited control over output quality and format
Real-world example: An enterprise security manager quickly asks an AI to "write a security protocol document" without specifying audience, compliance requirements, or implementation context—resulting in a generic document that requires extensive editing.
Better approach: Even simple refinements like "Write a 500-word blog post about zero-trust security architecture for financial institutions" provide significantly better direction.
Level 2: The Template User
At this level, users recognize that structure matters and begin incorporating specific parameters:
Write a 1200-word technical article on AI-powered threat detection. Include 5 real-world examples, 3 implementation challenges, and formatting with headers and bullet points. Target audience is IT directors at mid-sized enterprises.
Template Users have developed mental models for effective prompts and apply them consistently. Key characteristics include:
- Specified length and format requirements
- Target audience identification
- Basic structural elements (sections, examples, challenges)
- Reusable prompt patterns across similar tasks
Real-world example: A product manager creates a template for generating feature comparison tables, saving hours of manual research by specifying exact products, feature categories, and output format.
Better approach: While this level produces more consistent results, it still treats the AI as a content generator rather than a thinking partner. The next levels address this limitation.
Level 3: The Engineer
Engineers approach prompt design with precision and strategic intent:
You are a senior cybersecurity analyst with 15+ years of experience in financial services.
First, identify the three most critical emerging threats to cloud-based financial applications in 2025 (1-2 sentences each).
Then, for the most sophisticated threat, provide:
1. A technical breakdown of attack vectors
2. Real-world breach example with impact metrics
3. A defense framework using zero-trust principles
Format your analysis with clear headings, concise paragraphs, and include a technical complexity rating (1-5) for each recommended countermeasure.
Your response should balance technical depth with actionable insights. Prioritize novel approaches over common knowledge.
At this level, practitioners recognize that how you structure a prompt fundamentally shapes the AI's approach. Key techniques include:
- Role prompting: Assigning specific expertise personas to the AI
- Instruction layering: Breaking complex tasks into sequential steps
- Output formatting: Explicitly defining response structure
- Constraint definition: Setting boundaries that guide quality ("balance technical depth with actionable insights")
- Evaluation criteria: Building in quality standards ("prioritize novel approaches over common knowledge")
Real-world example: A CISO uses carefully engineered prompts to generate threat models that integrate the latest CVE data with company-specific architecture vulnerabilities, resulting in prioritized mitigation strategies that align with organizational resources.
Level 4: The Architect
Architects don't just write prompts—they design systems that leverage AI as computational components:
[System instruction layer]
You are CyberInsightAgent, specialized in translating complex security data into business risk assessments. You follow a structured analytical protocol:
1. Examine raw security data input
2. Categorize findings by MITRE ATT&CK framework
3. Calculate exploitation probability (Low/Medium/High) based on industry benchmarks
4. Map technical vulnerabilities to business impact using the organization's critical asset inventory
5. Generate prioritized recommendations with implementation complexity and resource requirements
[Context layer]
The organization is a healthcare provider with 5000 employees, subject to HIPAA compliance. Their critical systems include:
- Patient records database (Oracle)
- Telehealth platform (AWS-hosted)
- Internal communications (Microsoft 365)
- IoT medical devices (various vendors)
[Task layer]
Analyze the attached vulnerability scan results. Focus particularly on potential lateral movement paths between network segments. Generate a comprehensive risk assessment report for board-level presentation.
[Output constraints]
- Executive summary limited to 250 words
- Technical findings must include exploitation pathways
- Each recommendation must include estimated implementation effort (person-hours) and priority level
- Include visualizations where appropriate
Architects build sophisticated prompt ecosystems that may include:
- Multi-agent systems: Designing specialized AI agents that collaborate on complex problems
- Chain-of-thought architectures: Building prompts that guide the AI through explicit reasoning steps
- Tool integration: Combining AI capabilities with external data sources, APIs, and specialized tools
- Feedback loops: Creating systems where AI outputs are evaluated and refined through iterated prompting
- Context management: Strategically providing and updating relevant information throughout interactions
Real-world example: A cybersecurity team builds an integrated threat intelligence system where specialized AI agents continuously monitor, classify, and respond to security events—with one agent identifying anomalies, another researching relevant threat actors, and a third generating mitigation recommendations that are automatically prioritized and routed to appropriate team members.
Practical Techniques for Elevating Your Prompt Engineering
Regardless of your current level, these techniques can significantly improve your results:
1. Chain-of-Thought Prompting
Guide the AI to show its reasoning process step by step. This technique dramatically improves accuracy for complex analytical tasks:
Analyze the following cybersecurity incident:
[incident details]
Think through this step by step:
1. First, identify the initial attack vector and how it was exploited
2. Then, determine how the attacker established persistence
3. Next, analyze lateral movement techniques used
4. Finally, assess data exfiltration methods and potential impact
For each step, consider what evidence supports your conclusions and what alternative explanations might exist.
2. Few-Shot Learning
Provide examples of what good outputs look like before asking for a new one:
Here are two examples of well-structured vulnerability reports:
EXAMPLE 1:
[Title: CVE-2023-XXXX SQL Injection in Authentication Module]
Severity: Critical (CVSS 9.8)
Affected systems: All production web servers running v3.2.1
Description: Authentication bypass possible through malformed login parameters
Exploitation method: Specially crafted POST request to /auth/login endpoint
Business impact: Unauthorized access to all customer accounts and financial data
Remediation: Apply patch KB-23456 (effort: 4 hours, downtime: 15 minutes)
EXAMPLE 2:
[detailed second example]
Using exactly this format and level of detail, create a vulnerability report for the following issue:
[new vulnerability details]
3. Dynamic Refinement
Rather than trying to craft a perfect prompt initially, implement an iterative approach:
I need to develop a comprehensive security awareness training program. Let's approach this step by step.
First, outline the 5 most critical security awareness topics for our organization based on current threat landscapes.
After receiving the response:
Thank you. Now, for the "phishing awareness" topic, develop a detailed training module outline that includes:
1. Learning objectives
2. Key concepts to cover
3. Interactive exercises
4. Assessment methods
5. Reinforcement strategy
This approach allows you to build complexity progressively while maintaining control over the direction.
4. Context Framing
How you frame the context dramatically affects results. Compare:
Basic framing:
Write a security policy for password management.
Advanced context framing:
You are developing a password policy for a healthcare organization that must comply with HIPAA and NIST 800-63B guidelines. The organization has:
- 5,000 employees across clinical and administrative roles
- Legacy systems that cannot support passwordless authentication
- A recent breach attributed to password reuse
Create a comprehensive password policy that balances security requirements with usability considerations for healthcare workers who may need emergency access.
The contextual details enable the AI to generate significantly more relevant and applicable content.
Real-World Applications Across Organization Types
For Enterprise Security Teams
Automated Vulnerability Analysis:
Analyze this vulnerability scan output for our e-commerce platform. Identify the top 5 critical vulnerabilities based on:
1. Potential business impact (revenue loss, data breach costs, reputation damage)
2. Exploitation likelihood in our industry
3. Remediation complexity
For each vulnerability, suggest concrete remediation steps with estimated level of effort.
Compliance Documentation Generation:
You are a GDPR compliance specialist. I need to create a Data Protection Impact Assessment (DPIA) for our new customer analytics platform that processes European customer data.
Walk through each required DPIA section, asking me relevant questions about our system architecture, data flows, and existing safeguards. Then generate appropriate documentation based on my answers.
For Startup Founders
Competitive Analysis:
I'm launching a cybersecurity SaaS startup focused on [specific niche].
First, identify the 5 leading competitors in this space and analyze their:
- Key differentiators
- Pricing models
- Target customer segments
- Go-to-market strategies
Then, identify 3 potential market positioning opportunities where current solutions are inadequate. For each opportunity, suggest a potential product feature set that would address this gap.
Investment Pitch Preparation:
You are a cybersecurity VC investor with technical background. I'm preparing to pitch my AI-powered security orchestration platform to investors.
Review my value proposition:
[paste value prop]
1. Identify the 3 strongest elements and 3 weakest elements from an investor's perspective
2. Suggest improvements to address potential objections
3. Recommend which technical capabilities I should prioritize demonstrating in a limited demo
4. Propose 5 questions investors are likely to ask and help me craft compelling answers
For Product Managers
Feature Prioritization:
I'm a product manager for a cybersecurity platform with these upcoming features:
1. [Feature A description]
2. [Feature B description]
3. [Feature C description]
Help me prioritize these features by:
1. Creating a decision matrix with criteria including development effort, revenue potential, competitive advantage, and customer impact
2. Assigning weights to each criterion based on our growth stage
3. Systematically evaluating each feature against these criteria
4. Recommending an implementation sequence with rationale
User Story Development:
As a product manager for an identity management solution, I need to develop comprehensive user stories for our new passwordless authentication feature.
For each of these user types:
- Enterprise administrator
- End user (non-technical)
- Security analyst
- Help desk support
Create 3-5 detailed user stories in standard format:
"As a [user type], I want to [action/capability] so that [benefit]"
Include acceptance criteria and potential edge cases for each story.
Building Your Prompt Engineering Skills: A Progressive Exercise Plan
To systematically improve your prompt engineering capabilities, try this four-step exercise plan:
Step 1: Tourist to Template User
Exercise: Take 5 simple prompts you've used in the past and enhance them with specific parameters:
- Add word count requirements
- Specify audience and purpose
- Include format instructions (headers, sections, etc.)
- Define tone and style preferences
Compare the results between your original and enhanced prompts.
Step 2: Template User to Engineer
Exercise: Select 3 complex topics in your domain and create engineered prompts that include:
- Role assignment for the AI
- Step-by-step instruction sequencing
- Output format specifications
- Quality constraints
- Evaluation criteria
Test your prompts and iterate based on results.
Step 3: Engineer to Architect (Foundations)
Exercise: Design a multi-stage prompting workflow for a complex project:
- Create a planning prompt that outlines the approach
- Develop specialized prompts for different components of the project
- Build a synthesis prompt that integrates outputs from the component prompts
- Add a quality assurance prompt that evaluates the final product
Execute your workflow on a real project and document improvements.
Step 4: Advanced Architectural Patterns
Exercise: Implement at least two of these advanced patterns:
- Design a system with multiple specialized AI agents that collaborate on a complex problem
- Create a prompt that integrates external data sources and guides the AI in analyzing them
- Develop a feedback loop system where outputs are evaluated and refined through iteration
- Build a dynamic context management system that updates relevant information throughout a complex interaction
Conclusion: The Future of Human-AI Collaboration
As AI systems continue to evolve, prompt engineering will become an increasingly critical skill across virtually every industry. Those who master the art and science of effective prompting will gain significant advantages in productivity, innovation, and problem-solving capabilities.
The progression from Tourist to Architect represents more than just technical skill development—it reflects a fundamental shift in how we conceptualize human-AI collaboration. At the most advanced levels, we move from treating AI as a tool to engaging with it as a cognitive partner in complex problem-solving.
Whether you're an enterprise leader integrating AI capabilities across your organization, a startup founder leveraging AI for competitive advantage, or a technology professional enhancing your productivity, deliberate practice in prompt engineering will yield substantial returns on investment.
The most successful organizations and individuals in the coming decade will not necessarily be those with exclusive access to AI technology, but rather those who most effectively learn to communicate with, direct, and collaborate with these powerful systems. The journey from basic prompting to sophisticated prompt architecture is one well worth taking.
Remember: The quality of your outputs is directly proportional to the quality of your inputs. Invest in mastering prompt engineering, and you'll unlock capabilities that fundamentally transform how you work, innovate, and solve problems.

