Guide to Digital Identity — Part 1
Are you curious about the Digital Identity Ecosystem? If you have been looking for a good, reliable and easy-to-understand source of information and haven’t had any luck, then this article is for you.
We live in a digital age and consequently, our Digital Identity plays an increasingly important role in defining our physical identity — an entity that is becoming richer and more complex every day.
Wondering what has contributed to this change? Well, digital adoption from mobile usage and the introduction of new authentication regulations have been playing a crucial role.
Digital Identity is the new focus for many businesses, regulators, and governments in a data-driven and hyper-connected world. The concept can be seen as an integration of two components — belongingness and separation.
How Are Digital Identities Created
Digital Identity is composed of data that describes a person or a thing in a unique fashion. It is the information that defines the relationship of the person with other entities in a digital environment.
It may include personal details, online search activities, purchasing history, and the geographical location of a person. It is used to identify and authenticate a person to access diverse physical or computing resources.
The idea of Digital Identity in a computing environment revolves around:
- Identity registration
- Identity verification
- Service access
- A community of users
- Business partnerships across the world
- Digital development
- Identity management, and so on
Moving on, let’s talk about the Geographical and Personal identities, what they are and what role they play in today’s digital world.
Geographical Identity
When the digital or physical identity is attached to the country, region, or city in which the user lives, it becomes a Geographical Identity.
When we link the geographical identity with the digital world like web browsers, which contain information in the form of cookies (such as IP address, city, country, zip code along with other details), it becomes easy to identify users across the Internet.
Personal Identity
Data that can disclose information about a person is categorized as Personal Identity. It includes an individual’s name, date of birth (DOB), age, language(s) spoken, email address, user IDs, gender, biometrics, etc.
Personal identity is used by individuals to log into websites or web accounts, such as Facebook, Gmail, LinkedIn, etc.
Next, let’s talk about the evolution and concepts of Digital Identity.
Evolution of Digital Identity
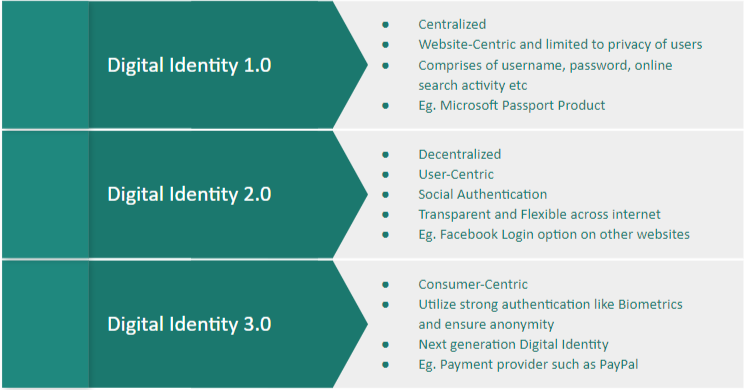
Digital Identity 1.0 laid the foundation for logging into websites using usernames and passwords. It was followed by Digital Identity 2.0 that allowed users to log into websites using their existing social account credentials.
Now, we are in the age of next-generation Digital Identity 3.0, where the gap between a person’s real and virtual identity is narrowing. It is accompanied by new and secure protocols, enhanced authentication mechanisms like biometrics, and innovative real-time applications including online banks, e-wallet, etc.
Concepts of Digital Identity
The following concepts are associated with Digital Identity:
- Identifier — An identifier distinguishes an individual or thing in a specific context. For example, a debit card can be considered as an identifier for a person holding a bank account.
- Attribute — An attribute is a specific characteristic related to an individual or a thing. Attributes can be temporary or permanent. For example, Social Security Number (SSN), biometric data, DOB, etc.
- Identification — Identification is the process by which individuals claim their identity. In the digital world, identification in a network occurs based on both the individual and the digital or computing device(s). It involves associating the identifier with the individual or the device.
- Authentication — Authentication is the process in which the claimed identity is verified based on which access to resources is granted or denied. In other words, it involves proving the association of the identifier with the individual.
- Authorization — Authorization is the decision process that allows a person to perform certain actions based on the identifier. It depends upon authentication, as giving control over resources requires the need to verify the identity first.
Authentication and Authorization are two key components of Digital Identity and play a crucial role in establishing security and trust between the real and the virtual world.
Let’s dive into the means of authentication. Typically, authentication is based on one or more of the following factors:
- Something you know — a password
- Something you have — a mobile phone or a security token
- Something you are — fingerprint or retina
- Something you do — typing speed or your locational information etc.
Below are the various authentication methods revolving around the above factors:
- Password-Based Authentication
In this method, a user first creates an account by providing the required information, such as email address, username, phone number, and password, and then uses the information to access the account.
It uses something you know (password or pin) factor.
2. Passwordless Authentication / Instant Login
With this form of authentication, a user is presented with the option of either logging in simply via a magic link or using an OTP that is delivered via email or text message.
The popular means of Passwordless Authentication are:
- Email and Magic Link: A link to log in sent to the registered email address.
- Email and OTP: An OTP to log in sent to the registered email address.
- Phone and OTP: An OTP to log in sent to the registered phone number.
- One-Touch Login/No Registration Login: A link or OTP sent to the provided email address or phone number. This method does not require registration.
It uses something you have (email or phone number) factor.
3. Social Login
This method involves signing in into third party websites using already existing credentials for social networking websites like Facebook, Twitter, Google, Microsoft, etc.
The user is not required to fill out a registration form in this case, and it uses something you have (social account) factor.
4. Delegated Authentication
This method involves delegating the authentication request to a different device. Upon successful authentication, the user is logged into the parent device. This feature is commonly used in smart TV apps, gaming consoles, IoT devices, etc.
5. Barcode Authentication
This method involves logging into the devices or the services by scanning a barcode without any manual typing. It is widely used by web applications to authenticate users and provide access.
For added security, this method can be used with two-factor authentication (2FA), i.e. the user first provides the password and then scans the barcode using an already linked mobile device.
It uses something you have (linked mobile device) factor.
6. Hardware Devices

This authentication method relies on a dedicated physical device like card swipe, fingerprint readers, retina scanners, etc.
The popular means of hardware devices authentication are:
- Biometric: This involves the use of unique biological characteristics of the individual for the verification of his identity. The biometric data of the user is captured and stored in the database which is then compared to confirm the authentication of the user.
This method uses something you are (fingerprint, retina, etc) factor.
Here are some common Biometric methods:
a. Fingerprint Authentication
b. Facial Recognition
c. Retina Scan
- Card Swipe: This involves using a physical card with a magnetic strip, microchip RFID, etc. The users authenticate themselves using their registered swipe cards. This method uses something you have (physical device) factor.
7. Two-Factor Authentication (2FA)
This form of authentication adds an extra layer of security to make sure that the users trying to gain access are who they say they are.
First, the user is required to enter the email/username and password, and then they need to provide another piece of information like OTP (one-time passcode), biometrics, etc.
Conceptually, it is a combination of two authentication factors (among something you know, something you have, something you are and something you do)
- RSA Token: Security tokens, also known as authentication tokens or cryptographic tokens, are physical devices given to authorized users of a computer system or services for authentication.
There are two types of RSA tokens: hardware tokens (a device with battery and display) or software tokens (OTP via authenticator app).
- SMS via Phone: This method involves the user’s phone. The user is first required to enter the email/username and password, and then the application sends the user a unique one-time passcode (OTP) via text message.
- Push Notification: It involves a 2FA app installed on a smartphone or desktop. The user is first required to enter the email/username and password, and then the application sends a push notification on the linked 2FA app for authentication.
The next article will cover an in-depth analysis of the above authentication methods — how they work, along with their general and industry-wise use cases.
Originally published at Medium.com