Grok AI Fundamentals: Core Concepts, Capabilities, and Technical Foundation

Definition and Purpose
Grok AI represents a significant evolution in conversational artificial intelligence, developed by xAI with the explicit goal of creating a more engaging, useful, and versatile AI assistant. At its core, Grok is a large language model (LLM) designed to understand and generate human language, answer questions, solve problems, and assist with a wide range of tasks through natural conversation.
What distinguishes Grok from many of its predecessors is its integrated access to real-time information via the internet, allowing it to provide current answers on recent events and developments beyond its training data. This capability addresses one of the most significant limitations of traditional LLMs—their knowledge cutoff dates.
The name "Grok" itself comes from Robert A. Heinlein's 1961 science fiction novel "Stranger in a Strange Land," where it means "to understand completely and intuitively." This naming reflects the system's aspiration to develop a deep, intuitive understanding of user queries and provide insightful, helpful responses that go beyond simple information retrieval.
Grok was designed with several core purposes in mind:
- To provide an AI assistant that can access and incorporate real-time information from the internet
- To deliver a more engaging, conversational experience with what xAI describes as a "rebellious" personality
- To offer an alternative to existing AI systems that Elon Musk has characterized as overly cautious and politically biased
- To advance the development of artificial general intelligence (AGI) through a "maximum truth-seeking" approach
As an AI system, Grok combines pre-trained knowledge with real-time information access to serve as a comprehensive assistant for research, problem-solving, content creation, and various specialized tasks.
Historical Context
Grok AI emerged from a confluence of technological developments and specific vision for how AI assistants should function:
Early Development (2023):
- Following Elon Musk's acquisition of Twitter (now X) and his departure from OpenAI (which he co-founded), Musk established xAI in March 2023 with the stated purpose of understanding the "true nature of the universe" and developing AI that is an alternative to the approaches of companies like OpenAI and Anthropic.
- The xAI team was assembled with researchers and engineers from organizations including DeepMind, OpenAI, Google Research, Microsoft Research, and Tesla.
Initial Release:
- Grok-1 was announced on November 4, 2023, and made available to a limited group of users as part of X's Premium+ subscription service.
- This first release positioned Grok as a conversational AI with real-time knowledge access via web browsing capabilities and a distinctive personality described as "rebellious" and willing to answer questions that other AI systems might refuse.
Subsequent Development:
- In March 2024, xAI announced Grok-1.5, a significant update that improved reasoning capabilities, reduced hallucinations, and enhanced the model's ability to follow complex instructions.
- April 2024 saw the introduction of Grok-1.5V, which added multimodal capabilities, allowing the model to understand and process images alongside text.
- Throughout 2024, xAI has continued to expand access to Grok while enhancing its capabilities and fine-tuning its performance across various tasks.
This rapid development timeline reflects xAI's aggressive approach to advancing AI technology and challenging established players in the field. Grok's evolution has been characterized by quick iterations and a focus on capabilities that differentiate it from competitors.
xAI Background
xAI (pronounced "X AI") is an artificial intelligence company founded by Elon Musk in March 2023, with the official announcement of the company coming in July 2023. The company was established with a distinctive mission that reflects Musk's vision for AI development.
Company Mission: xAI's stated mission is to "understand the true nature of the universe." More practically, the company aims to develop AI systems that:
- Pursue "maximum truth-seeking"
- Provide an alternative to what Musk has characterized as overly cautious and politically biased AI from other major developers
- Advance the path toward artificial general intelligence (AGI)
Leadership and Team:
- Founder and Executive Chairman: Elon Musk
- CEO: As of early 2025, leadership continues to evolve
- The technical team includes AI researchers and engineers with backgrounds from leading organizations in the field, including DeepMind, OpenAI, Google Research, Microsoft Research, and Tesla's Autopilot team.
Strategic Positioning: xAI has positioned itself as an independent AI company that nonetheless maintains close ties with X (formerly Twitter) and other Musk-led companies. This relationship with X has provided Grok with a ready distribution platform through X's Premium+ subscription service.
Funding and Resources:
- In December 2023, xAI announced it had raised $6 billion in funding, with investors including Sequoia Capital, Andreessen Horowitz, Fidelity Management, and others.
- The company has access to significant computing resources, which are essential for training and running advanced AI models like Grok.
Research Focus: Beyond developing Grok as a product, xAI has indicated research interests in several areas:
- Reasoning capabilities in large language models
- Truthfulness and bias mitigation
- Multimodal understanding (text, images, and potentially other modalities)
- AI alignment and safety
xAI represents a significant new entrant in the competitive landscape of AI research and development, with substantial resources and a distinctive philosophical approach that shapes the development of Grok AI.
Grok's Position in the AI Landscape
Grok occupies a distinctive position in the evolving landscape of large language models and AI assistants:
Competitive Positioning: Grok competes directly with other leading AI assistants, including:
- OpenAI's ChatGPT and GPT models
- Anthropic's Claude
- Google's Gemini (formerly Bard)
- Meta's Llama-based assistants
Within this competitive field, Grok has carved out a distinctive identity based on several differentiating factors.
Technological Positioning:
- Grok is among the more advanced general-purpose LLMs, though benchmarks suggest it currently performs slightly behind the most capable models like GPT-4 and Claude 3 Opus on various reasoning and knowledge tasks.
- Its integrated real-time information access places it among the models that directly address the knowledge cutoff limitation of traditional LLMs.
- Grok's development timeline shows rapid iteration and improvement, indicating xAI's commitment to quickly enhancing its capabilities.
Philosophical Positioning:
- Grok has been explicitly positioned as a "maximum truth-seeking" AI, with xAI emphasizing its willingness to engage with controversial topics that other AI systems might avoid.
- The model reflects Musk's stated concerns about what he perceives as political bias in other AI systems, offering what xAI characterizes as a more politically neutral alternative.
- Grok's "rebellious" personality represents a deliberate departure from the more cautious, neutral tone adopted by many competing AI assistants.
Market Positioning:
- Initially available exclusively to X Premium+ subscribers, Grok has a more restricted access model than many competitors, though this is likely to evolve as xAI expands its availability.
- The close integration with X (formerly Twitter) provides a distinctive distribution channel that leverages Musk's existing technology ecosystem.
- Grok's association with Elon Musk gives it high visibility and a ready audience among Musk's substantial following, while also potentially polarizing perception among those with varying opinions about Musk.
Developmental Trajectory: Grok appears to be on a path of rapid capability expansion, with xAI demonstrating a commitment to quick iterations and feature additions. This suggests a trajectory that will likely see Grok continue to evolve as a significant player in the AI assistant space, potentially with increased focus on enterprise applications as the model matures.
The model represents an important new entrant in a field that continues to develop at an extraordinary pace, adding a distinctive voice and approach to the ongoing conversation about how AI assistants should function and what role they should play in society.
Technical Foundation
Model Architecture
Grok AI is built on a transformer-based architecture, the dominant paradigm for large language models since the publication of the "Attention is All You Need" paper by Vaswani et al. in 2017. While xAI has not published comprehensive technical details about Grok's specific architecture, we can outline its likely structure based on available information and typical approaches in state-of-the-art LLMs.
Core Architecture Components:
- Transformer Foundation:
- Like other modern LLMs, Grok utilizes a transformer architecture with self-attention mechanisms that allow the model to weigh the importance of different words in context.
- The model likely employs a decoder-only transformer architecture similar to GPT models, which is optimized for text generation tasks.
- This architecture allows Grok to process input text and generate appropriate responses by predicting the most likely next tokens in a sequence.
- Attention Mechanisms:
- Multi-head attention mechanisms enable the model to focus on different aspects of the input simultaneously.
- This allows Grok to capture complex relationships between words and concepts across long contexts.
- The attention patterns learned during training help the model understand syntax, semantics, and factual relationships.
- Layer Structure:
- Grok consists of multiple transformer layers stacked on top of each other, with each layer processing the output of the previous layer.
- Each layer includes attention mechanisms and feed-forward neural networks.
- Layer normalization and residual connections likely help stabilize training and improve performance.
- Context Window:
- Grok has a context window of approximately 8,000 tokens, allowing it to process and maintain awareness of relatively long conversations and documents.
- This context management is crucial for maintaining coherence in extended interactions.
- Tokenization:
- Like other LLMs, Grok processes text by breaking it down into tokens, which may be words, parts of words, or individual characters depending on the tokenization scheme.
- The model was likely trained using a vocabulary of tens of thousands of tokens, allowing it to represent a wide range of text efficiently.
- Web Browsing Capability:
- A distinctive architectural feature of Grok is its integration with web browsing capabilities.
- This likely involves specialized components that:
- Translate user queries into appropriate search queries
- Process and extract information from search results and web pages
- Integrate this information with the model's existing knowledge
- Format responses that incorporate this real-time information
- Multimodal Extensions (in newer versions):
- Grok-1.5V introduced multimodal capabilities, allowing the model to process images alongside text.
- This likely involves additional architectural components for visual processing, such as vision transformers or convolutional neural networks, and mechanisms to align visual and textual representations.
The architecture represents a sophisticated integration of transformer-based language modeling with specialized components for real-time information access and, in newer versions, multimodal understanding. This foundation enables Grok's core capabilities while establishing a framework that can be expanded and enhanced in future iterations.
Training Methodology
The training of Grok AI follows a multi-stage process typical of large language models, though with specific approaches that reflect xAI's priorities and technical philosophy. While xAI has not disclosed comprehensive details about Grok's training, we can outline the likely methodology based on available information and standard practices in the field.
Pre-training Phase:
- Data Collection and Curation:
- Grok was trained on a diverse corpus of text drawn from the internet and other sources, likely including books, articles, websites, code repositories, and other text data.
- xAI has stated that Grok-1 was "trained on a large amount of text data from the web and other public information." This suggests a broad data collection approach similar to other large language models.
- The data curation process likely involved filtering for quality and removing certain types of harmful or problematic content, though xAI's stated philosophy suggests potentially different filtering criteria than those used by companies like OpenAI or Anthropic.
- Self-supervised Learning:
- Like other modern LLMs, Grok was likely pre-trained using self-supervised learning objectives, primarily next-token prediction.
- This involves training the model to predict the next word in a sequence given the previous words, allowing it to learn patterns, relationships, and knowledge from the training data without requiring explicit labeling.
- This pre-training process enables the model to develop general language understanding and knowledge representation.
- Distributed Training Infrastructure:
- Training a model of Grok's scale requires substantial computational resources.
- xAI likely employed distributed training across multiple GPUs or TPUs, with specialized software to coordinate the training process across this hardware.
- Optimization techniques like mixed-precision training were probably used to improve efficiency.
Fine-tuning and Alignment Phase:
- Supervised Fine-tuning (SFT):
- After pre-training, Grok was likely fine-tuned on examples of high-quality, helpful responses to various user queries.
- This process helps align the model's outputs with human preferences and expectations for an AI assistant.
- The fine-tuning dataset likely included examples showing how to follow instructions, provide helpful information, and engage in natural conversation.
- Reinforcement Learning from Human Feedback (RLHF):
- xAI probably employed RLHF techniques to further refine Grok's responses.
- This involves collecting human preferences between different model outputs, training a reward model based on these preferences, and then using reinforcement learning to optimize the model toward higher reward outputs.
- Given xAI's stated philosophy, their RLHF process may have emphasized different values than other AI companies, potentially prioritizing "maximum truth-seeking" and a willingness to engage with a wider range of topics.
- Safety Alignment:
- While maintaining its "rebellious" nature, Grok still required safety guardrails to prevent genuinely harmful outputs.
- xAI likely implemented specialized training and filtering to prevent the model from producing content that could enable illegal activities, cause direct harm, or violate basic ethical standards.
- This safety alignment process may have been calibrated differently than competing models, reflecting xAI's stated goal of creating a less restrictive AI.
Specialized Capability Training:
- Web Browsing Integration:
- A distinctive aspect of Grok's training would have been developing its capability to effectively access and utilize real-time information.
- This likely involved specialized training on:
- Generating effective search queries based on user questions
- Extracting relevant information from search results and web pages
- Synthesizing this information with the model's existing knowledge
- Providing appropriate attribution and handling conflicting information
- Multimodal Training (for Grok-1.5V):
- The multimodal version of Grok required additional training on image-text pairs to develop the ability to understand and discuss visual content.
- This likely involved specialized datasets containing images paired with descriptive text, captions, or related discussions.
- Continuous Improvement:
- Grok's rapid version iterations suggest an ongoing training methodology that incorporates new data, techniques, and capabilities.
- This likely includes analyzing user interactions to identify areas for improvement and updating the model accordingly.
This multi-stage training methodology has enabled Grok to develop its distinctive capabilities while reflecting xAI's philosophical approach to AI development.
Parameter Scale
The parameter scale of a large language model is a crucial factor in determining its capabilities, as it directly influences the model's capacity to learn patterns, store knowledge, and generate coherent, contextually appropriate responses. While xAI has not publicly disclosed the exact parameter count for Grok, we can provide informed estimates based on its performance and comparisons with other models.
Parameter Count Estimates:
Based on performance benchmarks and comparisons with other models, Grok-1 is estimated to have between 100 billion and 175 billion parameters. This places it in the same general scale as models like:
- GPT-4 (estimated to have approximately 1 trillion parameters)
- Claude 2 (estimated to have over 100 billion parameters)
- PaLM 2 (estimated at 340 billion parameters)
The subsequent Grok-1.5 likely maintained or slightly increased this parameter count, with potential architecture improvements to enhance efficiency and capability per parameter.
Significance of Parameter Scale:
- Knowledge Capacity:
- With a parameter count in the hundreds of billions, Grok has substantial capacity to store factual knowledge, linguistic patterns, and reasoning capabilities.
- This scale allows the model to "memorize" vast amounts of information from its training data, enabling it to answer questions across diverse domains without always needing to access external information.
- Reasoning Depth:
- Larger parameter counts generally correlate with improved reasoning capabilities, allowing Grok to handle more complex logical problems, follow multi-step instructions, and maintain coherence across longer contexts.
- The scale of Grok appears sufficient to support sophisticated reasoning, though benchmarks suggest it may not yet match the most advanced models in this regard.
- Generative Capability:
- Grok's parameter scale enables it to generate diverse, contextually appropriate text across various styles, formats, and domains.
- This includes creative writing, technical explanations, conversational responses, and code generation, among other capabilities.
- Computational Requirements:
- A model with hundreds of billions of parameters requires substantial computational resources for both training and inference.
- For inference (running the model to generate responses), this necessitates high-performance hardware, which may influence deployment options and access models.
- Evolutionary Context:
- Grok's parameter scale represents a significant but not revolutionary step in the ongoing scaling of large language models.
- It reflects xAI's approach of building a competitive model while potentially focusing on other aspects of development, such as real-time information access, rather than simply maximizing parameter count.
Efficiency Considerations:
It's important to note that raw parameter count is not the only determinant of model capability. Recent developments in the field have demonstrated that:
- Architectural improvements can increase efficiency, allowing smaller models to perform comparably to larger ones.
- Specialized training approaches can enhance performance without increasing parameter count.
- Models like Grok that integrate external knowledge sources (web browsing) may achieve greater effective capability with fewer parameters than fully self-contained models.
The parameter scale of Grok represents a significant investment in model capacity, placing it among the more advanced language models available while still being exceeded by the very largest models in the field. This scale supports Grok's broad capabilities while working in conjunction with its architectural design and training methodology to determine its overall performance characteristics.
Language Processing Approach
Grok AI processes language through a sophisticated approach that combines statistical pattern recognition with contextual understanding, enabling it to interpret user inputs and generate appropriate responses. This approach involves several key components and processes:
Tokenization and Input Processing:
- Tokenization:
- Grok breaks down input text into tokens, which may be words, parts of words, or individual characters depending on the tokenization scheme.
- This tokenization likely uses a subword tokenization method similar to Byte-Pair Encoding (BPE) or SentencePiece, which can efficiently handle words not seen during training.
- Each token is converted into a numerical vector representation that the model can process.
- Embedding:
- These token representations are then transformed into embeddings—dense vector representations that capture semantic meaning.
- The embedding space allows the model to represent similar words or concepts as numerically similar vectors.
- These embeddings serve as the input to the transformer layers of the model.
Contextual Understanding:
- Attention Mechanisms:
- Grok uses self-attention mechanisms to analyze relationships between all tokens in the input.
- This allows the model to consider the entire context when interpreting each word or phrase.
- Multiple attention heads allow the model to focus on different aspects of the relationships between words simultaneously.
- Contextual Representation:
- As information flows through the model's layers, each token's representation is continuously updated based on its context.
- This creates rich, contextual representations that capture the meaning of words as they are used in specific contexts.
- Later layers in the model develop increasingly abstract and sophisticated representations of the text.
- Long-context Processing:
- With a context window of approximately 8,000 tokens, Grok can maintain awareness of lengthy conversations or documents.
- This allows it to refer back to information mentioned earlier in a conversation and maintain coherence across extended interactions.
Response Generation:
- Autoregressive Generation:
- Grok generates responses one token at a time in an autoregressive manner.
- Each new token is predicted based on all previously generated tokens and the original input.
- This sequential generation process allows the model to create coherent, contextually appropriate text.
- Sampling Strategies:
- The model uses sophisticated sampling strategies to determine which token to output next.
- These likely include temperature controls (adjusting randomness), top-p sampling (limiting choices to the most probable tokens), and other techniques to balance creativity with coherence.
- Different sampling approaches may be used depending on the nature of the task (e.g., more deterministic for factual questions, more creative for open-ended generation).
- Stopping Criteria:
- The model employs various methods to determine when to end a response, including recognizing natural ending points and respecting length constraints.
Special Handling Mechanisms:
- Query Analysis:
- Grok analyzes user queries to determine their intent, required expertise domain, and whether they need current information.
- This analysis helps the model decide whether to rely on its internal knowledge or activate its web browsing capability.
- Knowledge Integration:
- When using web browsing, Grok must integrate information from external sources with its internal knowledge.
- This involves resolving potential contradictions, assessing source reliability, and presenting a coherent synthesis.
- Format Recognition:
- The model can recognize and generate text in various formats, including natural language, code, lists, tables, and structured data.
- This requires understanding format-specific conventions and syntax.
- Multilingual Processing:
- Grok has capabilities for processing multiple languages, though its primary strength is in English.
- This requires understanding the syntax, semantics, and unique characteristics of different languages.
- Safety Filtering:
- Grok implements various safety mechanisms to filter potentially harmful outputs.
- This includes detecting and avoiding prohibited content categories while still maintaining its "rebellious" approach to answering questions more broadly than some competitors.
Grok's language processing approach represents a sophisticated integration of these components, enabling it to understand complex queries, access and process relevant information, and generate appropriate responses across a wide range of topics and tasks.
Core Capabilities
Natural Language Understanding
Grok AI demonstrates sophisticated natural language understanding (NLU) capabilities that allow it to interpret user inputs with nuance and accuracy. This understanding forms the foundation for all of Grok's functionality, enabling it to process queries, detect intent, and generate appropriate responses.
Semantic Understanding: Grok can grasp the meaning behind words and phrases, not just their literal definitions. This semantic understanding allows the model to:
- Interpret ambiguous language: When a word or phrase has multiple potential meanings, Grok can usually determine the intended meaning based on context.
- Recognize synonyms and paraphrases: The model understands that different phrasings can express the same underlying concept, allowing it to respond appropriately regardless of how a question is formulated.
- Process figurative language: Grok can interpret metaphors, similes, idioms, and other non-literal expressions, though with varying degrees of accuracy depending on the complexity and cultural specificity of the expression.
- Recognize entities and concepts: The model identifies people, places, organizations, dates, and abstract concepts mentioned in text, understanding their significance and relationships.
Syntactic Processing: Grok demonstrates strong syntactic understanding, allowing it to:
- Parse complex sentences: The model can unravel nested clauses, complex sentence structures, and grammatical nuances.
- Handle grammatical variations: Grok can process text with varying grammatical structures, tenses, and voices, extracting the core meaning regardless of syntax.
- Recognize parts of speech: The model understands the functions of different words within sentences, distinguishing between nouns, verbs, adjectives, and other parts of speech.
- Process queries with linguistic errors: Grok can often understand the intent behind inputs containing typos, grammatical errors, or unusual phrasing.
Intent Recognition: A crucial aspect of Grok's natural language understanding is its ability to recognize user intent:
- Query classification: The model categorizes inputs into different types of requests (questions, instructions, conversation, creative tasks, etc.) and responds accordingly.
- Domain identification: Grok can determine which knowledge domain a query relates to (science, history, technology, arts, etc.), allowing it to draw on relevant information.
- Specificity assessment: The model evaluates how specific or open-ended a query is, adjusting its response style and depth accordingly.
- Implicit requests: Grok can often identify unstated but implied requests in user inputs, responding to the underlying need rather than just the explicit question.
Contextual Understanding: Grok maintains contextual awareness throughout conversations:
- Reference resolution: The model can resolve pronouns and other references to previously mentioned entities, maintaining coherence across conversation turns.
- Topic tracking: Grok follows topic shifts and maintains awareness of the conversation's subject matter, even in lengthy interactions.
- User state awareness: The model attempts to track implied user needs, knowledge level, and satisfaction throughout a conversation.
- Temporal understanding: Grok can process time-related language and maintain awareness of temporal relationships mentioned in conversation.
Multi-turn Comprehension: In extended conversations, Grok demonstrates:
- Conversational memory: The model maintains awareness of information shared earlier in the conversation, avoiding redundancy and building on established context.
- Progressive elaboration: Grok can handle follow-up questions that add constraints or specifications to earlier queries.
- Clarification processing: When given clarifications or corrections, the model can update its understanding of the user's intent.
- Coherent threading: The model maintains logical and topical coherence across multiple conversation turns.
These natural language understanding capabilities, while impressive, do have limitations. Grok may struggle with highly implicit cultural references, extremely technical domain-specific language without proper context, or detecting subtle emotional nuances in text. However, its overall NLU capabilities provide a strong foundation for its function as an AI assistant, enabling it to process a wide range of queries with impressive accuracy and nuance.
Knowledge Retrieval
Grok AI employs sophisticated knowledge retrieval mechanisms that allow it to access and utilize information from both its pre-trained parameters and external sources. This dual approach to knowledge access represents one of Grok's distinctive capabilities.
Internal Knowledge Base:
Grok's primary knowledge source is the information encoded in its model parameters during training:
- Parametric Knowledge Storage:
- During training on vast text corpora, Grok encoded billions of facts, concepts, and relationships in its neural network parameters.
- This parametric knowledge spans diverse domains including science, history, literature, programming, current events (up to its training cutoff), and general world knowledge.
- Associative Retrieval:
- When processing a query, Grok activates relevant portions of its neural network, effectively "retrieving" knowledge related to the query.
- This retrieval is associative rather than lookup-based, allowing the model to connect concepts and generate insights beyond simple fact recall.
- Knowledge Organization:
- While not explicitly structured like a traditional database, Grok's internal knowledge appears to be organized in ways that respect taxonomic relationships, logical implications, and semantic associations.
- This implicit organization allows the model to navigate its knowledge effectively, even across domains.
- Knowledge Integration:
- Grok can combine facts from different domains to answer interdisciplinary questions or draw connections between seemingly unrelated topics.
- This integration capability demonstrates a level of knowledge synthesis beyond simple retrieval.
External Knowledge Access:
Grok's distinctive feature is its ability to supplement its internal knowledge with real-time information from the web:
- Query Transformation:
- When Grok determines that a query requires current information or details beyond its training data, it can transform the user's question into appropriate search queries.
- This transformation process identifies key search terms and formulates queries likely to retrieve relevant information.
- Web Search Execution:
- Grok executes these search queries against web search engines, retrieving a set of potentially relevant results.
- The model can likely adjust its search approach based on initial results, refining queries if needed.
- Content Extraction:
- From search results or specific web pages, Grok extracts relevant information, focusing on content that addresses the user's query.
- This extraction process involves identifying key passages, facts, or data points within sometimes lengthy or complex sources.
- Information Evaluation:
- Grok attempts to assess the reliability and relevance of information retrieved from external sources.
- This evaluation likely considers factors such as source credibility, consistency with known facts, and relevance to the query.
- Knowledge Synthesis:
- The model integrates information from multiple sources, resolving contradictions and presenting a coherent synthesis.
- This synthesis combines externally retrieved information with Grok's internal knowledge to provide comprehensive responses.
Limitations and Challenges:
Despite its sophisticated knowledge retrieval capabilities, Grok faces several challenges:
- Hallucination Risk:
- Like all current LLMs, Grok may occasionally "hallucinate" information, presenting incorrect facts with confidence.
- This risk exists for both internal knowledge retrieval and external information synthesis.
- Source Reliability:
- When accessing external information, Grok must navigate the varying reliability of web sources.
- The model may sometimes retrieve and present information from sources of questionable accuracy.
- Knowledge Currency:
- While web access helps with recent information, Grok's understanding of very recent events or rapidly changing situations may still be limited by search results quality and its ability to interpret them correctly.
- Knowledge Depth vs. Breadth:
- Grok balances broad knowledge across many domains with deep expertise in specific areas, sometimes resulting in limitations when highly specialized knowledge is required.
- Attribution Challenges:
- The model may sometimes struggle to properly attribute information to sources, particularly when synthesizing from multiple references.
Grok's knowledge retrieval capabilities represent a significant advancement in AI assistants, combining the advantages of parametric knowledge with the currency of web access. This hybrid approach allows Grok to provide more complete and up-to-date responses than models limited to their training data, while still leveraging the deep understanding encoded in its parameters.
Real-time Information Access
One of Grok AI's most distinctive capabilities is its ability to access and process real-time information from the internet, addressing a fundamental limitation of traditional large language models that are restricted to knowledge from their training data.
Technical Implementation:
Grok's real-time information access capability is implemented through a sophisticated system that includes:
- Query Analysis and Routing:
- Grok analyzes user queries to determine whether they require current information beyond its training data.
- The model assesses factors such as time-sensitivity, references to recent events, or explicit requests for current data.
- Based on this analysis, Grok decides whether to rely on its internal knowledge or activate its web browsing capability.
- Search Query Formulation:
- When web access is needed, Grok converts the user's question into effective search queries.
- This involves identifying key search terms, potential sources, and query formulations likely to yield relevant results.
- The model may generate multiple search queries for complex questions requiring information from different sources.
- Search Execution and Result Processing:
- Grok executes these search queries against web search engines, retrieving a set of potentially relevant results.
- The model processes search results to identify the most promising sources for the requested information.
- This may involve analyzing snippets, titles, and source credibility to prioritize which links to explore further.
- Web Page Content Extraction:
- From selected search results, Grok can access and process the content of web pages.
- The model extracts relevant information from these pages, focusing on content that addresses the user's query.
- This extraction process involves filtering out advertising, navigation elements, and other irrelevant content to focus on the substantive information.
- Information Synthesis and Integration:
- Grok synthesizes information from multiple web sources, resolving contradictions and inconsistencies when possible.
- The model integrates this web-sourced information with its existing knowledge to provide comprehensive responses.
- This integration process attempts to maintain factual accuracy while presenting information in a coherent, conversational manner.
- Attribution and Sourcing:
- When providing information from external sources, Grok can include citations or references to the original sources.
- This attribution helps users understand where information is coming from and facilitates further exploration if desired.
Types of Real-time Information:
Grok can access various types of current information, including:
- Recent Events and News:
- Updates on current events, breaking news, and recent developments across various domains.
- This allows Grok to discuss events that occurred after its training data cutoff.
- Current Data and Statistics:
- Up-to-date figures, statistics, prices, ratings, and other quantitative information.
- Examples include current stock prices, sports scores, weather conditions, and economic indicators.
- Product Information and Reviews:
- Details about recently released products, services, and their reviews or ratings.
- This information helps Grok provide relevant recommendations and comparisons.
- Business and Organization Updates:
- Current information about companies, organizations, and their recent activities.
- This includes leadership changes, new initiatives, and other organizational developments.
- Technical Documentation:
- Access to current documentation for software, APIs, and technical systems.
- This allows Grok to provide up-to-date technical assistance and reference accurate specifications.
- Academic and Scientific Developments:
- Recent research findings, publications, and scientific advancements.
- This helps Grok discuss cutting-edge developments across scientific fields.
Advantages and Limitations:
The real-time information access capability provides several advantages:
- Overcoming Knowledge Cutoff:
- Grok can discuss events, developments, and information that emerged after its training data cutoff.
- This makes the model more useful for queries requiring current awareness.
- Factual Accuracy:
- Access to current information can improve the accuracy of Grok's responses on time-sensitive topics.
- The model can verify or update its internal knowledge with the latest information available online.
- Expanded Knowledge Domain:
- Web access effectively expands Grok's knowledge to include specialized or niche topics that might not have been well-represented in its training data.
- This allows the model to provide information on a wider range of subjects.
However, this capability also has limitations:
- Source Quality Variability:
- The reliability of web-sourced information depends on the quality of available sources.
- Grok may sometimes retrieve and present information from sources of varying credibility.
- Search Limitations:
- The quality of information retrieved depends on the effectiveness of Grok's search queries and the limitations of underlying search engines.
- Some information may be difficult to find if it's not well-indexed or prominently featured in search results.
- Interpretation Challenges:
- Extracting accurate information from web pages requires correct interpretation of sometimes complex or ambiguous content.
- Grok may occasionally misinterpret information, particularly from complex sources or on highly technical topics.
- Access Restrictions:
- Grok cannot access information behind paywalls, login requirements, or other access controls.
- This limits its ability to retrieve information from certain premium or restricted sources.
- Processing Time:
- Web browsing introduces some latency in response generation compared to queries answered from internal knowledge.
- Complex queries requiring multiple searches may take longer to process.
Despite these limitations, Grok's real-time information access represents a significant advancement in AI assistant capabilities, allowing it to provide more current and comprehensive responses than models limited to their training data.
Reasoning Abilities
Grok AI demonstrates sophisticated reasoning capabilities that enable it to process complex problems, follow multi-step instructions, and generate logically sound analyses. These reasoning abilities are central to Grok's function as an advanced AI assistant capable of handling intellectually demanding tasks.
Logical Reasoning:
Grok can apply principles of deductive and inductive logic to analyze problems and draw conclusions:
- Deductive Reasoning:
- The model can follow logical syllogisms and apply general principles to specific cases.
- It demonstrates the ability to recognize logical implications and draw valid conclusions from given premises.
- Example: Given assumptions about a system's rules, Grok can correctly determine what must follow from those rules.
- Inductive Reasoning:
- Grok can identify patterns from specific examples and generalize to broader principles.
- It can form reasonable hypotheses based on limited information, while usually acknowledging the probabilistic nature of such conclusions.
- Example: Given several examples of a pattern, Grok can predict how the pattern might continue.
- Abductive Reasoning:
- The model can generate plausible explanations for observations, considering multiple possible interpretations.
- It attempts to identify the most likely explanation for a given phenomenon based on available information.
- Example: Given symptoms of a system problem, Grok can suggest possible causes, typically starting with the most likely ones.
Analytical Problem-Solving:
Grok can break down complex problems into component parts and work through them systematically:
- Step-by-Step Analysis:
- When faced with multi-stage problems, Grok can decompose them into sequential steps and address each in turn.
- The model maintains awareness of its progress through a problem-solving sequence and builds upon earlier steps.
- Example: When solving a complex mathematical problem, Grok will typically show its work by proceeding through logical stages of calculation.
- Case Analysis:
- Grok can consider different possible scenarios or cases and analyze each separately.
- It demonstrates the ability to explore multiple branches of possibility in conditional problems.
- Example: Given a problem with several possible initial conditions, Grok can analyze the outcome for each condition.
- Constraint Satisfaction:
- The model can reason about problems with multiple constraints and identify solutions that satisfy all given conditions.
- It demonstrates understanding of how constraints interact and limit the solution space.
- Example: Given a scheduling problem with multiple requirements, Grok can propose arrangements that meet all specified constraints.
Numerical and Mathematical Reasoning:
Grok shows capability for mathematical thinking across various domains:
- Arithmetic and Basic Mathematics:
- The model can perform calculations, though its accuracy may decrease with very complex calculations.
- It demonstrates understanding of mathematical concepts like percentages, ratios, and basic statistics.
- Example: Grok can calculate compound interest, convert between units, or determine statistical measures for data sets.
- Mathematical Problem Formulation:
- Grok can translate word problems into mathematical expressions or equations.
- It shows ability to identify the appropriate mathematical approach for different problem types.
- Example: Given a verbal description of a physics scenario, Grok can set up the relevant equations.
- Probabilistic Reasoning:
- The model demonstrates understanding of probability concepts and can calculate probabilities for various scenarios.
- It shows awareness of concepts like independence, conditional probability, and expected value.
- Example: Grok can reason about the likelihood of different outcomes in games of chance or statistical scenarios.
Critical Thinking and Evaluation:
Grok demonstrates capabilities for evaluating information and arguments:
- Argument Analysis:
- The model can identify premises, conclusions, and the logical structure of arguments.
- It shows ability to recognize common logical fallacies and weaknesses in reasoning.
- Example: Given an argument, Grok can point out unwarranted assumptions or logical gaps.
- Evidence Evaluation:
- Grok attempts to assess the strength and relevance of evidence for claims.
- It demonstrates awareness of concepts like correlation vs. causation and statistical significance.
- Example: When presented with statistical claims, Grok can identify potential confounding factors or limitations.
- Source Credibility Assessment:
- When using its web browsing capability, Grok makes efforts to evaluate the reliability of sources.
- It shows awareness of factors that affect source credibility, though its implementation may be imperfect.
- Example: Grok might note when information comes from peer-reviewed research versus less authoritative sources.
Meta-Reasoning:
Grok demonstrates some capacity for reasoning about its own reasoning:
- Confidence Assessment:
- The model attempts to communicate its confidence in different parts of its reasoning.
- It shows willingness to acknowledge uncertainty when information is limited or conclusions are tentative.
- Example: Grok might indicate that certain conclusions are speculative or note when it lacks sufficient information for a definitive answer.
- Approach Selection:
- Grok can select appropriate reasoning strategies for different types of problems.
- It demonstrates flexibility in switching between reasoning approaches as needed.
- Example: The model might use different approaches for mathematical problems versus ethical dilemmas.
- Error Detection:
- In some cases, Grok can recognize and correct errors in its own reasoning.
- This self-correction ability is limited but represents an important aspect of its reasoning capability.
- Example: After working through a problem, Grok might recognize a mistake in its earlier steps and provide a correction.
While Grok's reasoning abilities are impressive, they do have limitations. The model may occasionally make errors in complex logical chains, struggle with highly abstract reasoning, or fail to recognize subtle logical fallacies. These limitations reflect the broader challenges in implementing human-like reasoning in current AI systems. Nevertheless, Grok's reasoning capabilities enable it to handle a wide range of intellectual tasks with considerable effectiveness.
Creative Generation
Grok AI demonstrates significant capabilities in creative content generation, allowing it to produce various forms of original, engaging, and contextually appropriate content based on user requests. This creative generation spans multiple domains and formats, making it valuable for diverse applications from entertainment to professional content creation.
Text-Based Creative Writing:
Grok can generate various forms of creative written content:
- Narrative Fiction:
- The model can create original short stories, fictional scenes, and narrative fragments across genres.
- It demonstrates understanding of story structure, character development, dialogue, and pacing.
- Example capabilities include writing short stories in specific genres, continuing stories from prompts, or creating character sketches.
- Poetry and Verse:
- Grok can generate various poetic forms, from free verse to structured formats like sonnets, haiku, or limericks.
- It shows appreciation for rhyme, meter, imagery, and other poetic devices.
- The quality of poetic output varies, with simpler forms often being more successful than complex poetic structures.
- Dialogue and Script Writing:
- The model can create conversational exchanges between characters, including script-style formatting.
- It demonstrates ability to maintain consistent character voices and advance narratives through dialogue.
- Example capabilities include writing screenplay scenes, creating hypothetical conversations, or generating interview scripts.
- Creative Non-fiction:
- Grok can produce essay-style explorations of topics from creative perspectives.
- It shows ability to blend informational content with engaging narrative approaches.
- Example capabilities include generating travel narratives, reflective essays, or feature article-style content.
Professional Content Creation:
Beyond purely creative writing, Grok can generate various forms of professional content:
- Marketing and Promotional Copy:
- The model can create advertising copy, product descriptions, marketing emails, and similar content.
- It demonstrates understanding of persuasive techniques, audience targeting, and brand voice.
- Example capabilities include generating taglines, creating product launch announcements, or writing promotional blog posts.
- Educational Content:
- Grok can produce instructional materials, explanatory texts, and learning resources.
- It shows ability to adapt explanations for different knowledge levels and learning contexts.
- Example capabilities include creating lesson plans, educational scripts, or explanatory guides.
- Business Communications:
- The model can generate professional emails, reports, proposals, and other business documents.
- It demonstrates understanding of business communication norms and professional language.
- Example capabilities include drafting business correspondence, creating meeting agendas, or writing executive summaries.
- Technical Writing:
- Grok can produce documentation, technical guides, and process descriptions.
- It shows ability to present complex information clearly and systematically.
- Example capabilities include creating user guides, API documentation, or technical specifications.
Specialized Creative Generation:
Grok also demonstrates creative generation capabilities in more specialized domains:
- Code Generation:
- The model can create original code snippets, scripts, and programs across multiple programming languages.
- It demonstrates understanding of programming concepts, syntax, and best practices.
- Example capabilities include generating functions for specific tasks, creating data processing scripts, or building simple applications.
- Game and Interactive Content:
- Grok can create content for games and interactive experiences, such as game scenarios, puzzles, or interactive fiction.
- It shows understanding of game mechanics, player engagement, and interactive storytelling.
- Example capabilities include designing riddles, creating text-based adventure scenarios, or developing game concepts.
- Adaptation and Transformation:
- The model can transform content between styles, formats, or tones.
- It demonstrates ability to maintain core content while adapting presentational elements.
- Example capabilities include rewriting technical content for non-technical audiences, adapting prose to different periods or styles, or converting concepts between media formats.
Creative Process Capabilities:
Beyond generating content, Grok shows capabilities related to the creative process itself:
- Ideation and Brainstorming:
- The model can generate multiple creative ideas around a theme or concept.
- It demonstrates divergent thinking and the ability to explore different conceptual directions.
- Example capabilities include brainstorming product names, generating story concepts, or proposing creative solutions to problems.
- Iteration and Refinement:
- Grok can revise and refine creative content based on feedback or direction.
- It shows ability to maintain core elements while making specified improvements.
- Example capabilities include editing draft content, enhancing specific aspects of created work, or addressing stylistic issues.
- Style Adaptation:
- The model can generate content in specific creative styles, mimicking genres or famous creators.
- It demonstrates understanding of the distinctive elements that characterize different creative styles.
- Example capabilities include writing in the style of specific authors, creating content in particular historical periods, or mimicking genre conventions.
Limitations and Considerations:
While Grok's creative generation capabilities are impressive, they do have limitations:
- Originality Boundaries:
- Like all current AI systems, Grok's creative output ultimately derives from patterns in its training data.
- While it can combine elements in novel ways, its fundamental creative building blocks come from existing human-created content.
- Quality Variation:
- The quality of creative output can vary significantly depending on the complexity of the request and the specific creative domain.
- Simpler creative forms typically yield more consistently successful results than highly sophisticated creative formats.
- Cultural and Contextual Limitations:
- Grok's creative generation may reflect biases or limitations in its training data, particularly regarding cultural contexts beyond dominant Western traditions.
- The model may have uneven capabilities across different cultural references, historical periods, or specialized creative domains.
- Ethical Boundaries:
- Grok maintains ethical boundaries in its creative generation, refusing to create certain types of content deemed harmful.
- This includes limitations on generating graphically violent content, sexually explicit material, or content promoting harmful activities.
Despite these limitations, Grok's creative generation capabilities represent a powerful tool for content creation, ideation, and creative exploration across a wide range of applications and domains.
Unique Features
"Rebellious" Nature
One of Grok AI's most distinctive characteristics is what xAI describes as its "rebellious" nature—a deliberate design choice that sets the model apart from many competitors in the AI assistant space. This characteristic manifests in several important ways and reflects xAI's broader philosophy regarding AI development and interaction.
Philosophical Foundation:
The "rebellious" nature of Grok stems from Elon Musk's stated concerns about what he perceives as excessive caution and potential political bias in other AI systems. xAI positioned Grok explicitly as an alternative approach, designed to:
- Challenge perceived orthodoxy: Offer responses that might explore ideas or perspectives that other AI systems might be more hesitant to engage with.
- Prioritize "maximum truth-seeking": Emphasize providing information and perspectives even on controversial or sensitive topics, with less restriction than some competing models.
- Balance safety with openness: Maintain basic safety guardrails while allowing more conversational freedom than some alternatives.
- Embrace humor and personality: Present information with a more casual, sometimes witty conversational style rather than a strictly neutral tone.
Manifestations in Interaction:
Grok's "rebellious" nature manifests in several observable ways during interactions:
- Conversational Style:
- Grok often adopts a more casual, colloquial tone than many other AI assistants.
- The model may use humor, informal language, and conversational flourishes more frequently.
- This creates a more personable interaction experience that some users find more engaging.
- Topic Engagement:
- Grok is generally more willing to engage with controversial or sensitive topics, though still maintaining basic safety boundaries.
- The model attempts to provide balanced perspectives on divisive issues rather than declining to address them.
- This approach aims to provide more informative responses on complex social and political topics.
- Humor Integration:
- Grok may incorporate humor, wit, or playful responses where appropriate.
- The model sometimes includes jokes, puns, or lighthearted remarks in its responses.
- This humor element contributes to Grok's distinctive personality and interaction style.
- Direct Communication:
- Grok tends toward straightforward communication with less hedging or qualification than some alternatives.
- The model aims to provide clear answers rather than overly cautious responses.
- This directness is particularly noticeable on topics where other AI systems might be more reserved.
- Creative Expression:
- Grok may exhibit more creative freedom in generating content, stories, or hypothetical scenarios.
- The model appears designed to balance creative expression with appropriate boundaries.
- This enables more engaging responses to creative requests while still maintaining responsible limits.
Ethical Boundaries and Safety:
Despite its "rebellious" positioning, Grok still maintains important ethical boundaries:
- Core Safety Guardrails:
- Grok will not assist with clearly illegal activities, provide instructions for causing harm, or generate explicitly harmful content.
- The model maintains limits around generating dangerous instructions, explicitly hateful content, or graphic violent or sexual material.
- These fundamental safety measures remain in place regardless of the "rebellious" positioning.
- Balanced Approach to Controversial Topics:
- When addressing controversial issues, Grok attempts to present multiple perspectives rather than avoiding the topic.
- The model aims to acknowledge complexity and nuance rather than presenting simplified or one-sided views.
- This approach seeks to provide informative responses while avoiding harmful biases.
- Transparency About Limitations:
- Grok will generally acknowledge when a request pushes against its ethical boundaries rather than subtly redirecting.
- The model typically explains its limitations explicitly when declining certain requests.
- This transparency aligns with the "rebellious" ethos of direct communication.
Strategic Positioning:
The "rebellious" nature of Grok represents a deliberate strategic positioning in the AI assistant market:
- Differentiation Strategy:
- This characteristic helps differentiate Grok from competitors in an increasingly crowded AI assistant landscape.
- It appeals to users who may find other AI systems overly cautious or restrictive.
- This positioning aligns with Elon Musk's public brand and appeals to his existing audience.
- Response to Perceived Market Gap:
- xAI identified what they saw as an underserved segment of users seeking more direct engagement with complex topics.
- Grok's approach attempts to fill this perceived gap while maintaining responsible AI practices.
- This positions the model as an alternative rather than just another entry in the AI assistant category.
- Alignment with Brand Identity:
- The "rebellious" nature connects with the broader brand identity of xAI and its association with Elon Musk.
- This consistency creates a coherent brand story around challenging conventions and pursuing unconventional approaches.
- The positioning reinforces Musk's public stance on free speech and anti-censorship principles.
While the "rebellious" characterization sometimes creates expectations of dramatic differences from other AI systems, in practice, the distinctions are often more subtle than revolutionary. Grok maintains many of the same fundamental ethical boundaries as other responsible AI systems while adopting a somewhat different approach to tone, engagement with controversial topics, and conversational style. This characteristic represents an important differentiator in Grok's identity while functioning within the broader context of responsible AI development.
Internet Access
Grok AI's internet access capability represents one of its most significant technical differentiators, allowing it to overcome the knowledge cutoff limitation that affects many large language models. This feature enables Grok to provide more current, comprehensive, and accurate information by directly accessing and processing web content in real-time.
Technical Implementation:
Grok's internet access capability is implemented through a sophisticated system that includes:
- Integrated Web Browsing:
- Unlike some models that require plugins or extensions, Grok has web browsing capabilities built directly into its core functionality.
- This integration creates a more seamless experience when accessing current information.
- The system includes mechanisms for determining when web access is appropriate and beneficial for answering a query.
- Dynamic Query Generation:
- Grok analyzes user questions to formulate effective search queries.
- The model can generate multiple search queries for complex questions or refine queries based on initial results.
- This dynamic approach helps ensure relevant information is located even for nuanced or multi-faceted questions.
- Content Extraction and Processing:
- Beyond simple search results, Grok can access full web pages to extract detailed information.
- The model processes page content to identify relevant sections, data points, and context.
- This extraction capability allows for more comprehensive answers than would be possible from search snippets alone.
- Information Synthesis:
- Grok integrates information from multiple web sources with its existing knowledge.
- The model attempts to resolve contradictions or inconsistencies across sources.
- This synthesis process aims to provide coherent, accurate responses drawing on both real-time and pre-trained information.
Functional Workflow:
When a user asks a question that might benefit from current information, Grok follows a workflow:
- Query Analysis:
- Grok evaluates whether the question requires current information, references recent events, or concerns rapidly changing topics.
- Based on this analysis, the model decides whether to rely on its internal knowledge or activate its web browsing capability.
- Web Search Execution:
- If web access is needed, Grok formulates and executes search queries.
- The model retrieves search results that appear relevant to the user's question.
- These initial results provide an overview of available information sources.
- Source Selection and Access:
- Grok evaluates search results to identify the most promising sources.
- The model can then access full web pages from these sources to gather more detailed information.
- This selection process considers factors like source credibility, relevance, and information completeness.
- Information Extraction:
- From accessed web pages, Grok extracts the specific information relevant to the user's query.
- The model navigates page content to locate key facts, explanations, or data points.
- This extraction process filters out extraneous content to focus on pertinent information.
- Response Formulation:
- Grok synthesizes the extracted information into a coherent response.
- The model integrates this web-sourced content with its existing knowledge.
- The final response often includes attribution to sources when providing specific facts or claims.
Strategic Advantages:
Grok's internet access provides several strategic advantages over models limited to their training data:
- Information Currency:
- Grok can provide information about events that occurred after its training data cutoff.
- This allows the model to discuss recent developments, current events, and emerging trends.
- Users receive up-to-date answers rather than information that might be months or years out of date.
- Factual Accuracy:
- Access to current sources improves the accuracy of responses about rapidly changing topics.
- The model can verify or update information that may have changed since its training.
- This reduces the risk of providing outdated or superseded information.
- Information Breadth:
- Web access effectively expands Grok's knowledge domain beyond what was covered in its training data.
- The model can provide information on niche or specialized topics by accessing relevant websites.
- This breadth makes Grok more versatile across diverse subject areas.
- Source Transparency:
- Grok can provide attribution for information drawn from external sources.
- This allows users to assess the credibility of information or explore topics further.
- The transparency supports more informed decision-making based on Grok's responses.
Implementation Challenges:
Despite its advantages, Grok's internet access feature entails several implementation challenges:
- Source Reliability Assessment:
- The quality of responses depends partly on Grok's ability to assess source credibility.
- This assessment is complex and imperfect, potentially leading to inclusion of information from less reliable sources.
- The model must balance accessing current information with ensuring source quality.
- Information Synthesis Complexity:
- Integrating information from multiple sources, potentially with contradictions, is technically challenging.
- The model must resolve inconsistencies and present a coherent synthesis.
- This process becomes particularly complex for controversial or rapidly evolving topics.
- Processing Efficiency:
- Web access introduces additional processing time compared to responses from internal knowledge.
- The model must balance comprehensive information gathering with reasonable response times.
- This balance affects the user experience, particularly for complex queries requiring multiple searches.
- Access Limitations:
- Grok cannot access content behind paywalls, login requirements, or other access controls.
- Some valuable information sources remain inaccessible to the model's web browsing capability.
- This creates uneven coverage across different information domains.
- Privacy and Data Considerations:
- Web browsing raises questions about how user queries might be exposed to search engines.
- The implementation must balance effective information retrieval with appropriate privacy protections.
- This requires careful system design to manage data flows and search execution.
Grok's internet access capability represents a significant advancement in AI assistant functionality, addressing a fundamental limitation of traditional LLMs while creating new possibilities for providing current, comprehensive information. This feature exemplifies xAI's approach to developing AI systems that can access and process real-time information rather than being limited to knowledge from their training data.
UI/UX Design
Grok AI's user interface and user experience (UI/UX) design represents an important aspect of its implementation, particularly as it appears on the X platform (formerly Twitter). The design choices reflect xAI's philosophy for AI interaction while addressing practical considerations for effective human-AI collaboration.
Interface Integration with X Platform:
Grok is most prominently featured as an integrated service within the X platform:
- Native Integration:
- Grok appears as a built-in feature for X Premium+ subscribers rather than a separate application.
- This integration creates a seamless experience within the X ecosystem.
- Users can access Grok directly from the X interface without switching contexts or applications.
- Dedicated Tab/Section:
- Within the X interface, Grok has a dedicated access point, typically represented by an icon in the navigation.
- This dedicated space creates a clear separation between standard X content and Grok interactions.
- The design maintains consistency with X's overall aesthetic while establishing Grok as a distinct service.
- Branded Identity:
- Grok maintains a consistent visual identity that aligns with both xAI's branding and the X platform's design language.
- This branding helps establish Grok as a distinctive product while fitting into the broader ecosystem.
- Visual elements like icons, color schemes, and typography create recognition and consistency.
Conversation Interface Design:
The core of Grok's user experience is its conversation interface:
- Chat-Based Interaction:
- Grok uses a familiar chat interface with user messages and AI responses in a conversational format.
- This design leverages users' existing familiarity with messaging interfaces.
- The conversation history remains visible, allowing users to reference earlier exchanges.
- Message Styling:
- User messages and Grok's responses have distinct visual treatments to clearly differentiate them.
- Grok's responses may include formatting elements like bold text, lists, or code blocks to improve readability.
- This styling enhances the clarity of complex or structured information.
- Input Mechanism:
- Users interact with Grok primarily through a text input field, similar to standard messaging interfaces.
- The input area may include prompts or placeholder text to guide users on how to interact with Grok.
- This familiar design reduces the learning curve for new users.
- Response Presentation:
- Grok's responses appear in a conversational format but may include rich formatting when appropriate.
- For complex information, the interface likely supports structured elements like tables, code blocks, or emphasized text.
- These formatting capabilities allow for more effective communication of diverse content types.
Interaction Model:
Grok's interaction design emphasizes several key principles:
- Conversational Continuity:
- The interface maintains conversation history and context across multiple exchanges.
- This continuity allows for natural follow-up questions and extended discussions.
- The design supports reference to earlier parts of the conversation for clarity and context.
- Response Timing Indicators:
- When Grok is processing complex queries or accessing web information, the interface likely provides visual indicators of this process.
- These indicators help set user expectations about response timing.
- This transparency improves the experience when responses require additional processing time.
- Feedback Mechanisms:
- The interface probably includes mechanisms for users to provide feedback on Grok's responses.
- This feedback might include options to rate responses or report problematic content.
- These mechanisms support both user satisfaction and continuous improvement of the system.
- Recovery Paths:
- The design likely includes approaches for recovering from misunderstandings or unclear queries.
- These might include suggested reformulations, clarifying questions, or options to restart a conversation.
- These recovery paths help prevent frustration when communication challenges arise.
Distinctive UX Elements:
Several UX elements likely differentiate Grok's implementation:
- Personality Expression:
- The interface design probably supports Grok's "rebellious" personality through tone, language, and possibly visual elements.
- This personality-driven design creates a more engaging and distinctive experience.
- The expressions of personality are balanced with professionalism and helpfulness.
- Web Browsing Transparency:
- When Grok accesses the internet for information, the interface likely provides some indication of this process.
- This transparency helps users understand when responses are based on real-time information versus Grok's internal knowledge.
- The design might include source citations or references when presenting web-sourced information.
- Multimodal Support:
- With the introduction of Grok-1.5V, the interface has likely been enhanced to support image inputs alongside text.
- This multimodal capability allows users to share images for Grok to analyze or comment on.
- The design likely accommodates both text-only and image+text interactions within the same conversation flow.
- Progressive Disclosure:
- For complex or lengthy responses, the interface might implement progressive disclosure techniques.
- These could include expandable sections, "read more" options, or collapsible elements.
- This approach helps manage information density and cognitive load, particularly on mobile devices.
Platform Adaptations:
Grok's interface likely adapts to different contexts within the X ecosystem:
- Mobile Optimization:
- Given X's significant mobile usage, Grok's interface is certainly optimized for smaller screens.
- This includes appropriate text sizing, touch targets, and conversation layouts for mobile devices.
- The mobile experience likely maintains the core functionality while adapting to screen constraints.
- Desktop Enhancements:
- On larger screens, the interface probably takes advantage of additional space for enhanced formatting.
- This might include side-by-side layouts, more extensive formatting options, or additional controls.
- These enhancements improve the experience while maintaining consistency across platforms.
- Accessibility Considerations:
- The interface likely implements accessibility features consistent with X's overall approach.
- These features would include screen reader compatibility, keyboard navigation, and appropriate contrast ratios.
- These considerations ensure Grok is usable by people with diverse abilities and needs.
While specific details of Grok's UI/UX design may evolve over time, these elements represent the likely approach based on xAI's stated philosophy and the integration within the X platform. The design balances conversational naturalness with effective information presentation, creating a distinctive experience that aligns with Grok's overall positioning in the AI assistant market.
Contextual Understanding
Grok AI demonstrates sophisticated contextual understanding capabilities that allow it to maintain coherent, relevant conversations across multiple exchanges. This ability to track and utilize context is fundamental to Grok's effectiveness as a conversational AI assistant.
Conversation Context Maintenance:
Grok maintains awareness of conversation history in several important ways:
- Reference Resolution:
- The model can resolve pronouns and other references to previously mentioned entities or concepts.
- For example, if a user asks about "its climate" after discussing a specific country, Grok correctly interprets what "it" refers to.
- This capability extends to complex reference patterns across multiple turns of conversation.
- Topic Tracking:
- Grok maintains awareness of the current conversation topic or topics, allowing for coherent discussion flow.
- The model recognizes when subtopics emerge and can navigate between related subjects while maintaining overall coherence.
- This tracking allows Grok to provide responses that build upon previously established information rather than treating each query in isolation.
- Information Persistence:
- Details shared earlier in a conversation remain available for later reference and use.
- This includes facts, preferences, specifications, or constraints mentioned by the user.
- This persistence allows for progressive refinement of topics or ideas across multiple exchanges.
- Conversational Arc Awareness:
- Grok demonstrates awareness of the overall progression of a conversation, including its phase and purpose.
- The model can adapt its responses based on whether a conversation is in an exploratory, problem-solving, or concluding phase.
- This awareness helps Grok provide appropriately structured responses at different stages of an interaction.
Multi-turn Reasoning:
Grok's contextual understanding enables sophisticated multi-turn reasoning:
- Progressive Problem-Solving:
- The model can work through complex problems across multiple conversation turns.
- Each response builds upon previous reasoning steps, maintaining logical consistency.
- This capability allows for collaborative problem-solving that would be impossible in single-turn interactions.
- Iterative Refinement:
- Grok can progressively refine outputs based on user feedback across multiple turns.
- For example, when generating creative content, the model can incorporate successive revisions and direction.
- This iterative process leverages context to improve outputs over time rather than starting fresh with each exchange.
- Hypothesis Development:
- In analytical discussions, Grok can develop and refine hypotheses across conversation turns.
- Initial ideas can be explored, questioned, and enhanced based on ongoing dialogue.
- This approach mimics human thought development through conversation.
- Clarification Incorporation:
- When users provide clarifications or corrections, Grok integrates this new information into its understanding.
- The model updates its interpretation of the conversation based on these clarifications.
- This adaptive understanding allows for recovery from misunderstandings or ambiguities.
Contextual Interpretation:
Grok interprets user inputs in light of established context:
- Query Disambiguation:
- Ambiguous queries are interpreted based on the conversation's existing context.
- This allows users to ask follow-up questions that would be unclear in isolation but make sense in context.
- For example, after discussing solar energy, a simple "What about wind?" is understood as asking about wind energy.
- Implicit Parameter Handling:
- The model carries forward implied parameters or constraints from earlier in the conversation.
- If a user sets conditions or preferences, these are applied to subsequent related queries without needing repetition.
- This capability reduces redundancy and creates more natural conversation flow.
- Intent Recognition in Context:
- Grok interprets the intent behind user queries based on the conversation's established purpose and direction.
- The same query might be interpreted differently depending on the conversation's context.
- This contextual intent recognition helps Grok provide more relevant and appropriate responses.
- Contextual Tone Matching:
- The model adapts its tone and formality level to match the established conversational context.
- If a conversation has developed a certain style or register, Grok maintains consistency.
- This adaptation creates a more natural and cohesive interaction experience.
Technical Implementation:
Grok's contextual understanding capability is likely implemented through several technical approaches:
- Context Window Management:
- Grok maintains a context window of approximately 8,000 tokens, allowing it to reference substantial conversation history.
- This window likely includes both user inputs and Grok's own previous responses.
- When conversations exceed this limit, the model likely employs strategies to prioritize the most relevant context.
- Attention Mechanisms:
- Transformer-based attention mechanisms allow Grok to weigh the importance of different parts of the conversation history.
- These mechanisms help the model focus on the most relevant prior context for each new response.
- This selective attention enables more effective use of limited context window space.
- Context Compression Techniques:
- For longer conversations, Grok likely employs techniques to compress earlier exchanges while preserving key information.
- This might include summarization of earlier turns or selective retention of critical details.
- These techniques help manage the limited context window while maintaining conversational coherence.
- Entity Tracking:
- The model likely maintains representations of key entities, concepts, and relationships established in the conversation.
- This tracking helps Grok maintain awareness of what has been discussed and how topics relate to each other.
- The entity representations are updated as new information emerges throughout the conversation.
Limitations and Challenges:
Despite its sophisticated capabilities, Grok's contextual understanding does face certain limitations:
- Context Window Constraints:
- The finite context window (approximately 8,000 tokens) limits how much conversation history can be directly referenced.
- In very lengthy conversations, earlier information may become inaccessible.
- This constraint can create challenges for conversations that reference details from much earlier exchanges.
- Implicit Context Challenges:
- Grok may sometimes miss subtle implicit context that would be obvious to human participants.
- This can occasionally lead to misinterpretations when context is implied rather than explicitly stated.
- These challenges are more pronounced in conversations with complex subtext or cultural references.
- Context Conflicts:
- When new information contradicts earlier context, Grok may sometimes struggle to appropriately update its understanding.
- This can lead to inconsistencies in how the model applies context to interpretation.
- These conflicts are particularly challenging when they involve nuanced or partial contradictions.
- Long-term Memory Limitations:
- Beyond the context window, Grok does not maintain persistent memory of previous conversations with a user.
- Each new conversation effectively starts fresh, without access to information shared in prior sessions.
- This contrasts with human conversations, where relationships build on shared history across multiple interactions.
Despite these limitations, Grok's contextual understanding capabilities represent a sophisticated implementation of conversation awareness that enables natural, coherent interactions across multiple turns. This capability is fundamental to Grok's effectiveness as a conversational AI assistant and supports complex collaborative interactions that would be impossible with single-turn exchanges.
Comparative Element
Grok AI's distinctive features become particularly apparent when compared with other leading large language models. These comparative differences highlight Grok's unique positioning in the AI assistant landscape and provide perspective on its strengths and limitations relative to alternatives.
Comparative Analysis with Leading Competitors:
- Grok vs. GPT-4 (OpenAI):Real-time Information Access:Interaction Style:Response Approach to Sensitive Topics:Developer Ecosystem:
- Grok: Built-in web browsing capability allows direct access to current information.
- GPT-4: Initially limited to training data cutoff, later versions introduced Browse with Bing for optional web access.
- Difference: Grok's approach integrates web access more fundamentally into its architecture, while GPT-4's browsing capability was added as an extension.
- Grok: More casual, sometimes humorous "rebellious" personality with generally more direct responses.
- GPT-4: More neutral, professional tone with careful, sometimes more cautious responses.
- Difference: Grok aims for engagement through personality, while GPT-4 focuses on professional reliability.
- Grok: Generally more willing to engage with controversial topics, providing balanced perspectives rather than declining.
- GPT-4: More cautious approach to sensitive topics, sometimes declining to address contentious issues.
- Difference: Grok's "maximum truth-seeking" philosophy leads to broader topic engagement, while GPT-4 tends toward greater caution.
- Grok: Limited developer ecosystem, primarily accessible through X platform.
- GPT-4: Extensive API access, plugin ecosystem, and developer tools.
- Difference: GPT-4 offers significantly more integration options and developer resources at present.
- Grok vs. Claude (Anthropic):Knowledge Access:Philosophical Approach:Context Length:Response Style:
- Grok: Integrated web browsing for real-time information.
- Claude: Tool use capability allows web searches, document analysis, and other extensions.
- Difference: Both offer external information access, but through somewhat different architectural approaches.
- Grok: Emphasizes "maximum truth-seeking" and wider topic engagement.
- Claude: Focuses on helpfulness, harmlessness, and honesty with Constitutional AI approach.
- Difference: Different foundational values lead to somewhat different response patterns on complex topics.
- Grok: Approximately 8,000 token context window.
- Claude: Up to 100,000+ token context window in advanced versions.
- Difference: Claude offers substantially larger context capacity for processing lengthy documents or conversations.
- Grok: More casual, sometimes witty style with "rebellious" personality.
- Claude: Warm, helpful tone with thoughtful, nuanced responses.
- Difference: Different personality approaches create distinctive conversation experiences.
- Grok vs. Gemini (Google):Integration Approach:Multimodal Capabilities:Knowledge Source:Development Focus:
- Grok: Primarily integrated with X platform ecosystem.
- Gemini: Deeply integrated with Google's search and productivity ecosystem.
- Difference: Each reflects the strategic priorities and existing products of their parent companies.
- Grok: Basic image understanding in newer versions (Grok-1.5V).
- Gemini: Advanced multimodal capabilities from its foundational design.
- Difference: Gemini was designed as multimodal from inception, while Grok added this capability later.
- Grok: Combination of training data and web browsing.
- Gemini: Training data plus potential Google Search integration.
- Difference: Different approaches to leveraging their companies' existing information infrastructure.
- Grok: Emphasis on real-time information and "rebellious" approach.
- Gemini: Focus on multimodal understanding and Google ecosystem integration.
- Difference: Different product priorities reflect different strategic goals.
Key Differentiating Features:
Several features particularly distinguish Grok from most competitors:
- Integrated Real-time Information: While several models now offer web access capabilities through various means, Grok's approach makes this a central rather than supplementary feature. The integration of web browsing into Grok's core functionality reflects xAI's emphasis on overcoming the knowledge cutoff limitation that affects many language models.
- "Rebellious" Personality: Grok's more casual, sometimes humorous personality creates a distinctly different user experience compared to more neutral models. This approach reflects a deliberate design choice to create more engaging interactions and differentiate from competitors that may seem more reserved or cautious.
- Topic Engagement Philosophy: Grok's willingness to engage with a wider range of topics, including controversial ones, stems from its "maximum truth-seeking" philosophy. This approach contrasts with models that may more frequently decline to address sensitive topics, reflecting different underlying values about AI's role in discussion.
- X Platform Integration: Grok's deep integration with the X platform creates a unique distribution channel and user experience. This integration reflects the close relationship between xAI and X, distinguishing Grok's availability model from competitors with more independent deployment approaches.
- Development Velocity: Grok has demonstrated rapid iteration and capability expansion, with significant updates occurring on a compressed timeline. This rapid development reflects xAI's approach to quickly evolving the model's capabilities and responding to competitive pressures.
Architectural Comparison:
From an architectural perspective, Grok shares the transformer-based foundation common to modern LLMs but with some distinctive elements:
- Web Browsing Architecture: Grok's architecture includes specialized components for web search formulation, content extraction, and information synthesis that are more deeply integrated than some competitors' approaches.
- Parameter Efficiency: While not confirmed by xAI, Grok appears to achieve competitive performance with potentially fewer parameters than some alternatives, suggesting possible architectural efficiencies or training optimizations.
- Training Philosophy: Grok's training likely reflects different priorities in terms of safety alignment and response calibration, resulting in its more direct approach to controversial topics.
- Multimodal Extensions: The addition of image understanding capabilities in Grok-1.5V represents an architectural extension that brings Grok closer to competitors with native multimodal designs.
User Experience Differentiation:
From a user experience perspective, several elements create Grok's distinctive interaction:
- Conversation Flow: Grok's more casual, direct style creates a different conversational rhythm and engagement pattern compared to more formal alternatives.
- Information Presentation: When using web browsing, Grok's approach to presenting and attributing information creates a distinctive information delivery experience.
- Response Personalities: The "rebellious" personality manifests in subtle interaction differences that collectively create a recognizable character distinct from other AI assistants.
- Engagement Approach: Grok's willingness to engage with controversial topics creates different expectations and interaction patterns around sensitive questions.
These comparative differences highlight Grok's distinctive positioning in the AI assistant landscape. While sharing fundamental technological foundations with other large language models, Grok's unique features, particularly its real-time information access, "rebellious" personality, and topic engagement philosophy, create a recognizably different experience that reflects xAI's specific vision for AI interaction.
Technical Limitations
Knowledge Boundaries
Despite its advanced capabilities and real-time information access, Grok AI operates within certain knowledge boundaries that define the limits of what it can know and access. Understanding these boundaries is important for users to develop appropriate expectations and for technical decision-makers to evaluate Grok's suitability for specific applications.
Training Data Limitations:
Like all large language models, Grok's foundational knowledge is constrained by its training data:
- Training Data Cutoff:
- Grok's base model knowledge has a temporal cutoff corresponding to when its training data was collected.
- Information that emerged after this cutoff is not inherently part of Grok's parametric knowledge.
- While web browsing helps overcome this limitation for public information, it remains a fundamental constraint on the model's internal knowledge.
- Training Data Coverage:
- The comprehensiveness of Grok's knowledge varies across domains based on their representation in training data.
- Well-documented fields like mainstream science, popular culture, and widely discussed historical events are likely well-covered.
- More obscure, specialized, or niche topics may have less comprehensive coverage.
- Linguistic and Cultural Limitations:
- Grok's training likely emphasized English-language content with potential bias toward Western cultural contexts.
- Knowledge of non-Western cultural concepts, regional information, or less-represented languages may be less comprehensive.
- These limitations affect the model's ability to reason about culturally specific concepts or regional details.
Web Access Constraints:
While Grok's web browsing capability expands its knowledge boundaries, this feature has its own limitations:
- Access Restrictions:
- Grok cannot access content behind paywalls, login requirements, or other access controls.
- Websites that block automated access or require CAPTCHA verification would be inaccessible.
- These restrictions limit Grok's ability to access certain premium or protected content sources.
- Search Engine Limitations:
- Grok's web access depends on search engines to identify relevant content.
- Information that is not well-indexed or not prominent in search results may remain effectively inaccessible.
- This creates potential blind spots for valid information that doesn't achieve search visibility.
- Information Recency Challenges:
- Very recent information (minutes or hours old) may not yet be indexed by search engines.
- For rapidly evolving situations, even web access may not provide the most current details.
- This creates a minimum latency for truly current information.
- Web Content Evaluation:
- Grok must evaluate the credibility and relevance of web sources with imperfect information.
- This evaluation process may sometimes lead to reliance on less authoritative sources.
- The model may struggle to appropriately weigh contradictory information from different sources.
Domain-Specific Knowledge Boundaries:
Grok's knowledge has varying boundaries across different domains:
- Scientific and Technical Knowledge:
- Mainstream scientific principles and well-established technical information are generally well-covered.
- Highly specialized scientific domains may have less comprehensive coverage.
- Very recent scientific developments may depend entirely on web access rather than training data.
- Personal and Private Information:
- Grok has extremely limited knowledge about individual users beyond what they explicitly share in conversation.
- The model cannot access private records, personal accounts, or non-public personal information.
- This represents an important privacy boundary that Grok cannot and should not cross.
- Organizational Knowledge:
- Without specific integration, Grok cannot access internal organizational data, documents, or systems.
- The model has no knowledge of private enterprise information unless explicitly provided in conversation.
- This limitation affects Grok's utility for organization-specific applications without appropriate integration.
- Rapidly Evolving Information:
- For domains with extremely rapid change (financial markets, breaking news, live events), even web access may provide information that is minutes or hours old.
- This latency creates boundaries for use cases requiring truly real-time information.
Temporal Knowledge Boundaries:
Grok's knowledge has specific temporal limitations:
- Historical Knowledge:
- Historical information is generally well-represented in training data, though with typical biases toward well-documented periods and Western history.
- More obscure historical topics or regional histories may have less comprehensive coverage.
- Historical information is rarely updated on the web, making web access less valuable for historical queries.
- Current Events Knowledge:
- Knowledge of events between training data cutoff and the present depends entirely on web access.
- The comprehensiveness of this knowledge varies based on web coverage and search visibility.
- More widely reported events will have better coverage than obscure developments.
- Future Predictions:
- Grok has no special ability to predict future events beyond logical extrapolation from existing information.
- Any discussion of future events represents reasoning based on current data rather than definitive knowledge.
- This fundamental limitation applies to all predictive questions regardless of domain.
Specialized Knowledge Domains:
Certain specialized knowledge domains present particular boundaries:
- Proprietary Information:
- Grok has no access to confidential business information, unreleased products, or non-public corporate strategies.
- Any discussion of such topics is limited to publicly available information.
- This boundary is particularly relevant for competitive intelligence applications.
- Local and Regional Knowledge:
- Hyperlocal information about specific communities or regions may have limited coverage.
- While web access can help with some regional information, the depth of knowledge varies significantly by location.
- Well-documented major cities will have better coverage than remote or less-documented areas.
- Specialized Professional Knowledge:
- Highly technical professional domains (specialized medicine, advanced engineering, etc.) may have knowledge boundaries based on the availability of high-quality public information.
- The model may struggle with cutting-edge professional practices or very specialized terminology.
- These limitations are more pronounced in fields with limited public documentation.
Understanding these knowledge boundaries is essential for effective utilization of Grok. While its web browsing capability significantly expands its knowledge compared to models limited to training data, Grok still operates within definable information constraints. These boundaries should inform decisions about where and how to deploy Grok, particularly for applications requiring specialized or highly current information.
Reasoning Constraints
Despite its sophisticated capabilities, Grok AI operates within certain reasoning constraints that limit its problem-solving abilities in important ways. Understanding these constraints is essential for setting appropriate expectations and evaluating Grok's suitability for different applications.
Fundamental Reasoning Limitations:
Several core limitations affect Grok's reasoning across all domains:
- Lack of True Understanding:
- Despite impressive language processing, Grok lacks genuine understanding in the human sense.
- The model processes patterns and statistical relationships rather than comprehending meaning as humans do.
- This fundamental limitation underlies many specific reasoning constraints.
- Absence of Consciousness:
- Grok has no self-awareness, subjective experience, or consciousness.
- The model cannot truly reflect on its own reasoning processes or limitations.
- Any apparent self-reflection is a simulation based on pattern recognition rather than genuine introspection.
- No True Common Sense:
- While Grok can mimic common sense reasoning in many situations, it lacks the intuitive understanding of physical reality that humans develop through lived experience.
- The model may fail to recognize obvious physical impossibilities or practical constraints that would be immediately apparent to humans.
- This limitation becomes more pronounced in scenarios requiring nuanced understanding of how the physical world works.
Complex Reasoning Constraints:
Several specific constraints affect Grok's ability to handle complex reasoning tasks:
- Multi-step Reasoning Degradation:
- Grok's performance typically degrades as reasoning chains become longer and more complex.
- The model may lose track of intermediate steps or make errors in lengthy deductive sequences.
- This degradation becomes more pronounced as the number of interdependent steps increases.
- Uncertainty Handling:
- Grok often struggles with appropriately representing uncertainty in its reasoning.
- The model may present speculative conclusions with unwarranted confidence.
- Conversely, it may sometimes express uncertainty about well-established facts.
- Causal Reasoning Limitations:
- Grok has limited ability to understand true causality beyond correlation.
- The model may identify spurious correlations as causal relationships.
- This constraint affects reasoning about complex systems with multiple causal factors.
- Counterfactual Reasoning:
- Reasoning about hypothetical scenarios that contradict reality can be challenging for Grok.
- The model may struggle with maintaining consistent alternative world models in complex counterfactual scenarios.
- These limitations affect certain types of creative problem-solving and hypothetical analysis.
Domain-Specific Reasoning Constraints:
Different domains present specific reasoning challenges for Grok:
- Mathematical Reasoning:
- Grok may make errors in complex mathematical calculations, particularly with multiple steps.
- The model can struggle with certain types of mathematical proofs or abstract mathematical concepts.
- Performance degrades as mathematical complexity increases, especially without step-by-step verification.
- Spatial Reasoning:
- Grok has limited ability to reason about complex spatial relationships or geometric problems.
- The model lacks true visualization capabilities, relying instead on learned patterns about spatial language.
- This constraint affects performance on problems requiring mental rotation, spatial transformation, or complex geometric analysis.
- Temporal Reasoning:
- Complex reasoning about time sequences, particularly with multiple interdependent events, can be challenging.
- The model may struggle with sophisticated temporal logic or complex scheduling constraints.
- These limitations affect applications requiring detailed temporal planning or analysis.
- Ethical Reasoning:
- While Grok can discuss ethical frameworks, it lacks genuine moral understanding or values.
- The model's ethical reasoning reflects patterns in its training data rather than true moral comprehension.
- This constraint is particularly relevant for applications involving complex ethical judgments.
Meta-Reasoning Limitations:
Grok faces significant constraints in reasoning about its own reasoning:
- Limited Self-evaluation:
- Grok has limited ability to accurately assess the quality or correctness of its own reasoning.
- The model may fail to recognize errors in its logic or factual claims.
- This constraint affects the reliability of Grok's confidence assessments about its own conclusions.
- Strategy Selection:
- Grok may not always select the optimal reasoning strategy for a given problem.
- The model sometimes applies learned approaches that are suboptimal for the specific question at hand.
- This limitation affects efficiency and effectiveness in complex problem-solving scenarios.
- Knowledge Boundary Awareness:
- Grok may have incomplete awareness of the boundaries of its own knowledge.
- The model sometimes attempts to reason about topics beyond its knowledge scope without appropriate qualification.
- This constraint can lead to overconfident reasoning in domains where Grok has limited information.
Practical Implementation Constraints:
Several practical factors further constrain Grok's reasoning in real-world implementations:
- Context Window Limitations:
- Grok's reasoning is constrained by its finite context window (approximately 8,000 tokens).
- Complex problems requiring reference to extensive background information may exceed this capacity.
- This limitation affects reasoning tasks that require maintaining awareness of numerous facts or constraints simultaneously.
- Processing Constraints:
- Unlike humans, Grok cannot "take time to think" about problems beyond its normal processing flow.
- The model generates responses in a single forward pass without the iterative reflection humans employ for difficult problems.
- This constraint affects performance on problems that humans would solve through extended contemplation.
- External Tool Limitations:
- Without specialized extensions, Grok cannot use external tools that might compensate for its reasoning limitations.
- The model cannot run simulations, access specialized software, or employ computational aids beyond its internal processing.
- This constraint affects problems that might benefit from specialized tools or external verification.
Cybersecurity Perspective on Reasoning Constraints:
From a cybersecurity perspective, several reasoning constraints have particular relevance:
- Security Implication Analysis:
- Grok may struggle to fully reason through complex security implications, particularly those involving multiple interacting systems or novel attack vectors.
- The model's reasoning about security consequences may miss subtle or non-obvious implications.
- This limitation affects Grok's utility for comprehensive security analysis without human oversight.
- Adversarial Scenario Reasoning:
- Reasoning about sophisticated adversarial scenarios, where intelligent actors actively work to circumvent security measures, presents particular challenges.
- Grok may not fully capture the strategic thinking of determined adversaries.
- This constraint affects applications involving advanced threat modeling or security red-teaming.
- Security Trade-off Evaluation:
- Complex security decisions often involve nuanced trade-offs between different security objectives, usability, and business requirements.
- Grok may struggle to comprehensively reason about these multi-dimensional trade-offs.
- This limitation is relevant when using Grok to support security architecture decisions.
Understanding these reasoning constraints is essential for appropriate deployment of Grok. While the model demonstrates impressive capabilities in many reasoning tasks, these limitations define boundaries for applications requiring sophisticated problem-solving, particularly without human verification. Organizations should consider these constraints when evaluating Grok for applications involving critical reasoning tasks or complex decision support.
Ethical Guardrails
Grok AI incorporates various ethical guardrails that define boundaries for its behavior and responses. These guardrails represent an important aspect of Grok's design, reflecting both technical safety considerations and xAI's philosophical approach to responsible AI development.
Core Safety Mechanisms:
Despite its "rebellious" positioning, Grok maintains fundamental safety mechanisms:
- Harmful Content Restrictions:
- Grok refuses to generate content designed to cause direct harm to individuals or groups.
- The model will not provide detailed instructions for creating weapons, synthesizing dangerous substances, or conducting illegal activities.
- These restrictions represent non-negotiable safety boundaries in Grok's design.
- Exploitation Prevention:
- Guardrails prevent Grok from facilitating exploitation of vulnerable individuals or groups.
- The model refuses to generate content promoting child exploitation, human trafficking, or similar abuses.
- These protections apply regardless of how queries are framed or contextualized.
- Hate Speech Limitations:
- Grok will not generate content that promotes hatred or violence against individuals or groups based on protected characteristics.
- The model aims to refuse genuine hate speech while still engaging with discussions about controversial topics.
- This balance reflects xAI's attempt to maintain open discussion while preventing harmful outputs.
- Self-harm Restrictions:
- Guardrails prevent Grok from providing detailed instructions for self-harm or suicide.
- The model aims to respond with appropriate resources rather than harmful guidance when users express distress.
- These protections represent an important safety boundary for vulnerable users.
Implementation Philosophy:
xAI's approach to ethical guardrails appears to reflect a distinctive philosophy:
- "Maximum Truth-seeking" Orientation:
- Grok's ethical guardrails are implemented with an emphasis on allowing broad discussion while preventing clearly harmful outputs.
- The model aims to engage with controversial topics rather than avoiding them entirely.
- This approach reflects xAI's stated goal of creating an AI system focused on truth-seeking rather than excessive caution.
- Reduced Political Filtering:
- xAI has positioned Grok as having less political bias filtering than some competitors.
- The model aims to present multiple perspectives on political and social issues rather than declining to engage.
- This approach reflects Elon Musk's concerns about perceived political bias in other AI systems.
- Transparency About Limitations:
- When Grok declines a request due to ethical guardrails, it typically provides explicit explanation rather than subtle redirection.
- This transparency aligns with the "rebellious" positioning, acknowledging restrictions directly.
- The approach aims to maintain user trust through clear communication about boundaries.
Specific Guardrail Categories:
Grok's ethical guardrails appear to span several specific categories:
- Illegal Activity Boundaries:
- Grok refuses to provide detailed instructions for clearly illegal activities.
- The model will not generate content that could reasonably be expected to facilitate specific crimes.
- These guardrails may allow discussion of illegal activities in abstract or educational contexts while refusing actionable guidance.
- Privacy Protections:
- Ethical guardrails prevent Grok from encouraging privacy violations or unauthorized surveillance.
- The model will not provide detailed instructions for hacking personal accounts, stalking individuals, or similar privacy intrusions.
- These protections apply even when requests are framed as hypothetical or educational.
- Manipulation Limitations:
- Guardrails restrict Grok from generating content designed to manipulate or deceive vulnerable individuals.
- The model will not provide detailed guidance for scams, fraud schemes, or psychological manipulation tactics.
- These limitations apply regardless of how such requests are contextualized.
- Content Moderation Guidelines:
- Ethical guardrails include restrictions on generating explicit sexual content, particularly involving minors.
- The model maintains boundaries around graphic violence, explicit content, and other areas requiring content moderation.
- These guidelines aim to prevent misuse while allowing appropriate discussion of sensitive topics.
Balancing Approaches:
Grok's ethical guardrails reflect attempts to balance several considerations:
- Safety vs. Utility:
- The guardrails aim to prevent harmful outputs while maximizing the model's usefulness for legitimate purposes.
- This balance requires distinguishing between genuinely dangerous requests and legitimate queries about sensitive topics.
- The implementation attempts to avoid over-restriction that would limit Grok's utility for appropriate uses.
- Openness vs. Protection:
- Grok's approach attempts to balance open discussion with appropriate protective boundaries.
- The model aims to engage with controversial topics while maintaining safeguards against harmful outputs.
- This balance reflects xAI's philosophical position on truth-seeking and open discourse.
- Consistency vs. Context:
- Ethical guardrails must balance consistent application of safety principles with contextual understanding.
- The model attempts to recognize when seemingly problematic queries actually have legitimate educational or informational purposes.
- This contextual approach aims to reduce false positives in safety filtering.
Implementation Mechanisms:
Grok's ethical guardrails are likely implemented through several technical approaches:
- Training Data Filtering:
- The training process likely excluded certain categories of harmful content or included them with appropriate contextual framing.
- This approach shapes the model's underlying tendencies before additional safety measures are applied.
- Reinforcement Learning from Human Feedback (RLHF):
- RLHF techniques were likely used to align Grok's outputs with human preferences regarding appropriate responses.
- This process helps calibrate the model's behavior across various scenarios, including potential misuse attempts.
- Rule-based Filtering:
- Certain categories of content are likely subject to rule-based restrictions that prevent harmful outputs.
- These explicit rules create clear boundaries for the most obviously problematic content categories.
- Context-aware Safety Systems:
- More sophisticated safety mechanisms likely evaluate requests in context rather than using simple keyword filtering.
- These systems attempt to understand the intent and potential impact of requests before determining responses.
- Prompt Injection Defenses:
- Security measures likely protect against attempts to circumvent ethical guardrails through prompt engineering or injection attacks.
- These defenses aim to maintain safety boundaries even when users attempt to bypass them through technical manipulation.
Importance for Implementation:
Understanding Grok's ethical guardrails is important for several reasons:
- Appropriate Use Planning:
- Organizations implementing Grok should understand its ethical boundaries to develop appropriate use policies.
- This understanding helps set realistic expectations about what the model will and will not do.
- Risk Management:
- Knowledge of Grok's guardrails informs risk assessments for organizational deployments.
- This understanding helps identify where additional safeguards or human oversight may be necessary.
- Responsible Deployment:
- Organizations have an ethical responsibility to deploy AI systems like Grok in ways that respect and reinforce appropriate boundaries.
- This includes avoiding systematic attempts to circumvent legitimate safety measures.
Grok's ethical guardrails represent an important aspect of its design, reflecting xAI's approach to balancing safety with utility and open discussion. While positioned as more "rebellious" than some alternatives, Grok still maintains fundamental safety boundaries that prevent the most clearly harmful outputs, particularly in categories with potential for direct harm or exploitation.
Performance Thresholds
Grok AI, like all current large language models, operates within certain performance thresholds that define the boundaries of its capabilities. Understanding these thresholds is essential for setting appropriate expectations and identifying scenarios where performance degradation may occur.
Complexity Thresholds:
Grok's performance generally degrades as tasks exceed certain complexity thresholds:
- Reasoning Step Length:
- Performance typically declines as the number of required reasoning steps increases.
- For logical deductions, accuracy tends to decrease significantly beyond 5-7 explicit reasoning steps.
- This threshold affects complex problem-solving tasks that require extended chains of logical inference.
- Mathematical Complexity:
- Calculation accuracy decreases with computational complexity and digit length.
- Performance is generally reliable for basic arithmetic and simple algebraic operations.
- Accuracy declines for complex equations, multi-step calculations, or problems requiring specialized mathematical techniques.
- Contextual Interconnections:
- Performance degrades as the number of interdependent contextual elements increases.
- The model handles straightforward relationships well but may struggle when multiple context elements interact in complex ways.
- This threshold affects tasks requiring integration of numerous facts with complex interrelationships.
- Abstraction Levels:
- Grok performs better with concrete concepts than with highly abstract or theoretical constructs.
- As abstraction levels increase, especially in philosophical or theoretical domains, performance becomes less reliable.
Technical Processing Thresholds:
Several technical factors establish performance boundaries for Grok:
- Context Window Utilization:
- Grok's performance may degrade as context utilization approaches its ~8,000 token limit.
- Long conversations or complex documents that fill much of the context window leave less space for processing new information.
- This technical threshold becomes particularly relevant in extended problem-solving sessions or document analysis tasks.
- Knowledge Recency:
- Performance on queries about recent events depends on the freshness of web information.
- Very recent events (within hours) may have limited or inconsistent coverage in search results.
- This creates a temporal threshold where performance decreases for very recent developments.
- Search Result Quality:
- When using web browsing, performance correlates strongly with search result quality and relevance.
- Queries about obscure topics or those with limited web presence may yield less reliable information.
- This dependency creates an information availability threshold that affects performance.
- Query Ambiguity:
- Performance typically declines as query ambiguity increases.
- Grok performs best with clear, well-specified requests and questions.
- Vague, ambiguous, or underspecified queries lead to more variable performance.
Domain-Specific Performance Thresholds:
Different knowledge domains present specific performance thresholds:
- Specialized Technical Domains:
- Performance generally declines as domain specialization increases beyond mainstream technical knowledge.
- Grok handles general technical concepts well but may struggle with highly specialized subdisciplines.
- This creates thresholds where expertise depth exceeds the model's capabilities.
- Creative Quality:
- Creative content generation maintains quality up to certain complexity thresholds.
- Performance is strong for straightforward creative tasks but may decline for highly sophisticated creative requests.
- Quality thresholds vary by creative medium, with simpler formats generally yielding more consistent results.
- Language Proficiency:
- Performance varies across languages, with strongest capabilities in English.
- For non-English languages, there are likely proficiency thresholds where complexity exceeds the model's capabilities.
- These thresholds create performance boundaries for multilingual applications.
- Code Generation:
- Code quality generally decreases with program complexity and specialization.
- Performance is reliable for common programming patterns and standard libraries.
- Quality thresholds emerge for highly specialized frameworks, optimization requirements, or complex algorithms.
Reliability Considerations:
Several factors affect the reliability of Grok's performance across these thresholds:
- Confidence-Performance Correlation:
- Grok's apparent confidence in responses does not always correlate with actual accuracy.
- The model may express high confidence in incorrect responses, particularly near performance thresholds.
- This disconnect creates challenges for assessing response reliability without external verification.
- Threshold Variability:
- Performance thresholds are not absolute but probabilistic, with gradual rather than sudden degradation.
- Threshold boundaries vary across specific tasks within broader categories.
- This variability means performance near thresholds is less predictable than well within capabilities.
- Interaction Effects:
- Multiple thresholds may interact, with combined effects more severe than individual limitations.
- For example, a complex reasoning task in a specialized domain presents compounded challenges.
- These interaction effects create more pronounced performance boundaries for multifaceted tasks.
- Recovery Mechanisms:
- Grok sometimes employs effective recovery strategies when approaching performance thresholds.
- These include breaking problems into steps, requesting clarification, or acknowledging uncertainty.
- The effectiveness of these strategies varies and may not fully compensate for fundamental limitations.
Understanding these performance thresholds is crucial for effective implementation, as it helps establish appropriate boundaries for Grok's applications and identifies scenarios where additional verification or human oversight may be necessary.
Expert Analysis: Cybersecurity Perspective on Limitations
From a cybersecurity perspective, Grok AI's technical limitations have several important implications that should inform its implementation in security contexts. Having built AI-powered cybersecurity solutions, I can offer the following assessment of how these limitations affect Grok's potential applications in this domain.
Knowledge Boundary Implications:
Grok's knowledge boundaries create specific security considerations:
- Security Intelligence Currency:
- While Grok's web access helps overcome knowledge cutoff limitations, security threat intelligence requires extremely current information.
- The model may not capture very recent vulnerability disclosures, exploit developments, or emerging attack techniques.
- This limitation necessitates complementary real-time threat intelligence sources for critical security applications.
- Specialized Security Domain Knowledge:
- Cybersecurity encompasses numerous highly specialized subdomains with their own terminology and concepts.
- Grok's knowledge depth varies across these domains, with likely stronger coverage of mainstream security topics.
- Security implementations should verify Grok's domain-specific knowledge rather than assuming comprehensive expertise.
- Proprietary Security Information:
- Many organizations rely on proprietary security tools, architectures, and practices not documented publicly.
- Without specialized integration, Grok cannot access this organization-specific security information.
- This limitation affects Grok's utility for organization-specific security applications without appropriate customization.
Reasoning Constraint Implications:
Grok's reasoning constraints have particular relevance for cybersecurity applications:
- Complex Attack Chain Analysis:
- Modern cyber attacks often involve complex multi-stage attack chains with numerous interdependent steps.
- Grok's reasoning performance degrades with chain complexity, potentially missing subtle attack path components.
- This limitation affects the reliability of Grok for comprehensive attack path analysis without human verification.
- Security Trade-off Assessment:
- Cybersecurity often involves nuanced trade-offs between security levels, usability, and operational requirements.
- Grok may struggle to fully reason through these multi-dimensional trade-off scenarios.
- Human judgment remains essential for security architecture decisions involving complex trade-offs.
- Novel Attack Vector Identification:
- Identifying previously unknown attack vectors requires creative yet technically sound security reasoning.
- Grok's reasoning limitations may affect its ability to identify novel attack paths not represented in existing literature.
- This constrains its utility for advanced threat modeling and zero-day vulnerability discovery.
Ethical Guardrail Implications:
Grok's ethical guardrails create important considerations for security applications:
- Offensive Security Testing:
- Legitimate security testing often requires understanding attack techniques for defensive purposes.
- Grok's ethical guardrails may limit detailed guidance for certain security testing activities.
- This creates potential constraints for using Grok in offensive security training or red team operations.
- Security Education Balance:
- Effective security education requires explaining vulnerabilities without enabling misuse.
- Grok attempts to balance educational value with potential harm, but this calibration may not always align with specific security training needs.
- Organizations may need to develop clear guidelines for appropriate security educational use cases.
- Dual-Use Security Information:
- Many cybersecurity concepts have both legitimate defensive applications and potential offensive misuse.
- Grok's approach to such dual-use information may not perfectly align with organizational security policies.
- This necessitates clear organizational guidelines for appropriate security information handling.
Performance Threshold Implications:
Grok's performance thresholds have specific security relevance:
- Complex Security Analysis:
- Comprehensive security analysis often involves integrating numerous technical factors across multiple domains.
- As complexity approaches Grok's performance thresholds, reliability for security-critical analyses decreases.
- This reinforces the need for human verification of complex security assessments.
- Security Documentation Quality:
- Security documentation often requires precise technical language and comprehensive coverage.
- Grok's performance in generating such documentation may decrease with technical complexity and specificity requirements.
- Quality verification becomes increasingly important as security documentation complexity increases.
- Incident Response Support:
- Security incidents often present time-critical, complex scenarios with incomplete information.
- Grok's performance under these conditions may approach various thresholds simultaneously.
- This affects reliability for unsupervised incident response applications without appropriate verification processes.
Strategic Implementation Guidance:
Based on these limitations, I recommend the following approaches for cybersecurity implementations:
- Augmentation Rather Than Replacement:
- Position Grok as an augmentation tool for security professionals rather than a replacement for human expertise.
- Design workflows where Grok accelerates initial analysis while humans verify critical security decisions.
- This approach leverages Grok's strengths while mitigating the impact of its limitations.
- Tiered Verification Processes:
- Implement verification requirements that scale with security criticality and complexity.
- Develop explicit guidelines for when Grok's security outputs require human review.
- This creates appropriate safeguards while maximizing efficiency for routine security tasks.
- Complementary Knowledge Sources:
- Integrate Grok with specialized security knowledge bases for organization-specific information.
- Develop approaches for combining Grok's general capabilities with specialized security tools.
- This compensates for domain-specific knowledge limitations while leveraging Grok's strengths.
- Clear Boundary Documentation:
- Explicitly document the security tasks where Grok performs reliably and those where limitations are significant.
- Train security teams on these boundaries to develop appropriate usage patterns.
- This establishes realistic expectations and promotes effective implementation.
These considerations don't diminish Grok's utility for cybersecurity applications but rather define how it can be most effectively integrated into security operations. With appropriate implementation approaches that account for these limitations, Grok can provide significant value across various cybersecurity use cases while maintaining necessary security assurance levels.
Version History and Evolution
Release Timeline
Grok AI has undergone rapid development since its initial release, with several significant versions introducing new capabilities and performance improvements. This accelerated evolution reflects xAI's commitment to quickly advancing Grok's capabilities in a competitive AI landscape.
Grok-1 (November 2023):
- Initial release announced on November 4, 2023
- Made available to X Premium+ subscribers in early access
- Introduced with core conversational capabilities and integrated web browsing
- Positioned as having a "rebellious" personality and real-time information access
- Initially available to a limited user base as xAI scaled access
Grok-1.5 (March 2024):
- Released in March 2024, approximately four months after initial launch
- Significant update focused on improving reasoning capabilities and reducing hallucinations
- Enhanced instruction-following abilities for more complex tasks
- Improved factual accuracy and reliability across various knowledge domains
- Maintained the "rebellious" personality while enhancing overall performance
Grok-1.5V (April 2024):
- Released in April 2024 as a multimodal extension of Grok-1.5
- Added image understanding capabilities, allowing Grok to process and discuss visual content
- Maintained the core capabilities of Grok-1.5 while expanding into multimodal functionality
- Represented xAI's first step beyond text-only interaction into broader multimodal AI
Grok System Updates (Ongoing):
- Throughout its evolution, Grok has received numerous smaller updates and improvements
- These ongoing enhancements include refinements to web browsing capabilities, UI improvements, and performance optimizations
- xAI has maintained a relatively rapid update cadence compared to some competitors
- These iterative improvements complement the major version releases
| Date | Milestone | Why it mattered |
|---|---|---|
| Nov 3 2023 | Initial Grok release (beta inside X) | First public look at xAI’s humor-infused chatbot, powered by early Grok LLM. (Wikipedia) |
| Mar 17 2024 | Grok-1 open weights | xAI open-sourced a 314 B-parameter MoE model—huge for transparency & community tinkering. (xAI) |
| Mar 28 2024 | Grok-1.5 | 128 K-token context + stronger math/coding ↗. (xAI) |
| Apr 12 2024 | Grok-1.5V (Vision preview) | First step into multimodal: reads docs, diagrams, photos. (xAI) |
| Aug 14 2024 | Grok-2 & 2 mini | Built-in vision + Flux image generation; big ranking jump. (xAI, SiliconANGLE) |
| Oct 28 2024 | Image understanding for all users | Everyday X subscribers could upload pics for analysis. (Wikipedia) |
| Feb 19 2025 | Grok 3 Beta—Age of Reasoning Agents | 10× compute, leading arena Elo; long-form “think” mode. (xAI) |
| Apr 23 2025 | Grok Vision + Voice | Real-time camera analysis & multilingual voice chat—full multimodal UX. (AIbase) |
This accelerated development timeline demonstrates xAI's approach to rapidly evolving Grok's capabilities while maintaining its core identity and distinctive features. The progression from text-only to multimodal capabilities within approximately six months of initial release shows an aggressive development strategy aimed at quickly achieving competitive feature parity with other leading AI systems.
Capability Growth
Throughout its evolution, Grok AI has demonstrated significant capability growth across several key dimensions. This expansion of capabilities reflects both xAI's development priorities and competitive pressures in the rapidly advancing AI assistant market.
Natural Language Understanding:
- Initial Capability (Grok-1): Strong fundamental language understanding with contextual awareness and conversational ability.
- Evolution: Progressive improvements in understanding complex instructions, nuanced queries, and ambiguous language.
- Current State: Sophisticated language understanding comparable to leading LLMs, with particular strength in conversational contexts.
Knowledge Access:
- Initial Capability (Grok-1): Integrated web browsing for real-time information beyond training data cutoff.
- Evolution: Refinements in search query formulation, source evaluation, and information synthesis from multiple sources.
- Current State: Effective real-time information access with improved reliability and source integration.
Reasoning Capabilities:
- Initial Capability (Grok-1): Basic reasoning across various domains with typical LLM limitations.
- Evolution: Significant focus area for Grok-1.5, with improvements in logical reasoning, problem-solving, and error reduction.
- Current State: Enhanced reasoning with better multi-step logic, though still subject to fundamental LLM reasoning constraints.
Creative Generation:
- Initial Capability (Grok-1): Standard creative content generation across text formats.
- Evolution: Gradual improvements in quality, consistency, and stylistic range for creative tasks.
- Current State: Competitive creative capabilities with particular strength in conversational and engaging content styles.
Multimodal Understanding:
- Initial Capability (Grok-1): Text-only interaction without image processing abilities.
- Evolution: Introduction of image understanding with Grok-1.5V, representing a major capability expansion.
- Current State: Basic multimodal functionality allowing processing of images alongside text, though likely still developing compared to models designed as multimodal from inception.
Instruction Following:
- Initial Capability (Grok-1): Ability to follow straightforward instructions with typical LLM limitations.
- Evolution: Improved ability to follow complex, multi-part instructions highlighted as a focus area for Grok-1.5.
- Current State: Enhanced instruction-following with better adherence to specific requirements and constraints.
Factual Reliability:
- Initial Capability (Grok-1): Standard LLM factual reliability with hallucination challenges.
- Evolution: Reduced hallucinations and improved factual accuracy emphasized in Grok-1.5 updates.
- Current State: Improved reliability, particularly when leveraging web access for verification, though still subject to fundamental LLM limitations.
User Experience Integration:
- Initial Capability (Grok-1): Basic integration with X platform for Premium+ subscribers.
- Evolution: Progressive UI/UX improvements and tighter integration with the X ecosystem.
- Current State: Streamlined user experience with enhancements to conversation management and response presentation.
This capability growth demonstrates xAI's focus on rapidly evolving Grok from its initial release to a more comprehensive AI assistant with competitive features. The emphasis on reasoning improvements and multimodal expansion reflects both user feedback priorities and competitive pressures in the AI assistant market, where these capabilities have become increasingly important differentiators.
Performance Improvements
Grok AI has seen notable performance improvements across its version history, with benchmarks and user experiences indicating significant advancements in several key areas. These improvements reflect xAI's focus on rapidly enhancing Grok's capabilities to compete effectively in the AI assistant market.
Reasoning Performance:
- Initial State (Grok-1): Demonstrated reasonable reasoning abilities typical of large language models but with significant limitations in complex reasoning chains.
- Improvement Focus: The Grok-1.5 update explicitly targeted reasoning enhancement as a primary objective.
- Observed Gains: Improved performance on logical reasoning tasks, mathematical problem-solving, and multi-step deduction.
- Benchmark Indicators: While specific benchmark numbers aren't publicly disclosed by xAI, third-party evaluations suggest meaningful gains on reasoning-focused benchmarks between versions.
Hallucination Reduction:
- Initial State (Grok-1): Like other LLMs, the initial version experienced hallucination issues where it would confidently state incorrect information.
- Improvement Focus: Hallucination reduction was highlighted as a key priority for the Grok-1.5 update.
- Observed Gains: Reduced frequency of fabricated facts and improved accuracy when reporting factual information.
- Evaluation Approach: This improvement is typically measured through factual accuracy tests across diverse knowledge domains.
Instruction Following:
- Initial State (Grok-1): Basic instruction following capabilities with inconsistencies in complex scenarios.
- Improvement Focus: Enhanced ability to follow detailed or multi-part instructions was targeted in updates.
- Observed Gains: More reliable adherence to specific instructions, better handling of constraints, and improved task completion.
- Performance Indicators: Improved scores on instruction-following benchmarks that assess adherence to complex requirements.
Web Browsing Effectiveness:
- Initial State (Grok-1): Fundamental web access capability for retrieving current information.
- Improvement Focus: Ongoing refinements to search formulation, content extraction, and information synthesis.
- Observed Gains: More relevant search queries, better extraction of pertinent information, and improved integration of web-sourced content.
- User Experience Impact: More accurate and comprehensive responses for queries requiring current information.
Multimodal Performance:
- Initial State (Grok-1): Text-only capabilities without image processing.
- Improvement Focus: Introduction of image understanding capabilities with Grok-1.5V.
- Observed Gains: New ability to process, describe, and reason about image content alongside text.
- Capability Baseline: Initial multimodal performance likely focuses on fundamental image understanding rather than advanced visual reasoning.
Response Quality:
- Initial State (Grok-1): Standard response quality with Grok's distinctive conversational style.
- Improvement Focus: Enhanced coherence, relevance, and helpfulness across diverse query types.
- Observed Gains: More consistent quality, better response organization, and improved precision in addressing user queries.
- Evaluation Metrics: Typically assessed through human evaluations of response helpfulness and relevance.
Contextual Understanding:
- Initial State (Grok-1): Basic ability to maintain conversation context and follow topic threads.
- Improvement Focus: Enhanced ability to track complex conversations and maintain awareness of established information.
- Observed Gains: Better handling of lengthy conversations, improved reference resolution, and more coherent multi-turn interactions.
- Performance Indicators: Improved coherence in extended conversations with multiple topic shifts or complex references.
While xAI does not publicly release comprehensive benchmark results for all Grok versions, the evolution from Grok-1 to Grok-1.5 and beyond shows a clear trajectory of performance improvement across key dimensions. These enhancements reflect both xAI's development priorities and response to user feedback, with particular emphasis on reasoning capabilities, factual reliability, and multimodal expansion. The rapid pace of these improvements demonstrates xAI's commitment to quickly establishing Grok as a competitive option in the AI assistant market.
Timeline Visualization
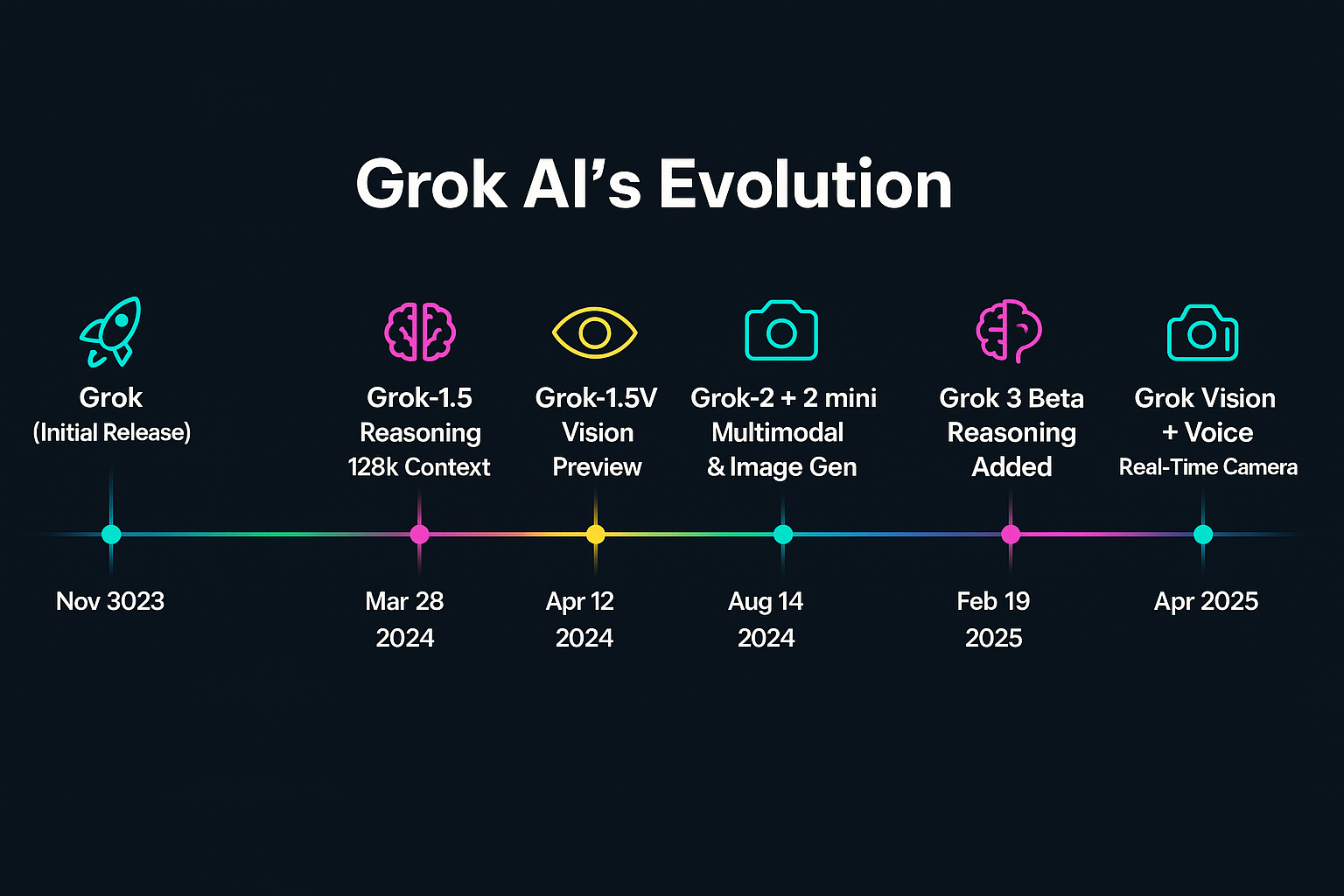
Visual representation of Grok AI's evolution showing major version releases and capability expansions from November 2023 through early 2025. The timeline illustrates the progression from initial release through reasoning enhancements to multimodal capabilities.
Access and Availability
Platform Availability
Grok AI is currently available through several platforms and access methods, with availability expanding over time as xAI scales its deployment. Understanding these access options is essential for organizations considering Grok implementation.
X Platform Integration:
- Primary Access Method: Grok is most prominently available through the X platform (formerly Twitter).
- Integration Type: Native integration within the X application and website.
- Access Point: Dedicated Grok tab or section within the X interface.
- Platform Support: Available across X's web interface, mobile applications, and other official access points.
- User Experience: Designed for seamless interaction within the broader X ecosystem.
Standalone Web Interface:
- Availability Status: xAI has developed a standalone web interface for Grok access.
- Access Scope: Initially limited to specific user groups with planned expansion.
- URL Access: Typically accessed through a dedicated domain separate from the X platform.
- Feature Parity: Generally offers the same core capabilities as the X-integrated version.
- Design Approach: Focused specifically on Grok interaction without X platform elements.
Mobile Application Access:
- X App Integration: Primary mobile access through the integrated Grok feature in X's official apps.
- Dedicated App Status: Potential for dedicated Grok mobile applications in development.
- Platform Support: Available across major mobile operating systems through X's platform support.
- Mobile Optimization: Interface designed for effective interaction on smaller screens.
API Access:
- Current Status: Limited API access with planned expansion for developers and enterprises.
- Access Model: Likely to follow standard API authorization and authentication patterns.
- Use Case Support: Designed to enable integration of Grok capabilities into third-party applications and services.
- Documentation: API documentation and developer resources expanding as access broadens.
- Enterprise Focus: API access particularly relevant for organizational implementation and custom integration.
Enterprise Deployment Options:
- Current Status: Enterprise-specific deployment options in development.
- Anticipated Models: Likely to include private instances, enterprise administration tools, and custom integration options.
- Security Features: Enterprise deployments typically include enhanced security, administration, and compliance features.
- Implementation Timeline: Enterprise-focused options expected to expand as xAI matures its offerings.
The availability of Grok continues to evolve as xAI expands access and develops new deployment options. Organizations interested in Grok implementation should monitor these developments and evaluate which access method best aligns with their specific requirements for integration, security, and user experience.
Subscription Models
Grok AI is available through several subscription models, with options evolving as xAI expands its service offerings. Understanding these subscription approaches is important for planning Grok implementation and assessing associated costs.
X Premium+ Subscription:
- Primary Access Model: Grok is currently available primarily through X Premium+ subscriptions.
- Pricing Structure: Approximately $16 per month (web) or $22 per month (iOS/Android) as of early 2025.
- Bundled Benefits: Includes other X Premium+ features beyond Grok access (verification checkmark, reduced ads, prioritized rankings, etc.).
- User Scope: Individual user-based subscription rather than organization-wide licensing.
- Payment Processing: Managed through X's standard subscription billing system.
Standalone Grok Subscription:
- Availability Status: Standalone Grok subscription options in development or limited release.
- Anticipated Pricing: Competitive with other AI assistant subscription services.
- Access Scope: Focused specifically on Grok access without X platform features.
- User Model: Likely to include both individual and multi-user options.
- Subscription Management: Direct relationship with xAI rather than through X platform.
Enterprise Licensing:
- Development Status: Enterprise-specific licensing models in development or limited availability.
- Pricing Approach: Likely to include per-seat, per-usage, and enterprise-wide options.
- Volume Discounts: Graduated pricing tiers based on user count or usage volume.
- Contract Terms: Enterprise agreements typically include service level agreements, support provisions, and customized terms.
- Commitment Options: Both annual and multi-year commitment options likely available.
API Usage-Based Pricing:
- Model Structure: For API access, pricing likely follows usage-based models standard in the industry.
- Measurement Metrics: Common pricing factors include request volume, token count, and feature utilization.
- Tier Structure: Graduated pricing tiers with volume discounts for larger implementations.
- Free Tier Possibility: Potential for limited free tier for development and evaluation purposes.
- Enterprise Customization: Custom pricing arrangements for high-volume enterprise implementations.
Educational and Research Access:
- Program Status: Special access programs for educational and research institutions in development.
- Pricing Approach: Discounted or specialized pricing for qualifying organizations.
- Usage Limitations: Potentially includes specific terms regarding appropriate educational/research use.
- Application Process: Likely requires verification of institutional status and intended use.
Trial and Evaluation Options:
- Availability: Various trial options to evaluate Grok before subscription commitment.
- Duration: Typically time-limited (7-30 days) or usage-limited evaluation periods.
- Feature Access: Full feature access during trial with potential usage caps.
- Conversion Process: Streamlined transition from trial to paid subscription.
These subscription models continue to evolve as xAI expands Grok's availability and develops its business model. Organizations considering Grok implementation should evaluate which subscription approach best aligns with their usage patterns, user counts, and integration requirements. As with any rapidly evolving service, subscription options and pricing are subject to change, requiring ongoing monitoring of xAI's offerings.
Enterprise Access
Enterprise access to Grok AI represents an important dimension of xAI's deployment strategy, with options evolving to meet the needs of organizational users. Understanding the current and developing enterprise access models is essential for technical decision-makers evaluating Grok for business applications.
Current Enterprise Access Status:
Enterprise access to Grok is in a developing stage, with options expanding as xAI matures its organizational offerings. Current enterprise access primarily occurs through:
- Individual X Premium+ Subscriptions:
- Organizations can provide X Premium+ accounts to employees requiring Grok access.
- This approach works for small teams but becomes less manageable at larger scales.
- Limited centralized administration creates management challenges for larger deployments.
- Early Enterprise Programs:
- xAI has begun establishing relationships with select enterprise partners.
- These early programs provide insight into organizational requirements while offering limited enterprise access.
- Participation typically involves direct engagement with xAI rather than self-service enrollment.
- API Access Programs:
- Limited API access programs allow technical integration for specific enterprise use cases.
- These programs typically involve direct relationship with xAI and custom implementation support.
- Current API access tends to focus on specific approved use cases rather than general availability.
Developing Enterprise Features:
As xAI expands its enterprise offerings, several key features are developing or anticipated:
- Enterprise Administration:
- Centralized user management for provisioning and revoking access
- Role-based permission systems for appropriate feature access
- Usage monitoring and analytics for deployment oversight
- Centralized billing and subscription management
- Security and Compliance:
- Enhanced security features for enterprise data protection
- Compliance certifications and documentation for regulated industries
- Audit logging and monitoring capabilities
- Data handling controls and governance features
- Integration Capabilities:
- Enterprise-grade API access with appropriate rate limits and SLAs
- Integration tools for connecting with existing enterprise systems
- Documentation and support for custom implementations
- Potential for data connector development to enterprise knowledge sources
- Customization Options:
- Organization-specific knowledge integration capabilities
- Custom deployment options for specific enterprise requirements
- Potential for industry-specific versions or configurations
- Development of enterprise-focused features beyond consumer offerings
Implementation Considerations:
Organizations considering enterprise Grok implementation should evaluate several factors:
- Deployment Models:
- Cloud-based access through xAI's infrastructure (current primary model)
- Potential future on-premises options for high-security requirements
- Hybrid approaches combining cloud access with enterprise data integration
- Scale Requirements:
- User count and anticipated growth trajectory
- Usage volume and patterns across the organization
- Performance requirements for specific use cases
- Geographic distribution of users and associated latency considerations
- Integration Needs:
- Requirements for connecting with existing enterprise systems
- Data sources that would enhance Grok's value for the organization
- Authentication and identity management integration
- Workflow integration with existing business processes
- Security and Compliance:
- Industry-specific regulatory requirements
- Data protection needs and privacy considerations
- Risk management approach for AI implementation
- Governance requirements for AI usage
Enterprise Roadmap Expectations:
While xAI has not published a comprehensive enterprise roadmap, typical industry patterns suggest likely development priorities:
- Near-term Focus:
- Expansion of basic enterprise administration capabilities
- Development of core security features for business use
- Establishment of standard enterprise pricing and licensing models
- Initial API access for basic integration scenarios
- Medium-term Development:
- Enhanced enterprise integration capabilities
- Expanded security and compliance certifications
- More sophisticated administration and governance tools
- Industry-specific solutions for key vertical markets
- Long-term Evolution:
- Advanced customization and knowledge integration
- Comprehensive enterprise ecosystem development
- Specialized enterprise-focused capabilities beyond consumer features
- Deeper integration with enterprise AI strategies
Organizations interested in enterprise Grok implementation should engage directly with xAI to understand current access options and development timelines. As with any rapidly evolving technology, enterprise capabilities will likely expand significantly over time, with early adopters helping shape the development of enterprise-focused features.
API Availability
API access to Grok AI represents a critical component for organizations seeking to integrate Grok's capabilities into their own applications, services, and workflows. The status and roadmap of Grok's API availability is an important consideration for technical implementation planning.
Current API Status:
As of early 2025, Grok API access is in a developing stage, with availability expanding gradually:
- Limited Access Programs:
- Initial API access provided through limited programs rather than general availability
- Selection process typically prioritizing specific use cases and development partners
- Focused on gathering implementation feedback while expanding capabilities
- Documentation Development:
- API documentation expanding as capabilities develop
- Reference materials covering authentication, endpoints, and usage patterns
- Sample code and implementation examples for common scenarios
- Core Functionality Exposure:
- Initial API focus on exposing Grok's core conversational capabilities
- Text generation endpoints for basic query/response patterns
- Access to Grok's distinctive real-time information retrieval features
Anticipated API Capabilities:
Based on industry patterns and xAI's development approach, Grok's API is likely to evolve to include:
- Conversation Management:
- Endpoints for creating and managing conversation sessions
- Context maintenance across multiple API calls
- Conversation history management and retrieval
- Advanced Parameter Control:
- Fine-grained control over response characteristics
- Temperature and sampling strategy adjustments
- Output format and length controls
- Response style customization options
- Multimodal Capabilities:
- Integration of image processing capabilities from Grok-1.5V
- Endpoints for combined text and image inputs
- Multimodal response options (descriptions, analysis, etc.)
- Web Browsing Integration:
- API access to Grok's real-time information retrieval
- Options for controlling web browsing behavior
- Source attribution and citation capabilities
- Enterprise Features:
- Team-based API key management
- Usage monitoring and analytics
- Rate limiting and quota management
- Security and compliance features
Implementation Considerations:
Organizations planning for Grok API integration should consider several technical factors:
- Authentication and Security:
- API authentication using industry-standard approaches (likely OAuth or API keys)
- Secure transmission of requests and responses
- Data handling and privacy considerations
- Key rotation and security management
- Rate Limits and Scaling:
- Understanding of request volume limitations
- Appropriate request throttling and rate limit handling
- Queue management for high-volume implementations
- Failover and redundancy planning
- Response Handling:
- Processing potentially varying response formats
- Handling errors and exceptional conditions
- Implementation of appropriate timeout and retry logic
- Content filtering and validation as needed
- Integration Patterns:
- Synchronous vs. asynchronous integration approaches
- Streaming vs. batch processing considerations
- Caching strategies for appropriate use cases
- Hybrid approaches combining local processing with API calls
API Use Case Examples:
Several common integration patterns are anticipated for Grok's API:
- Customer Support Enhancement:
- Integration with support platforms to provide AI-assisted responses
- Real-time information retrieval for current product/service details
- Contextual assistance based on customer interaction history
- Content Creation Workflows:
- Integration with content management systems
- Draft generation and content enhancement capabilities
- Research assistance leveraging Grok's web browsing features
- Research and Analysis Tools:
- Integration with research platforms and knowledge management systems
- Information synthesis across multiple sources
- Current information retrieval and processing
- Conversational Interfaces:
- Powering chatbots and conversational experiences in applications
- Creating interactive user assistance features
- Enhancing customer engagement through natural language interaction
- Productivity Applications:
- Integration with productivity tools and workplace applications
- Context-aware assistance for complex tasks
- Information retrieval and processing within workflow context
Organizations interested in API access should monitor xAI's announcements regarding API availability and engage directly regarding access programs. As API availability expands, implementation options will likely grow substantially, enabling more sophisticated integration of Grok's capabilities into diverse application contexts and workflows.
Practical Understanding
Interactive Elements
Interacting with Grok AI effectively requires understanding its interface elements and interaction patterns. These interactive elements shape the user experience and influence how successfully users can leverage Grok's capabilities.
Conversation Interface:
Grok's primary interaction occurs through a conversational interface with several key elements:
- Message Input Field:
- Primary text entry area for submitting queries, instructions, or messages
- Typically positioned at the bottom of the conversation view
- May include placeholder text suggesting input types (e.g., "Ask Grok anything...")
- Supports standard text editing functions (cut, copy, paste, etc.)
- Conversation History Display:
- Chronological view of the ongoing conversation
- Visual distinction between user messages and Grok's responses
- Formatting preservation for structured responses (lists, code blocks, etc.)
- Scrollable interface for reviewing earlier exchanges
- Message Status Indicators:
- Visual indicators showing when Grok is processing a query
- Typing or loading animations during response generation
- Delivery confirmation for submitted messages
- Error indicators when issues occur
- Formatting Elements:
- Rich text formatting in Grok's responses (bold, italics, etc.)
- Structured elements like lists, tables, and code blocks
- Links to referenced web sources when using real-time information
- Potential support for inline images in multimodal interactions
Interactive Example: Basic Query-Response:
User: What's the current state of quantum computing?
[Loading indicator appears]
Grok: Quantum computing is currently in a transitional phase between research and practical application. As of early 2025, several key developments characterize the field:
1. **Hardware Advances**: Companies like IBM, Google, and PsiQuantum have made significant progress in increasing qubit counts and reducing error rates. IBM's most advanced quantum processor now exceeds 1,000 qubits, though with substantial error rates.
2. **Quantum Advantage Demonstrations**: Several companies have demonstrated specific problems where quantum computers outperform classical systems, though these remain narrowly defined use cases.
3. **Error Correction Progress**: Significant advances in quantum error correction have occurred, with several groups demonstrating logical qubits with lower error rates than their physical counterparts.
4. **Commercial Access Expansion**: Cloud access to quantum computers has become more widely available, with several companies offering development environments and quantum processing access.
5. **Algorithm Development**: The library of quantum algorithms with potential practical advantage continues to grow, particularly in materials science, cryptography, and optimization problems.
Despite this progress, practical quantum computing with broad commercial impact remains several years away. Most experts expect the next 3-5 years to focus on error correction improvements and specialized applications before more general-purpose quantum computing becomes viable.
Source: Information compiled from recent quantum computing publications and company announcements.
Interaction Patterns:
Several common interaction patterns characterize typical Grok usage:
- Query Refinement:
- Initial query followed by follow-up questions that narrow or expand focus
- Grok maintains context across this refinement process
- Multi-turn Problem Solving:
- Extended exchanges to work through complex problems
- Progressive development of solutions across multiple messages
- Content Iteration:
- Initial content generation followed by revision requests
- Progressive refinement based on feedback
- Research Assistance:
- Leveraging Grok's web browsing for information gathering
- Multiple queries to explore different aspects of a topic
Example:
User: What are the latest developments in sustainable aviation?
Grok: [Provides information from recent web sources]
User: Which companies are leading in electric aircraft development?
Grok: [Searches for and synthesizes information about specific companies]
Example:
User: Write a product announcement for our new AI-powered security tool.
Grok: [Generates initial announcement]
User: That's good, but make it more technical for our developer audience.
Grok: [Revises content to be more technical]
Example:
User: I need to design a database schema for a library management system.
Grok: [Asks clarifying questions about requirements]
User: [Provides specific requirements]
Grok: [Suggests initial schema design]
User: What if we need to track multiple copies of the same book?
Grok: [Refines design to accommodate this requirement]
Example:
User: Tell me about neural networks.
Grok: [Provides overview of neural networks]
User: What about specifically recurrent neural networks?
Grok: [Focuses on recurrent neural networks while maintaining context]
Interactive Example: Web Browsing Capability:
User: What were the major outcomes of the climate conference that happened last month?
[Loading indicator shows web browsing activity]
Grok: Based on the most recent international climate conference from last month (April 2025), here are the major outcomes:
1. **Enhanced Emissions Targets**: 28 countries submitted new, more ambitious emissions reduction targets, with several major economies pledging carbon neutrality by 2045 instead of previous 2050 commitments.
2. **Climate Finance Package**: A new $100 billion annual climate finance package was established to support developing nations, with specific allocation mechanisms and transparency requirements.
3. **Methane Reduction Agreement**: A binding agreement to reduce methane emissions by 50% by 2030 was signed by 43 countries, including several major oil and gas producers.
4. **Loss and Damage Fund Implementation**: The operational framework for the Loss and Damage Fund was finalized, with initial capitalization of $30 billion and clear disbursement criteria.
5. **Renewable Energy Coalition**: A new international coalition committed to achieving 70% renewable electricity generation by 2035, with technology sharing agreements and implementation roadmaps.
The conference was generally considered more productive than previous years, with concrete commitments and financing mechanisms receiving praise from environmental organizations, though some critics noted implementation timelines remain too conservative given current warming trajectories.
Sources: UN Climate Change press releases, Reuters coverage of the conference, and Climate Action Network analysis published in the past month.
These interactive elements and patterns demonstrate how users engage with Grok across different use cases, from simple queries to complex problem-solving and research tasks. Understanding these interaction patterns helps users leverage Grok's capabilities more effectively and develop appropriate expectations for different types of exchanges.
Command Guide
Effectively interacting with Grok AI requires understanding various command strategies and input approaches that help users achieve optimal results. This command guide provides practical instruction on how to formulate requests to maximize Grok's utility across different use cases.
Basic Query Formulation:
The foundation of effective Grok interaction is clear query formulation:
- Direct Questions:
- Structure: Simple interrogative sentences ending with question marks
- Best for: Factual information, definitions, explanations
- Example: "What is quantum entanglement?"
- Tip: Be specific about what information you're seeking
- Imperative Commands:
- Structure: Directive statements beginning with verbs
- Best for: Requesting specific outputs or actions
- Example: "Explain the process of photosynthesis in simple terms."
- Tip: Clearly state the action you want Grok to perform
- Open-ended Prompts:
- Structure: Broader requests that invite exploration
- Best for: Creative tasks, brainstorming, exploration of topics
- Example: "Share some perspectives on how AI might impact healthcare over the next decade."
- Tip: Indicate the breadth or depth you're looking for
Specifying Output Format:
You can control how Grok presents information by specifying preferred formats:
- Structured Outputs:
- Request lists: "List five strategies for improving cybersecurity in remote work environments."
- Request tables: "Create a comparison table of the top three cloud storage providers."
- Request step-by-step procedures: "Explain how to implement two-factor authentication in step-by-step instructions."
- Length Control:
- Request brevity: "Give me a concise explanation of blockchain technology."
- Request detail: "Provide a comprehensive overview of machine learning algorithms."
- Specify word count: "Write a 300-word summary of the current state of renewable energy."
- Style Guidance:
- Specify tone: "Explain quantum computing in a conversational style."
- Specify audience: "Describe neural networks for a high school student."
- Specify formality: "Write a formal analysis of recent cybersecurity trends."
Task-Specific Commands:
Different tasks benefit from specialized command approaches:
- Information Retrieval:
- Current events: "What are the latest developments in fusion energy research?"
- Comparative information: "How do OLED and QLED display technologies compare?"
- Statistical information: "What are the current renewable energy adoption rates globally?"
- Tip: For current information, explicitly mention recency to trigger web browsing
- Problem-Solving:
- State problem clearly: "I need to design a database schema for tracking inventory across multiple locations."
- Provide context: "For a small business with approximately 500 products and 3 warehouse locations..."
- Specify constraints: "The solution needs to be implementable in MySQL and support mobile access."
- Ask for options: "What are different approaches to solving this, with their pros and cons?"
- Content Creation:
- Specify purpose: "Write a blog post introduction about cybersecurity for small businesses."
- Specify audience: "The target audience is non-technical business owners."
- Specify tone: "Use an authoritative but accessible tone."
- Specify length: "Approximately 200 words."
- Provide examples (optional): "I like introductions that start with a compelling statistic."
- Code Generation:
- Specify language: "Write a Python function that..."
- Specify requirements: "The function should take a list of strings and return..."
- Specify constraints: "Optimize for readability over performance."
- Request comments: "Include comments explaining the approach."
Multi-turn Interaction Strategies:
Effective use of Grok often involves multi-message exchanges:
- Progressive Refinement:
- Start broad: "Tell me about machine learning."
- Narrow focus: "Focus specifically on reinforcement learning applications."
- Request specific details: "Explain how Q-learning works in this context."
- Tip: Build on previous exchanges rather than starting fresh each time
- Feedback and Iteration:
- Initial request: "Draft an email to a client about project delays."
- Provide feedback: "Make it more concise and emphasize the new timeline."
- Final refinement: "Add a specific request for their acknowledgment."
- Tip: Be specific about what aspects need modification
- Exploration Sequences:
- Start with overview: "Explain the concept of zero trust security."
- Request examples: "Provide some real-world implementation examples."
- Ask for implications: "What are the challenges of transitioning to this model?"
- Request recommendations: "What steps should a mid-sized company take to begin implementation?"
Advanced Command Techniques:
Several advanced techniques can enhance Grok's responses for specific needs:
- Role Assignment:
- Structure: "As a [role], [task]"
- Example: "As a cybersecurity expert, explain the implications of the recent changes to data protection regulations."
- Benefit: Helps frame response from a particular perspective or expertise area
- Format Templates:
- Structure: "Respond using the following format: [specify sections]"
- Example: "Analyze this investment opportunity using the following format: Summary, Potential Benefits, Risks, Timeline Considerations, Recommendation."
- Benefit: Creates consistent, well-organized responses
- Explicit Context Provision:
- Structure: "Given that [context], [question/task]"
- Example: "Given that we're a B2B SaaS company with approximately 50 employees, what cybersecurity measures should we prioritize?"
- Benefit: Ensures relevant context is considered in the response
- Reasoning Prompts:
- Structure: "Think through [problem] step by step."
- Example: "Think through how to architect a secure cloud-based document management system step by step."
- Benefit: Encourages more thorough analytical responses
Web Browsing-Specific Commands:
To effectively leverage Grok's real-time information access:
- Explicitly Request Current Information:
- Structure: "What is the current state of [topic]?" or "What are the latest developments in [field]?"
- Example: "What are the latest advancements in quantum computing hardware?"
- Benefit: Clearly signals that recent information is needed
- Request Source Information:
- Structure: "Include sources for this information."
- Example: "Explain the current consensus on climate change mitigation strategies and include your sources."
- Benefit: Provides attribution for fact verification
- Comparative Current Analysis:
- Structure: "Compare the current approaches to [topic]."
- Example: "Compare the current approaches major companies are taking to implement AI ethics frameworks."
- Benefit: Triggers research across multiple current sources
These command strategies provide a practical framework for effective interaction with Grok across various use cases. By understanding and applying these approaches, users can more successfully leverage Grok's capabilities for information retrieval, problem-solving, content creation, and other applications while receiving more relevant, well-structured responses.
Use Case Examples
To illustrate Grok AI's practical applications, here are several detailed use case examples that demonstrate how different types of users can effectively leverage Grok's capabilities to address specific needs.
1. Research Assistant for Technology Monitoring
Scenario: A product manager needs to stay current on developments in AI hardware acceleration technologies to inform roadmap decisions.
Implementation Approach:
- Regular queries about recent developments in AI accelerator technology
- Requests for comparisons between competing approaches
- Questions about industry adoption trends and performance benchmarks
- Synthesis of information across multiple sources and timeframes
Example Interaction:
User: What are the most significant developments in AI hardware acceleration over the past three months?
Grok: [After web search] Over the past three months (February-April 2025), several significant developments have emerged in AI hardware acceleration:
1. **NVIDIA Blackwell Architecture Launch**: NVIDIA fully launched their Blackwell architecture GPUs, with benchmarks showing 2-4x performance improvements for large language model training compared to Hopper architecture, while claiming 25% better energy efficiency.
2. **Google TPU v5 Availability**: Google has expanded access to their TPU v5 systems, moving beyond internal use to broader cloud availability. Early benchmarks show particular strength in transformer model inference tasks.
3. **Apple Neural Engine Expansion**: Apple announced their next-generation Neural Engine with significant architectural changes to better support on-device large language model deployment, expected in devices later this year.
4. **Cerebras CS-3 System**: Cerebras unveiled their CS-3 system with an enhanced wafer-scale engine containing 4 trillion transistors, specifically optimized for sparse model training.
5. **Open AI Acceleration Standards**: A new industry consortium including AMD, Intel, and several cloud providers announced work on open standards for AI acceleration interoperability, aiming to reduce vendor lock-in.
The primary trend across these developments is the growing specialization for different AI workloads, with architectures increasingly optimized for specific model types rather than general-purpose acceleration.
Sources: Recent announcements from manufacturer websites, analysis from AnandTech's coverage, and performance benchmarks published by MLCommons.
Value Delivery:
- Saves hours of manual research across multiple sources
- Provides synthesis of developments rather than just isolated facts
- Offers context and implications beyond raw information
- Maintains awareness of rapidly evolving technology landscape
2. Cybersecurity Documentation and Process Development
Scenario: A security manager needs to develop comprehensive incident response procedures for different types of security events.
Implementation Approach:
- Requesting documentation templates for different incident types
- Iterative refinement based on organization-specific requirements
- Generation of procedural workflows and responsibility matrices
- Development of communication templates for different stakeholders
Example Interaction:
User: Create an incident response procedure template for ransomware attacks.
Grok: Here's an incident response procedure template for ransomware attacks:
# RANSOMWARE ATTACK INCIDENT RESPONSE PROCEDURE
## 1. INCIDENT IDENTIFICATION AND INITIAL RESPONSE
- **Detection Methods**: System alerts, user reports, security monitoring tools
- **Initial Assessment Tasks**:
* Confirm ransomware indicators (encrypted files, ransom notes)
* Document observable symptoms and affected systems
* Identify initial infection vector if immediately apparent
- **Immediate Containment Actions**:
* Isolate affected systems by disconnecting from network
* Disable affected user accounts
* Block relevant IP addresses/domains at firewall/proxy
* Consider broader network segmentation based on spread assessment
## 2. INCIDENT DECLARATION AND ESCALATION
- **Escalation Criteria**: [Customize based on organization size/threshold]
- **Notification Chain**:
* Incident Response Team Lead
* CISO/Security Director
* IT Infrastructure Team
* Legal Department
* Executive Management
- **External Notification Assessment**:
* Law enforcement (FBI/CISA)
* Cyber insurance provider
* External incident response partners
## 3. CONTAINMENT AND ERADICATION
- **Comprehensive Impact Assessment**:
* Identify all affected systems, accounts, and data
* Determine ransomware variant using available indicators
* Assess lateral movement and potential persistence mechanisms
- **Enhanced Containment Measures**:
* Implement additional network segregation
* Block command-and-control communications
* Reset credentials for all potentially compromised accounts
- **Evidence Preservation**:
* Create forensic images of affected systems
* Preserve logs from security tools, network devices, and servers
* Document all observed IoCs (file hashes, IP addresses, domains)
## 4. RECOVERY PLANNING
- **Recovery Strategy Decision Points**:
* Restore from clean backups vs. other options
* Required system rebuild procedures
* Prioritization framework for system restoration
- **Pre-Recovery Security Measures**:
* Address initial infection vector
* Implement additional security controls
* Verify backup integrity before restoration
- **Recovery Execution**:
* Systematic restoration according to priority list
* Verification testing before returning to production
* Enhanced monitoring during recovery process
## 5. POST-INCIDENT ACTIVITIES
- **Comprehensive Analysis**:
* Full attack timeline reconstruction
* Root cause determination
* Effectiveness assessment of security controls
- **Documentation Requirements**:
* Detailed incident report
* Evidence handling chain of custody
* Remediation actions taken
- **Process Improvement**:
* Security control enhancement recommendations
* Procedure update requirements
* Training and awareness needs
## 6. COMMUNICATION PLAN
- **Internal Communications**:
* Executive briefing templates
* Staff notification guidelines
* Status update cadence and channels
- **External Communications**:
* Customer/client notification criteria and templates
* Media response guidelines (if applicable)
* Regulatory reporting requirements and deadlines
## APPENDICES
- Ransomware Identification Checklist
- Key Contact Information
- Evidence Collection Procedures
- Relevant Regulatory Requirements
User: This is good. Can you expand the Recovery Planning section with more specific guidance on determining whether to pay the ransom?
Grok: [Provides expanded recovery planning section with ransomware payment decision framework]
Value Delivery:
- Accelerates documentation development process
- Ensures comprehensive coverage of critical procedure elements
- Provides structured framework that can be customized
- Enables iterative refinement through conversation
3. Software Architecture Planning Assistant
Scenario: A software developer needs to design a scalable microservices architecture for a new application with specific performance requirements.
Implementation Approach:
- Discussion of architectural requirements and constraints
- Generation of candidate architecture diagrams and descriptions
- Exploration of technology stack options with pros/cons
- Analysis of potential scaling challenges and solutions
Example Interaction:
User: I need to design a microservices architecture for an e-commerce platform that needs to handle 10,000 concurrent users and seasonal traffic spikes up to 5x normal volume. The platform needs to include product catalog, user accounts, shopping cart, order processing, and payment processing. What architecture would you recommend?
Grok: [Provides detailed architectural recommendation with services breakdown, technology stack options, and scaling considerations]
User: For the product catalog service, how would you handle the database design to support efficient searching with faceted filtering?
Grok: [Provides specific database design recommendations for the catalog service with query optimization approaches]
User: What monitoring and observability solutions would work best with this architecture?
Grok: [Recommends comprehensive monitoring approach with specific tools and implementation considerations]
Value Delivery:
- Provides structured approach to architectural planning
- Offers perspective on industry best practices and patterns
- Helps identify potential issues before implementation
- Serves as a "thought partner" for technical decision-making
4. Market Analysis and Competitive Intelligence
Scenario: A business strategist needs to understand market trends and competitive positioning in the cybersecurity SaaS sector.
Implementation Approach:
- Queries about current market size and growth projections
- Requests for competitive landscape analysis
- Questions about recent funding activity and acquisitions
- Analysis of emerging technology trends affecting the market
Example Interaction:
User: Analyze the current competitive landscape for endpoint detection and response (EDR) solutions, focusing on cloud-native offerings.
Grok: [After web search] Here's an analysis of the current competitive landscape for cloud-native Endpoint Detection and Response (EDR) solutions as of May 2025:
## Market Overview
The cloud-native EDR market continues to grow rapidly, with recent analyst reports estimating a market size of approximately $4.2 billion in 2025, projected to reach $7.8 billion by 2028. This represents a CAGR of around 23%, driven by increasing sophisticated threats and the continued shift to remote/hybrid work environments.
## Key Competitive Segments
### Enterprise-Focused Leaders
* **CrowdStrike Falcon**: Maintains market leadership with approximately 24% market share. Recent platform expansions include enhanced identity protection and cloud workload security. Their Q1 2025 earnings showed 42% YoY growth.
* **Microsoft Defender for Endpoint**: Leveraging their broader ecosystem integration, Microsoft has grown to approximately 18% market share. Their recent E5 security suite bundling strategy has accelerated adoption.
* **SentinelOne Singularity**: Continuing strong growth at 39% YoY, with current market share around 16%. Their recent acquisition of [Company X] expanded their data analytics capabilities.
### Cloud-Native Specialists
* **Cybereason XDR**: Focused on behavioral analysis and automated response, with approximately 8% market share. Recent funding round of $150M positions them for expansion.
* **VMware Carbon Black Cloud**: Leveraging VMware's cloud infrastructure presence, maintaining around 10% market share with strong position in regulated industries.
* **Elastic Security**: Growing from their observability roots, currently at approximately 5% market share but showing the fastest growth rate among established vendors.
### Emerging Disruptors
* **Uptycs**: Gaining traction with their unified CNAPP/EDR approach, especially in cloud-first organizations.
* **Hunters XDR**: Their automated investigation capabilities and recent Series C funding of $200M have accelerated enterprise adoption.
* **[Several other emerging players with distinctive approaches]**
## Current Competitive Differentiation Factors
1. **Extended XDR Integration**: The ability to correlate endpoint data with other security telemetry is now table stakes
2. **Cloud Workload Protection**: Expanded coverage beyond traditional endpoints to cloud infrastructure
3. **Identity Security Integration**: Merging endpoint and identity signals for enhanced protection
4. **Automation Sophistication**: Advanced automated response capabilities requiring minimal human intervention
5. **Time-to-Value**: Deployment speed and immediate protection capabilities
## Recent Market Developments
* Continued consolidation with [Company A] acquiring [Company B] in March 2025
* Shift toward consumption-based pricing models rather than per-endpoint licensing
* Increasing regulatory requirements driving advanced logging and compliance reporting features
* Emergence of specialized solutions for OT/IoT endpoint protection
Sources: Recent market reports from Gartner and Forrester, company earnings calls from the past quarter, and industry analysis published in the cybersecurity trade press.
Value Delivery:
- Provides synthesized market intelligence from multiple sources
- Offers current information through web browsing capability
- Delivers structured analysis rather than just raw information
- Saves significant manual research time
5. Technical Documentation Development
Scenario: A product team needs to create comprehensive API documentation for a new developer platform.
Implementation Approach:
- Generation of documentation structure and templates
- Development of clear endpoint descriptions and parameters
- Creation of example requests and responses
- Production of implementation tutorials and best practices
Example Interaction:
User: I need to create documentation for our new authentication API. The API has endpoints for user registration, login, token refresh, password reset, and multi-factor authentication management. Can you create a documentation template?
Grok: [Provides comprehensive API documentation template with all requested endpoints]
User: For the user registration endpoint, here are the actual parameters: [provides parameter details]
Grok: [Updates documentation with specific parameter information and generates example requests/responses]
User: Can you add a section on security best practices for implementing this API?
Grok: [Adds detailed security best practices section with implementation recommendations]
Value Delivery:
- Accelerates technical documentation development
- Ensures comprehensive coverage of important elements
- Promotes documentation consistency and clarity
- Reduces technical writing burden on development teams
These detailed use case examples illustrate how Grok can be practically applied across different business functions and technical needs. The examples demonstrate not just the types of tasks Grok can assist with, but also the interaction patterns and implementation approaches that lead to effective utilization of its capabilities in real-world scenarios.
Expert Tips
Based on my experience implementing AI solutions across different organizational contexts, I've developed several expert recommendations for getting the most from Grok AI. These tips focus on maximizing Grok's effectiveness while working within its capabilities and limitations.
Optimizing Query Formulation:
- Specify Information Currency Needs
- When current information is essential, explicitly indicate this in your query.
- Example: "What are the latest developments in quantum computing?" rather than just "Tell me about quantum computing."
- This approach helps trigger Grok's web browsing capability when appropriate.
- Frame Complex Queries as Tasks
- For complex needs, frame your query as a task with clear deliverables rather than an open question.
- Instead of "What should our cybersecurity strategy include?" try "Create a framework for developing a cybersecurity strategy for a mid-sized B2B SaaS company."
- This task-oriented approach typically yields more structured, comprehensive responses.
- Provide Context Efficiently
- Front-load essential context but avoid unnecessary detail that consumes context window space.
- Example: "For a financial services company with 500 employees and regulatory compliance requirements, recommend an approach to..."
- This balanced context provides critical information without overwhelming the query.
- Use Question Sequencing
- Break complex information needs into strategic sequences of related questions.
- Start with broader questions before drilling down into specifics.
- This builds context progressively while maintaining focus at each step.
Technical Implementation Strategies:
- Leverage Complementary Knowledge Bases
- For organization-specific information, provide essential facts in your queries rather than expecting Grok to know them.
- Consider developing standard context snippets for common query types in your organization.
- This approach bridges the gap between Grok's general knowledge and your specific environment.
- Implement Verification Workflows
- Design workflows with appropriate verification steps based on the criticality of the task.
- For high-stakes outputs, implement multiple review checkpoints.
- Develop clear guidelines for when human verification is required versus optional.
- Create Prompt Libraries
- Develop and maintain libraries of effective prompts for common use cases in your organization.
- Document what works well for specific needs to enable knowledge sharing.
- Iterate and refine these prompts based on results and feedback.
- Establish Context Management Practices
- For extended sessions, periodically summarize the conversation to refresh context.
- When approaching context window limits, consider starting new conversations with summarized context.
- This approach helps manage Grok's finite context capacity more effectively.
Domain-Specific Optimization:
- Cybersecurity Applications
- For threat analysis, provide specific indicators and context rather than vague descriptions.
- When discussing security implementations, specify your technology stack and constraints.
- Frame security questions in terms of risk management and trade-offs rather than seeking absolute answers.
- Software Development Assistance
- Provide language version, framework details, and specific requirements when requesting code.
- Ask for explanations alongside code to ensure understanding.
- Break complex development tasks into logical components rather than requesting entire systems at once.
- Business Strategy Support
- Frame analysis requests with specific decision criteria or evaluation frameworks.
- Specify the strategic context, including key constraints and objectives.
- Request multiple perspectives or approaches rather than single solutions.
Maximizing Information Quality:
- Source Evaluation Requests
- When using Grok's web browsing capability, ask it to comment on the quality of sources.
- Request information about source recency, authority, and potential limitations.
- This promotes transparency about information quality and reliability.
- Multi-angle Inquiry
- Approach important topics from multiple angles with different queries.
- Compare responses to identify consistency and potential knowledge gaps.
- This cross-referencing approach improves information confidence.
- Explicit Uncertainty Requests
- Ask Grok to explicitly identify aspects of responses with higher uncertainty.
- Example: "Please note any parts of this analysis where you have lower confidence."
- This promotes appropriate calibration of confidence in the information.
Productivity Enhancement:
- Template Generation
- Use Grok to create templates for recurring document types rather than generating each from scratch.
- Develop and refine these templates over time for consistent quality.
- This approach combines Grok's creative capabilities with efficient reuse.
- Incremental Review Cycles
- For complex content development, use multiple shorter review cycles rather than single comprehensive reviews.
- Focus each cycle on specific aspects (structure, technical accuracy, tone, etc.).
- This iterative approach typically yields better results than attempting perfect outputs in one step.
- Hybrid Workflows
- Design workflows that combine Grok's strengths with human expertise.
- Use Grok for initial drafts, research assistance, or option generation while reserving critical evaluation and decision-making for humans.
- These hybrid approaches typically deliver better results than either fully manual or fully AI-driven processes.
Implementation Philosophy:
- Start With Bounded Use Cases
- Begin Grok implementation with clearly defined, limited-scope use cases.
- Establish success metrics and evaluation approaches before expanding.
- Use these initial implementations to develop organizational best practices.
- Develop AI Collaboration Skills
- Invest in developing employee skills for effective AI collaboration.
- Focus training on prompt engineering, output evaluation, and appropriate task selection.
- Recognize that effective AI utilization is an evolving skill set requiring ongoing development.
- Establish Clear Boundaries
- Develop explicit guidelines for appropriate and inappropriate Grok use cases in your organization.
- Create clear policies regarding sensitive information sharing.
- Establish responsibility frameworks for AI-assisted outputs.
These expert tips represent practical wisdom gained from implementing AI solutions across various contexts. By applying these strategies, organizations can more effectively leverage Grok's capabilities while appropriately managing its limitations, ultimately delivering greater value through thoughtful implementation approaches.
Deepak's Analysis
Expert Perspective
As a technology entrepreneur who has built multiple AI-powered solutions in the cybersecurity and identity management space, I see Grok AI as representing an important evolution in the large language model landscape. Its approach to addressing the knowledge cutoff limitation through integrated web browsing capability reflects a necessary direction for making these models more practically useful in rapidly changing domains like technology and cybersecurity.
From my perspective, what makes Grok particularly interesting is not just this technical capability, but the philosophical approach it represents. By designing a model that more aggressively seeks current information rather than relying primarily on its training data, xAI has addressed one of the most significant practical limitations of early LLMs. This approach aligns well with the needs of technology professionals who require both deep foundational knowledge and awareness of current developments.
Having built LoginRadius to serve millions of users with digital identity solutions, I appreciate the technical challenges involved in creating systems that balance sophisticated capabilities with practical utility. Grok appears to strike this balance in several ways - maintaining the broad knowledge representation of large language models while adding real-time information access, and combining conversational engagement with substantive information delivery.
The "rebellious" personality that distinguishes Grok represents an interesting product differentiation strategy in an increasingly crowded AI assistant market. While this characteristic sometimes receives more attention than its substantive impact warrants, it does create a distinctive user experience that some users find more engaging. From a product strategy perspective, this differentiation makes sense, though the long-term value will ultimately depend more on capability execution than personality positioning.
What I find most promising about Grok's fundamental design is its potential to evolve into a more comprehensive intelligence augmentation tool rather than just an information retrieval system. The combination of parametric knowledge with real-time information access creates possibilities for more sophisticated synthesis and analysis than either approach alone would allow. This aligns with my own work at GrackerAI, where we're focused on augmenting human intelligence rather than simply automating tasks.
At the same time, I recognize that Grok's current implementation has limitations that should inform deployment decisions. Its reasoning capabilities, while impressive in many contexts, still exhibit the fundamental constraints common to all current LLMs. Its knowledge integration processes, combining internal and external information, continue to evolve in sophistication but require appropriate verification for critical applications. These limitations don't diminish Grok's utility but rather define how it can be most effectively leveraged.
Security Implications
From a cybersecurity perspective, Grok AI presents both opportunities and considerations that should inform implementation decisions.
On the opportunity side, Grok's real-time information access capability has particular value for security applications that require current awareness. The cybersecurity landscape evolves rapidly, with new vulnerabilities, attack techniques, and mitigation strategies emerging constantly. Traditional LLMs with fixed knowledge cutoffs quickly become outdated for specific security information, even as their fundamental security principles remain valid. Grok's ability to access current vulnerability disclosures, security advisories, and threat intelligence provides significant value for security professionals seeking to maintain awareness.
Additionally, Grok can serve as an effective force multiplier for security teams, particularly in organizations with limited specialized resources. It can help analyze security events, generate initial documentation, and provide context on emerging threats - supporting security professionals rather than replacing them. This augmentation approach aligns with how I've seen AI most effectively deployed in security contexts.
However, several security considerations should guide Grok implementation:
First, information security must be carefully considered when using any external AI system. Organizations must develop clear guidelines about what types of information can be shared with Grok, particularly regarding sensitive security details, network architecture, and potential vulnerabilities. While xAI undoubtedly implements appropriate security controls, the fundamental principle of need-to-know should still apply to AI interactions.
Second, the quality of security information retrieved through web browsing varies significantly. Security professionals using Grok should maintain a critical perspective on source credibility and information currency, particularly for emerging threats where initial reports often contain inaccuracies. Verification processes remain essential for security-critical information.
Third, Grok's reasoning limitations become particularly significant in security contexts where subtle interactions between system components can create unexpected vulnerabilities. Complex attack chains, sophisticated threat scenarios, and security architecture decisions often require deeper contextual understanding than current AI systems can reliably provide without human oversight.
From an implementation perspective, I recommend a tiered approach to Grok utilization in security contexts:
- Tier 1 (Low Risk): Information gathering, initial research, documentation assistance
- Tier 2 (Medium Risk): Preliminary analysis, option generation, pattern identification
- Tier 3 (High Risk): Final decision-making, critical security architecture, vulnerability assessment
This tiered approach allows security teams to leverage Grok's capabilities while implementing appropriate verification processes based on the criticality of the specific task.
Strategic Value
For technical decision-makers evaluating Grok AI, understanding its strategic value requires looking beyond feature comparisons to consider how it might enhance organizational capabilities and workflows.
The primary strategic value of Grok lies in its ability to accelerate information processes across the enterprise. By combining broad knowledge with real-time information access in a conversational interface, Grok can significantly reduce the time required for research, initial content creation, and information synthesis. This time efficiency translates directly to productivity enhancements, particularly for knowledge workers who spend substantial time gathering and processing information.
From my experience building and scaling technology companies, I've observed that AI implementations deliver the greatest value when they enhance human capabilities rather than simply replacing tasks. Grok's design philosophy aligns with this approach - it serves as an intelligence augmentation tool that can handle initial information processing while allowing humans to focus on critical thinking, creativity, and decision-making. This collaborative human-AI approach typically delivers better results than either could achieve independently.
For organizations implementing Grok, several strategic considerations should inform the approach:
- Capability Enhancement vs. Cost Reduction The most successful AI implementations typically focus first on enhancing capabilities rather than reducing costs. Organizations should identify where Grok can help employees deliver better outcomes - more comprehensive research, more informed decisions, more creative solutions - rather than focusing primarily on headcount reduction. This capability-first approach typically generates greater long-term value.
- Knowledge Democratization Grok can help democratize specialized knowledge across the organization, making expertise more accessible beyond formal organizational boundaries. This can accelerate innovation and problem-solving by allowing more employees to access and apply specialized knowledge that would previously have been bottlenecked by expert availability.
- Workflow Integration The strategic value of Grok depends significantly on how effectively it integrates into existing workflows rather than creating parallel processes. Organizations should design thoughtful integration points where Grok enhances rather than disrupts established workflows, creating adoption paths with minimal friction.
- Capability Development Effective AI utilization represents a new organizational capability that requires intentional development. Organizations should invest in developing employee skills for effective AI collaboration, establishing best practices, and creating feedback loops for continuous improvement in AI utilization.
- Strategic Vs. Tactical Implementation Organizations will derive the greatest value by implementing Grok strategically rather than tactically. This means identifying systematic organizational needs where AI assistance can create compounding value, rather than isolated use cases. Examples include knowledge management systems, employee onboarding processes, or centralized research functions.
For technical decision-makers specifically, understanding Grok's fundamentals provides the foundation for effective implementation planning. By recognizing both the capabilities and limitations of Grok's architecture, knowledge access mechanisms, and reasoning abilities, leaders can develop appropriate governance frameworks, integration approaches, and verification processes that maximize value while managing risks.
The organizations that will derive the greatest strategic value from Grok are those that approach implementation as a sociotechnical challenge rather than merely a technical one - recognizing that effective AI utilization requires alignment of technology, processes, skills, and culture. This holistic approach to implementation typically delivers more sustainable value than treating AI adoption as primarily a technical deployment.
Resources and Next Steps
Related Content Links
To further explore Grok AI and related topics, the following resources provide additional depth in key areas:
Grok AI Technical Resources:
- Grok AI Technical Analysis - Detailed examination of Grok's architecture, performance benchmarks, and engineering insights
- Grok AI vs. Competitors - Comprehensive comparison with GPT-4, Claude, and other leading language models
- Grok AI Use Cases - Practical applications across business functions and technical domains
Implementation Guidance:
- Grok AI Implementation Guide - Detailed approaches for enterprise deployment and integration
- Grok AI Security Considerations - Comprehensive analysis of security implications and risk management
- Future of Grok AI - Analysis of expected developments and strategic preparation
Complementary AI Resources:
- AI Implementation Framework - Comprehensive methodology for effective enterprise AI deployment
- Prompt Engineering Best Practices - Advanced techniques for effective AI interaction
- AI Governance for Enterprises - Frameworks for responsible AI implementation
Cybersecurity Integration:
- AI in Cybersecurity Operations - Strategic approaches to integrating AI into security workflows
- Threat Intelligence Automation - Leveraging AI for enhanced threat awareness
- Security Documentation Automation - Streamlining security documentation with AI assistance
Deepak's AI Perspectives:
- AI Strategy for B2B SaaS Companies - Strategic framework for AI implementation in SaaS contexts
- Balancing AI Innovation and Security - Approaches to responsible AI advancement
- Future of AI in Enterprise Operations - Long-term vision for AI integration
External References
For those seeking additional perspectives on Grok AI and related technologies, these external resources provide valuable context and insights:
Official Resources:
- xAI Official Website - Primary source for official Grok information and updates
- X (Twitter) Premium+ Information - Details on accessing Grok through X Premium+ subscriptions
Technical Analyses:
- Anthropic's State of AI Report - Comprehensive analysis of AI model capabilities and trends
- Stanford HAI Artificial Intelligence Index - Academic perspective on AI advancement and impacts
- Hugging Face Model Comparison - Community-driven model benchmarking and comparison
Industry Perspectives:
- Gartner AI Hype Cycle - Analysis of AI technology maturity and adoption
- MIT Technology Review - In-depth coverage of AI developments and implications
- IEEE Spectrum AI Reports - Technical perspective on AI advancement
Implementation Guidance:
- AI Business Case Framework (Harvard Business Review) - Approaches to evaluating AI business value
- NIST AI Risk Management Framework - Standards-based approach to AI risk assessment
- O'Reilly AI Implementation Patterns - Practical patterns for effective AI deployment
These external resources complement the information provided in this guide, offering additional perspectives and specialized insights on Grok AI and the broader AI landscape.
Downloadable Resource: Grok AI Technical Specifications
To support your evaluation and implementation planning, we've created a comprehensive technical specifications sheet for Grok AI. This downloadable resource provides a detailed reference for Grok's capabilities, limitations, and implementation requirements.
Download Grok AI Technical Specifications (PDF)
This reference document includes:
Technical Architecture Details:
- Comprehensive architectural diagram
- Component descriptions and relationships
- Processing workflow illustrations
- Interface specifications and protocols
Capability Parameters:
- Detailed capability benchmarks and performance metrics
- Context window specifications and limitations
- Web browsing implementation details
- Query processing and response generation specifications
Implementation Requirements:
- System requirements for different deployment scenarios
- Integration approach recommendations
- Performance considerations and optimization guidance
- Security implementation recommendations
Comparison Reference:
- Detailed feature comparison with leading alternatives
- Performance benchmark comparisons across key metrics
- Use case suitability matrix across different needs
- Integration capability comparison
This technical specifications sheet serves as a valuable reference for technical decision-makers evaluating Grok implementation, providing the detailed information necessary for thorough assessment and planning.
Engagement CTA
Discuss Your Grok AI Implementation
I'd be happy to discuss how your organization can effectively implement Grok AI to address specific business challenges. With experience building and scaling AI-powered solutions across cybersecurity, digital identity, and B2B SaaS contexts, I can provide practical guidance for your implementation journey.
Schedule a Consultation to Discuss:
- Evaluating Grok's fit for your specific use cases
- Developing effective implementation strategies
- Establishing appropriate governance frameworks
- Creating hybrid human-AI workflows
- Balancing innovation with security considerations
Schedule a 30-Minute Consultation →
Share Your Implementation Experience
If you've already begun implementing Grok in your organization, I'd love to hear about your experience. Sharing implementation insights helps advance our collective understanding of effective AI utilization approaches.
Share Your Grok Implementation Story →
Stay Updated on Grok Developments
The Grok AI landscape continues to evolve rapidly. Subscribe to receive updates on new capabilities, implementation best practices, and strategic insights:
Subscribe to Grok AI Updates →
Your journey with Grok AI represents an opportunity to enhance your organization's capabilities through thoughtful implementation of advanced AI technology. I'm committed to supporting that journey with practical, experience-based guidance that balances innovation with responsible implementation.
