AI-Powered Cybersecurity: How Artificial Intelligence is Transforming the OSI Model
Explore the OSI model's 7 layers, their vulnerabilities in the cybersecurity landscape, and how AI is revolutionizing defense strategies for each layer.
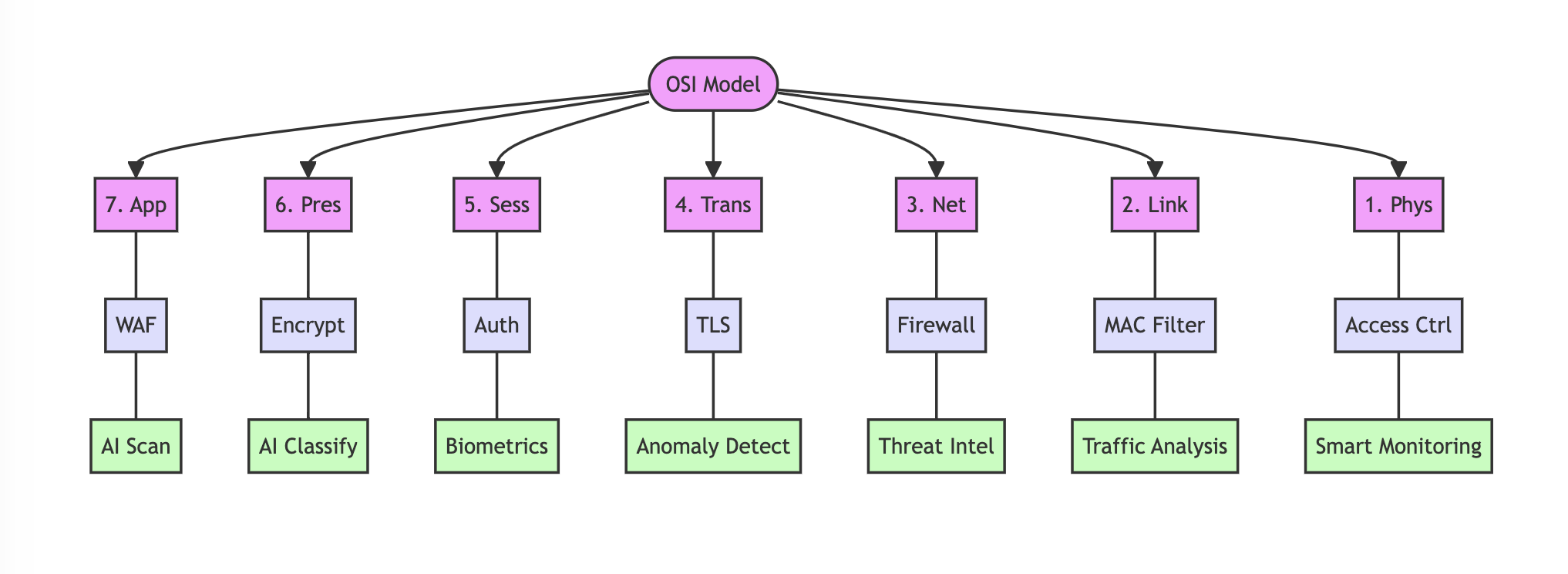
In today's interconnected digital landscape, businesses face an ever-evolving array of cybersecurity threats. To effectively protect their assets, data, and reputation, companies must implement robust security measures at every layer of their network infrastructure.
This article provides a deep dive into each layer of the OSI (Open Systems Interconnection) model, exploring the specific security challenges, protection strategies, key players in the security industry, and emerging innovations for each layer.
| OSI Layer | Layer Name | Cybersecurity Measures |
|---|---|---|
| 7 | Application | - Web Application Firewalls (WAF) - Input validation - Encryption (HTTPS, SSL/TLS) - Authentication and authorization - Regular security updates and patches |
| 6 | Presentation | - Data encryption - Digital signatures - Format preserving encryption |
| 5 | Session | - Session management - Secure session handling - Time-outs for inactive sessions |
| 4 | Transport | - Transport Layer Security (TLS) - Secure Socket Layer (SSL) - Port security |
| 3 | Network | - Firewalls - Intrusion Detection/Prevention Systems (IDS/IPS) - Virtual Private Networks (VPN) - Access Control Lists (ACL) |
| 2 | Data Link | - MAC address filtering - Port security on switches - IEEE 802.1X for port-based access control |
| 1 | Physical | - Physical access controls - Cable protection - Biometric access systems - Surveillance systems |
1. Physical Layer Security
The Physical Layer is the foundation of network communication, dealing with the actual physical connections and hardware involved in network infrastructure.
Key Security Challenges
- Unauthorized physical access to network devices
- Cable tapping and signal interception
- Hardware tampering and theft
- Electromagnetic interference and jamming
Protection Strategies
- Access Control Systems: Implement biometric scanners, key card systems, and multi-factor authentication for server rooms and network closets.
- Surveillance: Deploy CCTV cameras and motion sensors to monitor sensitive areas.
- Cable Protection: Use armored fiber optic cables and secure cable trays to prevent tapping.
- Hardware Security: Employ tamper-evident seals and regularly inspect devices for signs of tampering.
- Environmental Controls: Implement proper HVAC systems to prevent overheating and moisture damage.
Key Security Companies
- Honeywell (Access Control and Surveillance)
- Cisco (Physical Network Infrastructure)
- ADT (Physical Security Systems)
- Axis Communications (Network Cameras and Access Control)
Future Innovations
- AI-powered surveillance systems for anomaly detection
- Quantum-based physical layer security for unbreakable communication
- Self-healing materials for cable and hardware protection
2. Data Link Layer Security
The Data Link Layer manages communication between directly connected network nodes, handling data framing and error detection.
Key Security Challenges
- MAC address spoofing
- ARP poisoning attacks
- Rogue access points
- VLAN hopping
Protection Strategies
- Port Security: Configure switches to limit the number of MAC addresses per port.
- MAC Filtering: Implement whitelists of allowed MAC addresses on network switches.
- IEEE 802.1X: Deploy port-based Network Access Control (NAC) for authentication.
- DHCP Snooping: Prevent rogue DHCP servers from distributing malicious IP configurations.
- Private VLANs: Isolate hosts within the same VLAN to prevent lateral movement.
Key Security Companies
- Cisco (Switches with advanced security features)
- Juniper Networks (Network Access Control solutions)
- Aruba Networks (Secure wireless solutions)
- Extreme Networks (Fabric-based networking security)
Future Innovations
- AI-driven anomaly detection in Layer 2 traffic patterns
- Blockchain-based device authentication for IoT networks
- Self-configuring and self-healing Layer 2 networks
3. Network Layer Security
The Network Layer handles routing and addressing, making it crucial for controlling traffic flow and preventing unauthorized access.
Key Security Challenges
- IP spoofing
- DDoS attacks
- Routing table poisoning
- Packet sniffing
Protection Strategies
- Firewalls: Deploy next-generation firewalls (NGFW) with deep packet inspection capabilities.
- Intrusion Detection/Prevention Systems (IDS/IPS): Implement real-time traffic analysis and threat mitigation.
- Virtual Private Networks (VPN): Secure remote access and site-to-site connections with strong encryption.
- Access Control Lists (ACL): Configure routers to filter traffic based on predefined rules.
- Segmentation: Implement network segmentation and micro-segmentation to limit the blast radius of potential breaches.
Key Security Companies
- Palo Alto Networks (Next-generation firewalls)
- Fortinet (Unified threat management solutions)
- Check Point Software Technologies (Network security appliances)
- Zscaler (Cloud-based security)
Future Innovations
- AI-powered predictive threat intelligence
- Software-defined perimeter (SDP) for dynamic access control
- Quantum-resistant encryption for VPNs
4. Transport Layer Security
The Transport Layer ensures reliable data transfer between end systems, making it critical for securing communications.
Key Security Challenges
- SSL/TLS vulnerabilities
- TCP SYN flooding attacks
- Session hijacking
- Man-in-the-middle attacks
Protection Strategies
- Transport Layer Security (TLS): Implement the latest TLS protocols (TLS 1.3) for encrypted communications.
- Certificate Management: Use robust PKI systems and regularly rotate SSL/TLS certificates.
- TCP SYN Cookie: Enable SYN cookies on servers to mitigate SYN flood attacks.
- Connection Rate Limiting: Implement rate limiting to prevent connection exhaustion attacks.
Key Security Companies
- DigiCert (SSL/TLS certificates and management)
- Venafi (Machine identity protection)
- F5 Networks (Application delivery and security)
- Cloudflare (DDoS protection and SSL/TLS services)
Future Innovations
- Post-quantum cryptography for transport layer security
- AI-driven anomaly detection in encrypted traffic
- Decentralized PKI systems using blockchain technology
5. Session Layer Security
The Session Layer establishes, manages, and terminates connections between applications, making session security crucial for preventing unauthorized access.
Key Security Challenges
- Session hijacking
- Cross-site scripting (XSS) attacks
- Insufficient session timeout
- Session fixation
Protection Strategies
- Secure Session Handling: Implement strong session ID generation and management.
- Session Timeouts: Configure appropriate idle and absolute session timeouts.
- Session Encryption: Encrypt session data in transit and at rest.
- Multi-factor Authentication (MFA): Require additional authentication for sensitive actions or after periods of inactivity.
Key Security Companies
- Okta (Identity and access management)
- Auth0 (Authentication and authorization as a service)
- OneLogin (Unified access management)
- Ping Identity (Identity security solutions)
Future Innovations
- Continuous authentication using behavioral biometrics
- Decentralized identity management using blockchain
- Context-aware session management based on user behavior and environment
6. Presentation Layer Security
The Presentation Layer deals with data formatting and encryption, playing a crucial role in data privacy and integrity.
Key Security Challenges
- Data format vulnerabilities
- Insufficient encryption
- Compression-based attacks
- Encoding/decoding exploits
Protection Strategies
- Data Encryption: Implement strong encryption algorithms for data at rest and in transit.
- Input Validation: Rigorously validate and sanitize all input data to prevent injection attacks.
- Secure Data Serialization: Use secure methods for data serialization and deserialization.
- Format-Preserving Encryption: Employ FPE for sensitive data that needs to maintain its original format.
Key Security Companies
- Voltage Security (Data-centric security solutions)
- Thales (Encryption and key management)
- IBM Security (Data security and encryption)
- Microsoft (Azure Information Protection)
Future Innovations
- Homomorphic encryption for processing encrypted data
- AI-driven data classification and automatic encryption
- Quantum-resistant encryption algorithms
7. Application Layer Security
The Application Layer is where end-user services operate, making it a primary target for cyberattacks and a critical focus for security efforts.
Key Security Challenges
- SQL injection
- Cross-site scripting (XSS)
- Broken authentication
- Sensitive data exposure
- XML external entity (XXE) attacks
Protection Strategies
- Web Application Firewalls (WAF): Deploy WAFs to filter and monitor HTTP traffic.
- Secure Coding Practices: Implement and enforce secure coding guidelines and conduct regular code reviews.
- Regular Security Updates: Maintain a rigorous patching schedule for all applications and dependencies.
- API Security: Implement robust authentication, rate limiting, and input validation for APIs.
- Runtime Application Self-Protection (RASP): Deploy RASP solutions to detect and prevent attacks in real-time.
Key Security Companies
- Akamai (Web application and API protection)
- Imperva (Application security solutions)
- Veracode (Application security testing)
- Synopsys (Software composition analysis and security testing)
Future Innovations
- AI-powered application security testing and vulnerability prediction
- Serverless security solutions for cloud-native applications
- Automated patch generation and deployment using machine learning
Conclusion
Securing each layer of the network is crucial for businesses to protect against the ever-evolving landscape of cyber threats. By implementing a comprehensive, multi-layered security approach, organizations can significantly reduce their risk exposure and build resilience against potential attacks.
As we look to the future, emerging technologies like AI, machine learning, blockchain, and quantum computing are set to revolutionize network security. However, these same technologies may also be leveraged by malicious actors, creating new challenges and attack vectors.
To stay ahead in this constant arms race, businesses must remain vigilant, continuously updating their security strategies, and investing in the latest security innovations. By doing so, they can not only protect their assets and data but also gain a competitive advantage in an increasingly digital world.

