Security Vulnerabilities in SAML, OAuth 2.0, OpenID Connect, and JWT
Discover which SSO protocols put your enterprise at highest risk. This data-driven analysis compares authentication vulnerabilities across SAML, OAuth, OIDC, and JWT, with actionable mitigation strategies for security professionals.
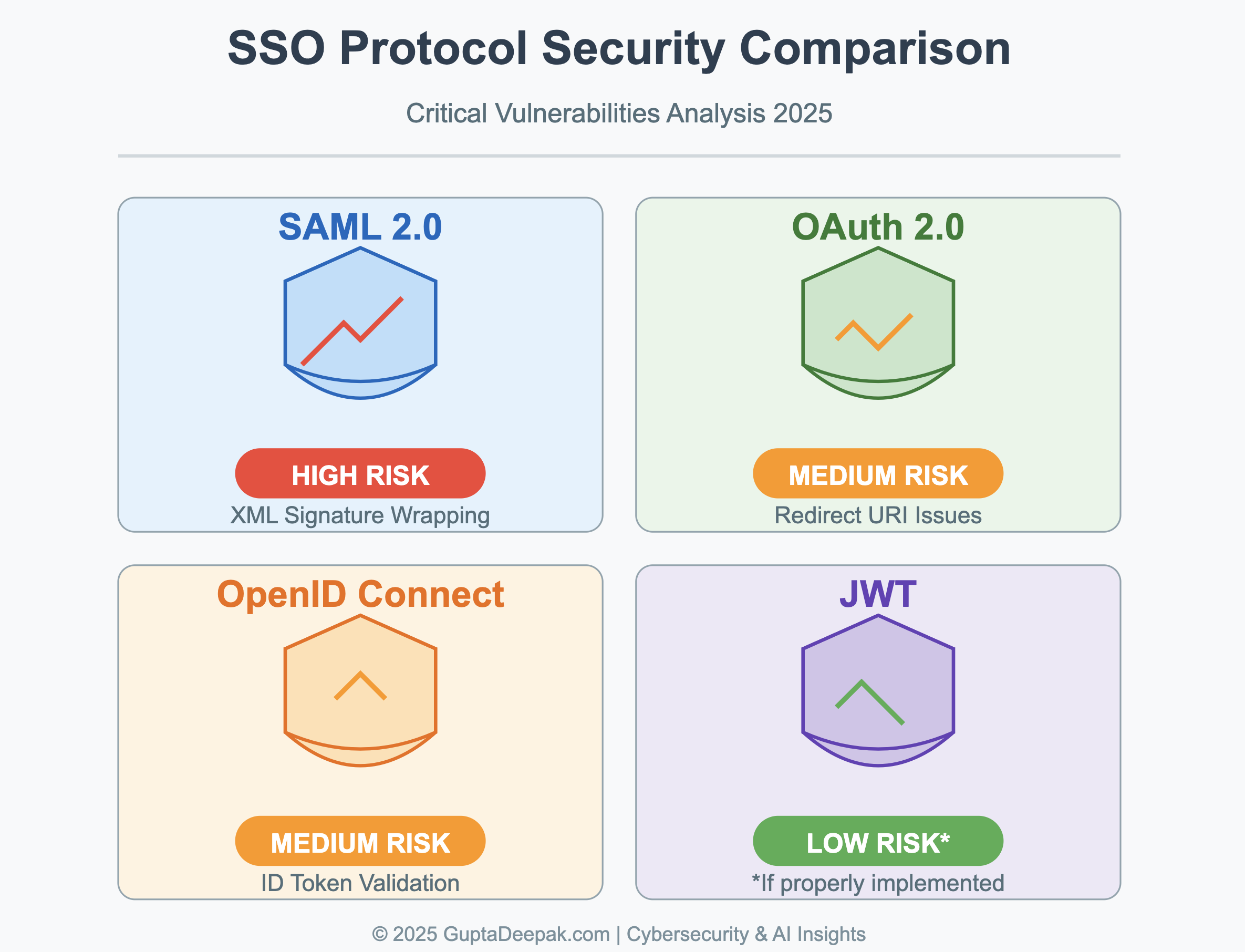
Single Sign-On (SSO) protocols are critical for enterprise security but have a history of severe vulnerabilities. This report provides a data-rich overview of known security flaws in four major SSO technologies – SAML, OAuth 2.0, OpenID Connect (OIDC), and JSON Web Tokens (JWT) – including both historical exploits and recent findings. We compare the frequency and impact of these vulnerabilities, and analyze how enterprise, cloud, and open-source implementations have responded. Links to CVEs, advisories, and authoritative research are included for direct reference.
Introduction and SSO Protocol Overview
Modern SSO protocols allow users to authenticate with one identity provider and gain access to multiple services. The most common standards are:
- Security Assertion Markup Language (SAML 2.0) – An XML-based framework for exchanging authentication and authorization data between an Identity Provider (IdP) and a Service Provider (SP). Widely used in enterprise web SSO and federation scenarios.
- OAuth 2.0 – An authorization framework (not strictly authentication) that permits third-party applications to obtain limited access to a web service (often issuing access tokens). It underpins many "Login with X" features and API auth schemes.
- OpenID Connect (OIDC) – An identity layer built on OAuth 2.0. OIDC issues ID Tokens (often as JWTs) in addition to OAuth access tokens, enabling client applications (relying parties) to verify user identity. Formal security analyses have generally found OIDC sound if implemented correctly.
- JSON Web Tokens (JWT) – A compact token format (JSON payload, signed/encrypted) used by OAuth/OIDC and other systems to represent claims. JWT is not a full protocol by itself, but its security is crucial to any SSO design that uses it for tokens.
Despite their widespread adoption, each of these has exhibited critical vulnerabilities. Implementation bugs and subtle design flaws have led to authentication bypasses, token forgeries, and account compromise. Below we catalog major known vulnerabilities for each protocol, from early exploits to 2024–2025 discoveries.
Security Vulnerabilities in SAML
SAML has been plagued by a series of high-impact vulnerabilities, largely due to the complexity of XML signature processing and token handling. Key vulnerability classes include XML signature wrapping, incorrect XML canonicalization, replay attacks, and flaws in specific SAML product implementations. Many of these allow an attacker to forge or alter SAML assertions and thereby impersonate users.
- XML Signature Wrapping (XSW) Attacks: This is the most infamous SAML flaw. First documented in the late 2000s, XSW exploits the flexibility of XML signatures. An attacker injects elements into a SAML response such that the IdP's signature still validates, but the SP interprets a different, unsigned portion as the asserted identity. Essentially, the attacker "wraps" a fake assertion around a valid signature. XSW vulnerabilities have reappeared repeatedly over the years. For example, in 2024, a critical bug (CVE-2024-45409) in the widely used Ruby SAML library allowed an attacker to log in as any user by forging a SAML response. This issue impacted platforms like GitLab and other Ruby-based SAML SPs. The recurring nature of XSW is highlighted by security researchers: "this attack keeps coming up again and again… affecting huge swaths of the internet". Recent CVEs related to XSW include CVE-2024-6202 (HaloITSM, critical SAML user impersonation) and CVE-2024-6800 (GitHub Enterprise Server, SAML SSO bypass).
- XML Canonicalization and Parser Bugs (2018 Multiple Libraries): In 2017–2018, researchers from Duo Security (Kelby Ludwig et al.) discovered a broad class of SAML implementation bugs affecting numerous open-source SAML toolkits. These libraries failed to properly handle certain XML structures (comments and DOM traversal), allowing portions of an unsigned SAML message to be interpreted as valid despite not being covered by the signature. The result was an authentication bypass – an attacker could modify SAML data after the signature, and the SP would still accept it as valid, logging in the attacker. CERT Coordination Center issued VU#475445 on this issue, and multiple CVEs were assigned across different SAML SDKs, including OneLogin's python-saml (CVE-2017-11427) and ruby-saml (CVE-2017-11428), the saml2-js library (CVE-2017-11429), OmniAuth SAML for Ruby (CVE-2017-11430), Shibboleth's OpenSAML in C++ (CVE-2018-0489), and others. These flaws were easy to exploit and had critical impact (authentication bypass). Vendors responded with patches in early 2018 once the issue became public, and advisories (e.g., from Shibboleth and others) urged immediate library updates. Okta's security team noted the attack "can be used to bypass authentication in a sinisterly simplistic way". (Notably, Okta itself was not vulnerable, as it did not use the affected libraries.)
- Assertion Replay / Missing Expiration Enforcement: Some SAML bugs involved failure to enforce token expiration or replay protections. For instance, CVE-2018-14637 was a flaw where a SAML SP ignored the expiration (
NotOnOrAfter) on SAML assertions, allowing an attacker to reuse an old SAML response (replay attack). While less complex than signature attacks, the impact (session hijacking) is still serious. Proper checking of SAML Conditions timestamps and one-time use of assertions (via<Assertion ID>or one-time tokens) is essential to mitigate replay. - Vendor-Specific Flaws: Enterprise SSO products built on SAML have had their share of issues. For example, Oracle Access Manager (an enterprise SSO/Federation server) suffered a critical vulnerability (CVE-2021-35587) that allowed unauthenticated remote takeover of the SSO system. Oracle's advisory doesn't detail the mechanics, but a CVSS 9.8 suggests a trivial exploit path, possibly an open endpoint that accepts malicious SAML or a default credential. Another example: Shibboleth's SAML SP software in 2023 had an SSRF (Server-Side Request Forgery) flaw in its XML parsing – a malicious
<KeyInfo>element in a SAML response could trick the SP into fetching external URLs. This SSRF bug (fixed in OpenSAML XMLTooling V3.2.4) could lead to DoS or be combined with other attacks. While not an auth bypass itself, it illustrates the ongoing hardening needed in XML-based SSO implementations.
Impact and Exploitability: SAML vulnerabilities are often high impact, typically allowing full authentication bypass – essentially letting an attacker impersonate arbitrary users at the service provider. For instance, the XSW flaw in Ruby SAML (CVE-2024-45409) was rated 9.8 Critical (network exploitable, no auth needed, complete compromise of confidentiality/integrity).
Exploit complexity varies: some attacks require the attacker to entice a user to visit a malicious IdP or interception of a SAML message, whereas others (like XSW) can be executed by directly crafting a SAML response if the SP will consume it (often the attacker needs a position to inject the response in the SSO flow). The XML-centric nature (XPath, XML DSig) means many vulnerabilities arise from subtle parsing logic – tough to spot in code, but once public, they are straightforward to exploit with off-the-shelf scripts.
Importantly, these issues keep recurring because the SAML spec is complex and "begs engineers to [make mistakes]" in validation logic. The frequency of critical SAML bugs has been significant: major waves in ~2012, 2018, and mid-2020s, plus sporadic CVEs in between. On the positive side, vendor response has become more responsive over time – after the 2018 CERT advisory, most library maintainers patched quickly (within days or weeks) and disseminated fixes.
However, fully eliminating XSW has proven difficult, as evidenced by its resurgence in 2024. Enterprise vendors now incorporate SAML patches into regular updates (e.g., Oracle's Critical Patch Updates) and cloud SSO providers closely audit their SAML flows (many have moved to OIDC/ OAuth tokens where possible to reduce XML attack surface).
Security Vulnerabilities in OAuth 2.0
OAuth 2.0 is an authorization framework, but its widespread use for login (via "OAuth dance" or as part of OIDC) means its security flaws can lead to account breaches and token leaks. The core OAuth 2.0 spec has known weaknesses (some design trade-offs), and many implementation bugs have been uncovered in OAuth deployments. Unlike SAML's cryptographic XML issues, OAuth vulnerabilities often involve logic and web security issues: open redirects, improper state parameter usage (CSRF), mis-validating redirect URIs, and insecure token handling. Below we summarize notable OAuth-related vulnerabilities:
- OAuth "Open Redirect" (Covert Redirect) Weakness: OAuth relies on redirecting users between the client (relying party) and authorization server. Attackers have long abused open redirectors on trusted domains to craft URLs that hijack OAuth flows. In 2014, a widely discussed issue named Covert Redirect showed how if a provider or client has a poorly validated
redirect_uri, an attacker could intercept the authorization code or token by redirecting to a malicious site. For example, an attacker could initiate an OAuth flow pointing toredirect_uri=http://attacker.com/authon a client that doesn't strictly validate the domain. After user login, the authorization server (e.g., Facebook) would redirect with the token/code to the attacker's domain. Many OAuth providers added stricter validation to mitigate this (requiring exact match redirect URIs or disallowing open redirects), but some third-party apps still misconfigure this. Research in 2023 found several major IdPs were vulnerable to redirect URI manipulations (path confusion or parameter pollution) that could be exploited to leak tokens. - CSRF and Lack of State Parameter: OAuth 2.0's implicit and authorization code flows are susceptible to cross-site request forgery on the client, potentially causing an OAuth login CSRF. The spec recommends a
stateparameter to carry a nonce, so the client can confirm the response is tied to the request. Yet many implementations historically forgot to use or verifystate. This led to real-world bugs where an attacker could trick a user into logging in to the attacker's account or otherwise misdirect the OAuth response. For instance, a HackerOne report described an OAuth client not validatingstate, allowing an attacker to craft a consent URL such that the victim, when logging in, gets logged into the attacker's session. Essentially, the victim's OAuth grant is hijacked to the attacker's account on the target service. This is a login CSRF – not a takeover of the victim's account, but rather a confusion attack that could be a stepping stone to other attacks (for example, linking the victim's social login to an attacker's account). Modern best practice is to always usestate(and in OIDC, also nonce) and many libraries enforce this, but older or custom OAuth clients may still be vulnerable if they ignorestate. - Authorization Code Interception (Without PKCE): OAuth's authorization code flow historically had an issue for native/mobile apps. Before the advent of PKCE (Proof Key for Code Exchange), if a native app used a custom URL scheme for redirect (e.g.,
myapp://callback), a malicious app on the device could register the same scheme and intercept the authorization code. The malicious app could then redeem that code to get the access token (essentially impersonating the legitimate app). This was a realistic threat on mobile platforms. PKCE (RFC 7636) mitigates it by binding the code to a code_challenge and verifier – the intercepted code alone is useless without the attacker also knowing the random verifier. PKCE became recommended for all clients (and is mandatory in OAuth 2.1). The vulnerability here was not a "bug" in OAuth per se, but a gap in the original design addressed by a later extension. Still, apps not implementing PKCE remained vulnerable to token theft via code interception until they upgraded. - Bearer Token Leakage (Implicit Flow and Otherwise): OAuth access tokens (and OIDC id_tokens) are often bearer tokens – any party that possesses the token can use it. The older implicit flow, where the access token is returned in the URL fragment, has been criticized for leaking tokens (e.g., through browser history, referer headers, or injected scripts). If an app served the access token in the redirect URL without
response_mode=form_post, it could end up in the browser address bar or logs. Attackers could steal tokens via XSS or sniffing network traffic if TLS is not enforced. Additionally, long-lived tokens or absence of TLS can turn any token interception into a full compromise. Modern guidance deprecates the implicit flow due to these risks. Even with authorization code flow, mismanagement of tokens on the client side (storing in localStorage vulnerable to XSS, not using HTTPS, etc.) can lead to leakage. These are more general web security issues but directly affect OAuth token security. - Ambiguities in JWT Profiles (spec vulnerability): OAuth 2.0 has optional mechanisms for client authentication and for passing tokens (JWT profiles, JAR, etc.). A recent formal analysis in 2025 identified a subtle vulnerability in how JWT audience values are used in OAuth/OIDC protocols. The issue, disclosed by the OpenID Foundation, is that the specification for private_key_jwt (an OAuth/OIDC client auth method using JWTs) had ambiguities that could potentially be exploited. It was assigned CVE-2025-27371 for OAuth 2.0's spec (and CVE-2025-27370 for the OpenID spec). While details are complex, it could allow an attacker to craft a JWT that an authorization server might accept illegitimately due to confusion about the audience claim. Notably, no known compromises occurred from this, as it was caught by researchers proactively. The OAuth and OpenID communities updated the specifications and certification tests to close this gap. This example shows the maturity of OAuth/OIDC: even spec flaws are now being formally checked and promptly addressed.
- Implementation-Specific Vulnerabilities: Numerous CVEs exist for specific OAuth implementations:
- OAuth Frameworks/Libraries: E.g., CVE-2025-31123 in Zitadel (open-source IdP) – it failed to check key expiration when using JWT for auth grants, allowing an attacker with an expired key to still obtain access tokens. Another example: a race condition in Duende Software's .NET OAuth token management (CVE-2025-26620) could mix up tokens between requests (a less common scenario).
- Vendor OAuth Services: While big providers (Google, Microsoft, etc.) seldom have publicly known CVEs, there have been logic bugs. For instance, Microsoft had a known issue where abusing MS OAuth endpoints in certain ways led to token injection (sometimes dubbed "OAuth 2.0 Mix-up" or similar, as reported in conferences).
- OAuth in Cloud Products: An example is CVE-2025-27672 in PrinterLogic (Vasion) which allowed an OAuth security bypass – likely an implementation bug where an attacker could skip the OAuth flow altogether.
Impact and Response: OAuth vulnerabilities can sometimes be as severe as SAML's (e.g., complete login bypass or token theft), but many are less direct. Often, an OAuth attack requires phishing or an open redirect to trick a user into granting access, whereas a SAML XSW can be exploited against a vulnerable SP in a single crafted response. Thus, exploitability is often medium – requiring user interaction or specific misconfigurations – and impact ranges from session hijacking to account impersonation. Still, critical cases exist (e.g., improper validation allowing straight token forgery is on par with SAML issues).
Frequency: logic flaws in OAuth integrations are discovered regularly by security researchers (often reported via bug bounty programs or academic papers). Many are unique to a particular service or library rather than systemic in the protocol.
Vendor response in the OAuth space is generally quick: cloud providers quietly fix issues in their authorization servers once reported. Open-source OAuth libraries (e.g., the Python oic library in CVE-2020-26244) also patch promptly when cryptographic flaws are reported. The OAuth 2.0 spec itself evolved (with PKCE, security BCPs) to mitigate earlier weaknesses. In summary, while OAuth's simpler design avoided XML-specific bugs, it has required constant vigilance for logic errors and evolved best practices to maintain security.
Security Vulnerabilities in OpenID Connect (OIDC)
OpenID Connect builds on OAuth 2.0, inheriting all the OAuth issues above, and adds its own ID token handling and discovery mechanisms, which have introduced additional vulnerabilities. The most critical OIDC-specific issues revolve around ID Token validation (or lack thereof) and IdP mix-up between multiple providers.
- Failure to Validate ID Token Signatures and Claims: OIDC's ID Token is a JWT that must be validated by the client (relying party). Mistakes in this validation have led to serious bugs. For example, the Python
oiclibrary (used for OIDC client implementations) had multiple vulnerabilities (CVE-2020-26244) where it did not automatically check the ID Token's signature algorithm ornoneusage, and could even return an ID token without verification. Specifically, this CVE enumerated: (1) the library did not verify the JWT'salgunless the calling code explicitly passed an expected algorithm; (2) it allowed thealg: none(no signature) token in all flows; (3) it returned ID tokens to the app without validating them, leaving it up to the implementer to call a separate verify function; (4) it didn't check theiat(issued-at) for sanity. Combined, these flaws could let an attacker provide a bogus ID token (unsigned or wrongly signed) that the client would accept – resulting in user impersonation. Many of these are essentially JWT issues manifesting in OIDC; similar bugs were seen in other languages or earlier libraries (e.g., an old Auth0 library version acceptedalg:nonetokens). Proper OIDC client implementations must verify the ID token's signature using the IdP's public keys, ensure theiss(issuer) andaud(audience) claims match the expected values, and enforce token freshness (expandiat). Any lapse in these checks is a potential critical vulnerability. - OIDC "Mix-Up" Attack: Discovered by researchers in 2017, the mix-up attack is a protocol-level vulnerability that can occur when a client (relying party) talks to multiple identity providers. An attacker could initiate an OIDC login with a malicious IdP and cause the client to mix up responses from a legitimate IdP vs. the attacker's IdP, potentially leading the client to accept an ID token from the attacker's IdP as if it came from the legitimate one. In practice, this attack is mitigated by the OIDC spec's requirement that clients check the
iss(issuer) in the ID token against the provider they intended to send the request to. Additionally, OIDC introduced aissparameter in the authorization response for cases where multiple IdPs might use the same redirect URI, and the client can also record which issuer it expected. The mix-up attack is more theoretical (no known widespread exploits in the wild after it was disclosed), but it underscores the importance of strict issuer validation and not assuming one IdP's token can be accepted in place of another. - Nonce and Session Fixation Issues: OIDC extends OAuth by using a
nonceparameter in authentication requests to bind the ID token to the session that initiated the request. If the nonce is not checked, an attacker might perform an ID token replay or a session fixation attack. A concrete case was CVE-2024-10318, a session fixation flaw in the NGINX OpenID Connect reference implementation. The IdP's response nonce wasn't being validated at the client, meaning an attacker could reuse a valid ID token (with a known nonce) to log in a victim or themselves as the victim on a target service. Essentially, an attacker could trick a user into accepting an ID token that wasn't actually freshly issued for that login. The fix was to properly verify the nonce value corresponds to the one sent in the OAuth/OIDC request. This type of bug is similar to not verifying the state parameter – it breaks the intended binding of responses to request origins. - Account Linking and Audience Confusion: Many applications allow logging in via multiple IdPs (Google, Facebook, enterprise IdP, etc.). Implementation oversights in how they link accounts can create vulnerabilities. For example, if an application doesn't properly distinguish ID tokens from different issuers, an attacker might be able to use an ID token from one context in another. OIDC's design expects that each client is configured per issuer, but misconfiguration could lead to accepting a token from a social provider where a corporate IdP token is expected (and vice versa). No specific CVE for this scenario, but it has been noted in penetration testing guides (always check the
issand client ID audience). The recent OpenID Foundation disclosure about ambiguous audience values in client-auth JWTs also hints at how confusion in token audience/issuer can introduce vulnerabilities if not tightly specified. - Discovery and Dynamic Client Registration Issues: OIDC has a discovery mechanism (metadata JSON documents) and dynamic client registration. Flaws in parsing discovery could lead to using a malicious IdP unintentionally. For instance, a vulnerability in XWiki's OIDC implementation (CVE-2022-39387) allowed a user to supply a custom OIDC provider in the request even if the wiki had a fixed IdP configured. This means an attacker could potentially use their own IdP to issue tokens that XWiki would trust (since it didn't enforce the configured provider), an obvious authentication bypass. Similarly, if an OIDC client erroneously trusts information from an unvalidated discovery URL, it could be pointed to a hostile IdP.
Impact and Response: OIDC vulnerabilities, when they occur, typically allow user impersonation or token theft, similar to OAuth. However, thanks to extensive formal security analysis (e.g., by researchers like Fett, Küsters, Schmitz in 2017), the core OIDC protocol is robust – many potential flaws were identified and addressed in the design. Most issues now arise in implementation.
The frequency of OIDC-specific CVEs is moderate; many issues reported are actually generic OAuth or JWT issues. When OIDC bugs do surface (like CVE-2020-26244 in a client library), they are patched swiftly given the security-conscious user base. Vendors of OIDC providers (e.g., cloud IdPs like Azure AD, Okta) usually fix things behind the scenes; open-source projects like mod_auth_openidc or IdentityServer also have good track records of prompt fixes.
For example, the NGINX OIDC nonce bug (CVE-2024-10318) was fixed by November 2024 with an update to the module. The OpenID Foundation's coordinated disclosure in 2025 of spec ambiguities, with no known compromises, demonstrates a proactive approach. In summary, OIDC's additional ID token layer adds some complexity (and thus a few new vulnerability avenues), but also provides more explicit security features (issuer, audience, nonce) that, when used correctly, greatly limit attacks.
Security Vulnerabilities in JSON Web Tokens (JWT)
While not an SSO protocol by itself, JWT is integral to OAuth2/OIDC (and even used in some SAML token exchanges as an alternative format). JWTs have had their own share of vulnerabilities, primarily due to issues in how libraries validate tokens. The two most notorious bugs in JWT implementations are the "alg:none" attack and signature verification algorithm confusion:
- "alg": "none" (Unauthenticated JWTs): The JWT standard defines an
algheader that specifies the signing algorithm, and it includes"none"as a valid value (meaning the token is unsecured). This was intended only for scenarios where the token's integrity is guaranteed by external means, but early JWT libraries mistakenly treatedalg:"none"as if it were a valid signature method even when a secret/key was expected. In 2015, researchers showed that in several libraries, if an attacker changed the JWT header to"alg": "none"and removed the signature, the library would accept the token as valid. Result: the attacker could modify the payload freely (e.g., set"admin": trueor change the user ID) and the server would trust it, effectively bypassing authentication or authorization. This vulnerability was extremely easy to exploit (just tweak a JWT with base64 decoding/encoding) and catastrophic in impact (authentication bypass). It was documented under CVE-2015-2951 (for JOSE4J library in Java) and other identifiers, and was widely publicized by the Auth0 security team. Fortunately, most implementations quickly added a check to disallownoneunless explicitly configured. As the Auth0 report noted, "most (hopefully all?) implementations now prevent this attack" by requiring a no-key scenario fornoneor disallowing it entirely. - HMAC-Signature Confusion (Public Key as Secret): JWT supports both symmetric (HMAC, e.g. HS256) and asymmetric (RSA/ECDSA, e.g. RS256) algorithms. In 2015, it was found that some libraries didn't properly handle tokens that used a different algorithm than expected. If a server was using an RSA public/private key pair (RS256) to verify tokens, an attacker could submit a token with header
"alg": "HS256"and reuse the server's public key as the HMAC secret key. A vulnerable server would attempt to verify the HMAC using what it thinks is the secret – but it's actually the public key provided (since it mistakenly believes the token is now using a symmetric key). Because the attacker also knows the public key (it's public), they can sign the token with that key (as HMAC secret) and the server will accept it. In other words, the server interprets the public key as a shared secret, which the attacker also possesses. This allows forging an arbitrary token that passes verification. This flaw is essentially a failure to enforce algorithm consistency – the server should know it only expects RS256 tokens and reject ones claiming HS256, but if it doesn't, the attacker can confuse it. Like thealg:noneissue, this was addressed by libraries adding explicit algorithm whitelisting or requiring the application to specify expected alg. The recommended fix is for the verify function to not trust the token's alg header and instead use server-side configuration. CVE-2016-10555 was assigned for one implementation of this bug (in a Node.js library), and generally multiple libraries were patched around 2015–2016 to fix it. - Key Management and Injection Flaws: Other JWT-related vulnerabilities include mistakes in key parsing or
kid(Key ID) handling. For instance, if an application allows an attacker to supply their own public key and the server doesn't properly validate the token'skid, the attacker could trick the server into using a wrong key to verify. There have been CVEs (e.g., CVE-2018-1000531 mentioned in a JWT security analysis) where JWT libraries were too lenient in accepting keys or algorithms, leading to forgery. Another issue can be alg downgrade attacks in systems that accept multiple algs: if not careful, an attacker could get the system to use a weaker alg (though modern libraries typically tie a key to one algorithm). - JWT Replay and Storage Weaknesses: Even when JWTs are correctly validated, misuse can lead to vulnerabilities. For example, not all systems properly manage JWT revocation or expiration. If a JWT (especially a long-lived one like a refresh token or an OIDC id_token meant for one-time use) is captured by an attacker, they can reuse it until it expires. Some enterprise SSO solutions had issues where logout did not invalidate existing JWTs or where the same JWT could be used across applications not intended to share sessions. These aren't CVE-level bugs in JWT itself but design issues that security architects must consider (e.g., audience restrictions, short token lifespans, token binding to client IP or context, etc., to limit replay value).
Impact and Response: The critical JWT implementation bugs (alg confusion) were extremely impactful – effectively allowing an attacker to become any user – but those were largely handled in 2015–2016.
The frequency of new JWT-specific CVEs has dropped as libraries matured. One notable later issue was the Python OIDC CVE-2020-26244 we described, which again was about not enforcing alg and accepting none – essentially a re-emergence of past mistakes in a less popular library. This indicates that new or niche implementations might still make these mistakes if they aren't using well-known libraries.
Exploitability of JWT flaws is typically trivial once a vulnerable library is identified (for alg:none or key confusion, it's just crafting a token). On the flip side, if libraries are up-to-date, JWTs are secure by design (using strong cryptography like RS256 or ES256).
Vendor response time for JWT bugs has been good, in part because the vulnerability is usually in a self-contained library – maintainers can patch the library and all downstream applications that update will be secured. For example, when Auth0's team discovered the original issues, they provided patches or guidance and most major JWT libraries integrated those checks.
Developers and security teams today are generally aware of JWT risks; there are OWASP cheat sheets and tooling to test JWT handling. It's worth noting that JWT usage spans enterprise, cloud, and open-source: e.g., Microsoft's Azure AD issues JWTs for OIDC, open-source projects like Keycloak use JWTs, etc. Ensuring consistency in validation across these is crucial. Misconfigurations (like not pinning expected algorithm, or failing to rotate secrets) remain a potential weak link.
Comparative Analysis and Discussion
In this section, we compare the four technologies across several dimensions – frequency of vulnerabilities, ease of exploitation, typical impact severity, and how different vendor types respond. The following table summarizes the comparison:
| Protocol | Common Vulnerability Types | Notable CVEs / Incidents | Frequency & Recent Trend | Exploitability | Impact | Vendor Response |
|---|---|---|---|---|---|---|
| SAML 2.0 | – XML Signature Wrapping (XSW) attacks<br>– XML canonicalization & parsing bugs<br>– Replay of assertions (missing expiration checks)<br>– Implementation logic flaws (SSRF, injection) | CVE-2017-11427…11430 (multi-library auth bypass);<br>CVE-2018-7644 (SimpleSAMLphp signature verification bypass);<br>CVE-2024-45409 (Ruby SAML, login as arbitrary user);<br>CVE-2024-6202 (HaloITSM, XSW user impersonation);<br>CVE-2021-35587 (Oracle Access Manager, takeover) | Historically high volume of critical vulns. Big waves in 2012, 2018, 2024. Recent trend: XSW resurfacing in 2023–24 across languages. Continual patching needed; spec complexity means new variants keep appearing. | Many SAML bugs are easy to exploit once known – e.g., crafting an XML with a forged assertion. Attacker often needs ability to feed a fake SAML response to SP (via user's browser or a malicious IdP). Requires knowledge of SP's SAML endpoint, but tools are available. | Critical – Typically full authentication bypass (impersonation of any user). Attackers can gain unauthorized access to applications as legitimate users, including admin accounts, without credentials. Replay issues allow session hijack. Some bugs (SSRF) lower impact, but most affect authentication directly. | Enterprise vendors issue patches in security advisories (e.g., Shibboleth, Oracle) and many moved to safer defaults (e.g., requiring signed entire response). After 2018's disclosures, open-source libs were patched promptly. Cloud SAML (e.g., Google, Azure) remained largely unaffected by those library bugs or patched internally (some have shifted emphasis to OIDC). However, SAML being older means some deployments run legacy versions – upgrades can lag, leaving long-tail risk. |
| OAuth 2.0 | – Open redirect and improper redirect_uri validation<br>– Missing/weak state parameter (CSRF)<br>– Implicit flow token exposure<br>– Misuse of OAuth flows (e.g., using public clients without PKCE)<br>– Spec ambiguities in JWT profiles | "Covert Redirect" (not a single CVE, but widely reported issue in 2014);<br>CVE-2025-27371 (JWT audience ambiguity in OAuth spec);<br>CVE-2025-31123 (Zitadel, expired key allows token issuance);<br>CVE-2025-27672 (PrinterLogic, OAuth bypass); <br>CVE-2019-9837 (Doorkeeper OIDC, open redirect via redirect_uri) | Steady stream of medium-severity findings. Recent trend: focus on securing redirect URIs, PKCE now standard, formal analysis of spec in 2025 found rare flaw (fixed in spec). Fewer critical universal flaws than SAML; issues often specific to implementers. | Moderate – Many attacks require tricking a user (social engineering) or exploiting a misconfig on the client side. For example, open redirect attacks require a user to click a crafted link. Attack complexity can be low if the target app is misconfigured (then attacker just crafts a URL), but overall more steps than injecting a single malicious token. | Ranges from High to Moderate. Worst-case (like spec flaw or a token forgery bug) can allow account takeover (stealing tokens to access user data). Many OAuth bugs lead to token leakage or unintended login, which are serious but often need chaining of actions. The impact can be limited by scope – e.g., stealing an access token for one app might not compromise others. | OAuth providers (Google, Facebook, etc.) respond quickly to security reports, often fixing quietly. Open-source projects (e.g., OAuth libraries) also tend to patch fast due to broad use. The OpenID/OAuth community actively updates recommendations (PKCE, threat mitigations) – e.g., OAuth 2.1 draft formalizes many security best practices. Enterprise products include OAuth fixes in routine updates (e.g., IBM, Oracle include in quarterly patches). Because OAuth issues often involve multiple parties (IdP, RP), coordination and clear communication (CERT bulletins, etc.) happen for bigger vulnerabilities. |
| OpenID Connect | – ID token validation flaws (signature, issuer, audience, nonce)<br>– OIDC "mix-up" attack between multiple IdPs<br>– Insecure dynamic client registration or discovery<br>– Libraries inheriting OAuth issues (state, redirect) | CVE-2020-26244 (Python OIDC lib, multiple ID token verification flaws);<br>CVE-2024-10318 (NGINX OIDC, nonce not checked – session fixation);<br>CVE-2022-39387 (XWiki OIDC, use of rogue IdP via request params);<br>CVE-2023-24424 (Jenkins OIDC plugin, session not invalidated – session fixation);<br>CVE-2025-27370 (OIDC spec private_key_jwt vulnerability) | OIDC itself is newer; frequency of fundamental flaws is low (benefited from formal security proofs). Implementation issues still arise, often similar to OAuth's. Recent trend: ensuring libraries properly enforce nonce, alg, issuer checks (e.g., 2020 and 2024 CVEs above). Also, ecosystem addressing spec-level issue in Federation in 2025 before it caused harm. | Moderate, akin to OAuth. Exploiting OIDC often means exploiting the client's validation: e.g., attacker must supply a crafted ID token or manipulate the flow (requires some access or trickery). If an RP is misconfigured to trust the wrong IdP, that's easy to exploit (just use your own IdP). If a library fails to verify signature, an attacker crafts a token – trivial if you know the flaw. Mix-up attacks are complex and largely theoretical with modern mitigations. | When an OIDC validation bug exists, impact is Critical – e.g., forging an ID token lets attacker log in as any user (full account takeover). If only a nonce check is skipped, impact can be session fixation (attacker replaying a login response), which can also lead to impersonation in certain contexts. Many OIDC issues ultimately result in impersonation or authentication bypass, matching the severity of SAML/OAuth. | OIDC providers (Azure AD, Okta, etc.) quickly patch server-side issues – often before public disclosure. OpenID Foundation oversees the standard's security: the 2025 spec vulnerability was handled by updating specs/tests rapidly. Open-source OIDC libraries, when alerted (as with the Python one), issue fixes and security advisories. In enterprise products (e.g., those supporting OIDC login), OIDC bugs are addressed in regular security updates. The community is quite proactive – e.g., collaboration with academics for formal analysis. Overall, response times have been good and there's an emphasis on backwards-compatible security improvements (like requiring nonce, recommending library default checks) to prevent common mistakes. |
| JWT (Token) | – alg: none acceptance (no signature check)<br>– Algorithm confusion (e.g., RSA vs HMAC as in HS256/RS256 mixup)<br>– Weak token encryption or no integrity check in some modes<br>– Poor token storage or reuse (replay issues) |
CVE-2015-2951 (JWT alg=none, JWT.io library);<br>CVE-2016-10555 (JWT HS256 public key confusion in node-jwt-simple);<br>CVE-2017-12979 (JOSE library in C, alg none) – as referenced by research;<br>CVE-2018-1000531 (Java JWT, insecure key parsing);<br>CVE-2020-15957 (Go JWT lib, alg none) – indicating issues persisted in some libs. | Most critical JWT bugs were found around 2015–2017 when JWT usage surged. Frequency now is low; core libraries are stable. Occasional new CVEs when a new library or edge scenario is looked at (e.g., Python OIDC lib in 2020). As JWT is ubiquitous, any new flaw is quickly publicized. | Easy if vulnerability present – crafting JWTs is straightforward with tools, and no special position needed (attacker just sends the fake token to the server). If no flaw, then JWTs are as hard to forge as the crypto (practically impossible). So it's feast or famine: either completely insecure (to anyone with a laptop) or secure. | In vulnerable cases, Critical – complete authz/auth bypass (forging tokens with any claims). For example, with alg=none, an attacker could become an admin by modifying the token payload. With key confusion, any user could impersonate others. If JWTs are properly validated, impact then depends on other factors (the token's privileges, lifespan) – a stolen but valid JWT might have time-limited impact. | Library maintainers responded rapidly circa 2015 once exploits were demoed. Today, popular JWT libraries explicitly prevent using "none" or mixing algs incorrectly. Vendors that build on JWT (cloud APIs, etc.) also implemented checks. For instance, Auth0 improved their JWT libraries' API to require specifying expected algorithms. Overall, the JWT community learned from early mistakes; updates and advisories were rolled out within days in many cases. One challenge is propagation – enterprise apps might use outdated libraries. But awareness is high: many security scans and pen-tests specifically look for JWT issues now, and devs are quick to apply patches given the severity. |
Enterprise vs. Cloud vs. Open-Source
It's useful to distinguish how different environments handle these vulnerabilities:
Enterprise Software
Traditional on-premises SSO solutions (Oracle, IBM, CA SiteMinder, Microsoft ADFS, etc.) bundle SSO protocol support. They have had severe issues (e.g., Oracle Access Manager CVE-2021-35587, older ADFS "golden SAML" token forgery when token-signing cert stolen).
Enterprise vendors usually patch via scheduled Critical Patch Updates or Security Bulletins. The response time can vary: if an issue is public (like the 2018 SAML bug), vendors aim to patch fast. Oracle and IBM issued fixes for the SAML library issues in their products shortly after the CERT bulletin. A challenge is that enterprise customers must apply patches – if they delay, systems remain vulnerable. Enterprise implementations often have robust security teams, but also longer deployment lifecycles, meaning some older versions with known flaws might persist in the wild.
Cloud Services (SSO as a Service)
Cloud identity providers (Okta, Azure AD, Google Identity, AWS Cognito, etc.) can usually fix vulnerabilities on their end transparently. For example, when OAuth redirect flaws have been identified, Google tightened their allowed redirect URI patterns server-side. Azure AD, after incidents of token misuse, rolled out features like continuous access evaluation and stricter JWT validation.
OneLogin's 2017 breach (while not a protocol flaw, but an incident where decryption keys were stolen) highlighted that even cloud SSO is not immune to compromise. Cloud vendors tend not to have CVEs since they're not software distributed to users; instead, they publish security advisories or blog posts. Their response tends to be quick and decisive, often working with researchers under NDA until fixed. The down side is less transparency – we often hear of issues only through talks or brief notes rather than CVEs.
Open-Source Solutions
These include libraries (e.g., passport.js for Node OAuth, Spring Security SAML for Java) and full products (Shibboleth, Keycloak, etc.). Open-source projects rely on the community or academics to find bugs, but they also benefit from it – many of the vulnerabilities we discussed (SAML XSW, JWT bugs) were found by researchers and quickly communicated. For instance, Shibboleth's team has been exemplary in handling reports: the 2023 SSRF fix and previous SAML issues were addressed with clear advisories and patched versions.
Open-source libraries like SimpleSAMLphp, OneLogin's toolkits, etc., patched the 2018 SAML vulns promptly and issued public guidance. One challenge in open source is coordination – a flaw in a widely used library can affect dozens of products (as seen in SAML and JWT cases). CERT bulletins (like VU#475445) help coordinate here, listing all affected projects. The community nature also means open-source solutions often adopt preventive measures quickly – e.g., after JWT issues, almost all libraries added stricter defaults. The frequency of discoveries in open source might seem higher (because of transparency), but that also means issues get fixed before attackers exploit them widely.
Conclusion
SSO protocols have proven to be both indispensable and at times vulnerable. SAML's rich but complex XML framework has yielded multiple critical vulnerabilities over the years, whereas OAuth/OIDC, while simpler and benefiting from iterative improvements, have had their share of logic and implementation flaws. JWT, as a cornerstone of token-based auth, had early growing pains with serious security bugs that are now largely resolved in mature libraries.
For security professionals and decision-makers, the key takeaways are:
- Stay Updated: Keep SSO software and libraries up to date. Many high-impact vulnerabilities (across SAML, OAuth, OIDC, JWT) are fixed in recent versions – e.g., upgrading SAML libraries post-2018 patches, using OAuth 2.1/PKCE, ensuring JWT libraries from 2016 onward.
- Defense in Depth: Use protocol features as intended – enforce signature validation, use state and nonce, restrict redirect URIs, short token lifetimes, etc. Many exploits succeeded because optional security measures were not implemented.
- Monitor Advisories: Subscribe to CERT, vendor bulletins, and the OpenID Foundation announcements. The OpenID Foundation's 2025 disclosure is an example of heads-up communication about spec-level issues. Vendors like Microsoft, Oracle, IBM, and open-source communities (Shibboleth, OAuth.net) regularly publish security notices.
- Incident Response and Hardening: Plan for the worst – e.g., token theft can happen, so design least-privilege scopes and the ability to revoke tokens. In SAML, protect your IdP's signing keys (as the "Golden SAML" attack shows – if attackers get your cert, they can mint valid SAML for any user). Consider moving to or adding OIDC/OAuth flows which have less XML attack surface, if feasible, or use modern SAML profiles that limit complex features.
- Comparative Risk: Recognize that while SAML has a history of more frequent critical flaws, a well-hardened SAML deployment can be very secure – and conversely, a poorly implemented OAuth client can be phished easily. No protocol is magically safe; implementation quality and prompt patching are paramount. OIDC, being built on lessons from SAML and OAuth, strikes a good balance but still demands correct usage of its features.
In conclusion, the state of SSO protocol security in 2025 is one of improved resilience but constant vigilance. The community has responded to past failures with stronger standards and quicker patch pipelines. By keeping abreast of vulnerability disclosures (from historical CVEs to emerging research) and proactively applying mitigations, organizations can confidently leverage SSO benefits without undue risk. The collaborative efforts of vendors, open-source maintainers, and researchers are steadily raising the bar, making the SSO ecosystem safer for everyone.

